Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Por um escritor misterioso
Last updated 22 março 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.

Cyber Policy, Doctrine, and Tactics, Techniques, and Procedures

TTPs Within Cyber Threat Intelligence

TTPs Within Cyber Threat Intelligence

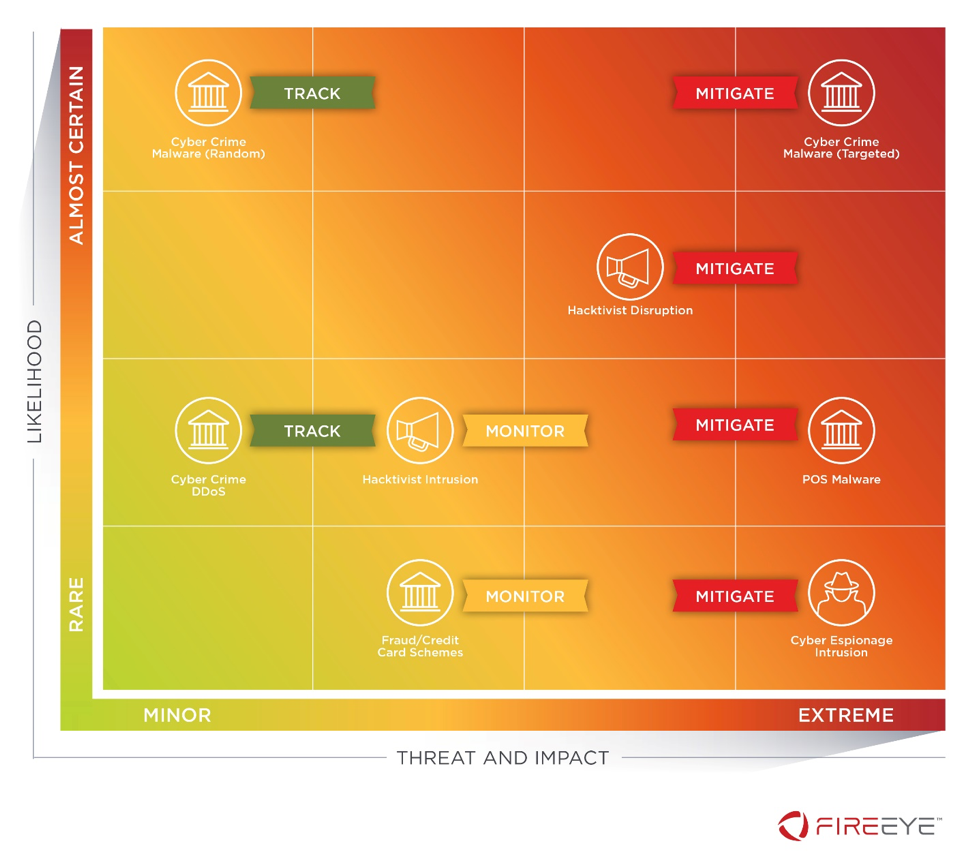
Techniques Tactics Procedures Utilized by Fireeye Red Team Tools
Operationalizing CTI: Using MITRE ATT&CK to Hunt for and Defend
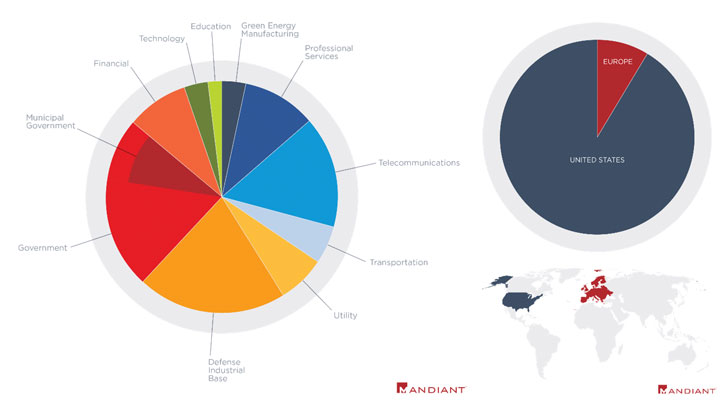
Chinese Cyber Espionage Hackers Continue to Target Pulse Secure

Tactics, Techniques and Procedures of FireEye Red Team Tools
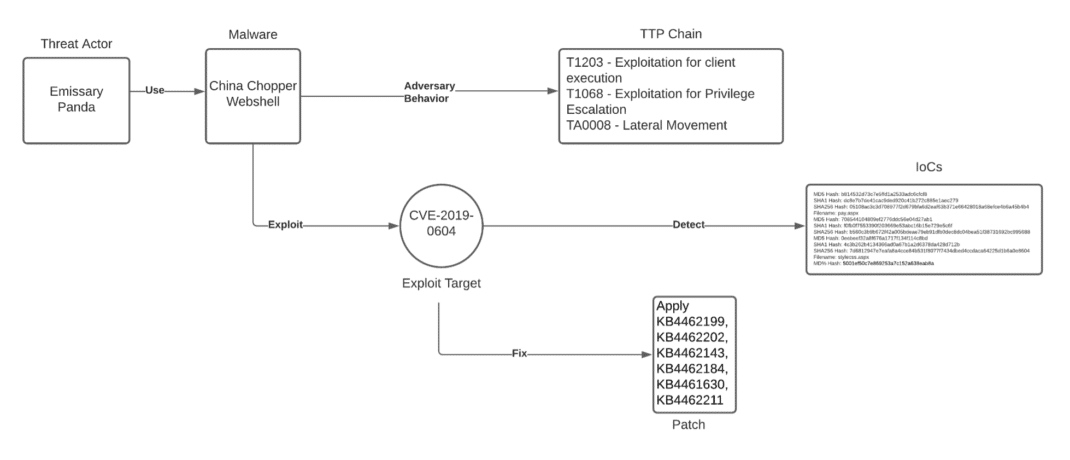
Unpacking the CVEs in the FireEye Breach - Start Here First
Hackers' Favourite Scripting Languages Part 2: Offensive and

Tactics, Techniques and Procedures of FireEye Red Team Tools

Inside the Mind of a Cyber Attacker

Defending CI/CD Environments - The NSA/CISA Way
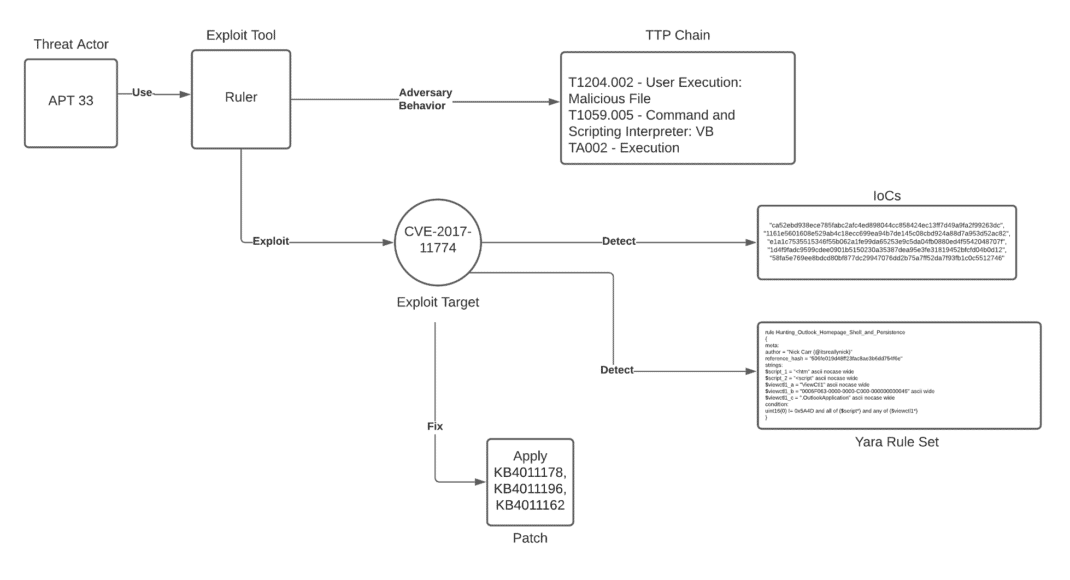
Unpacking the CVEs in the FireEye Breach - Start Here First

FireEye Endpoint Security Leads MITRE ATT&CK Evaluation
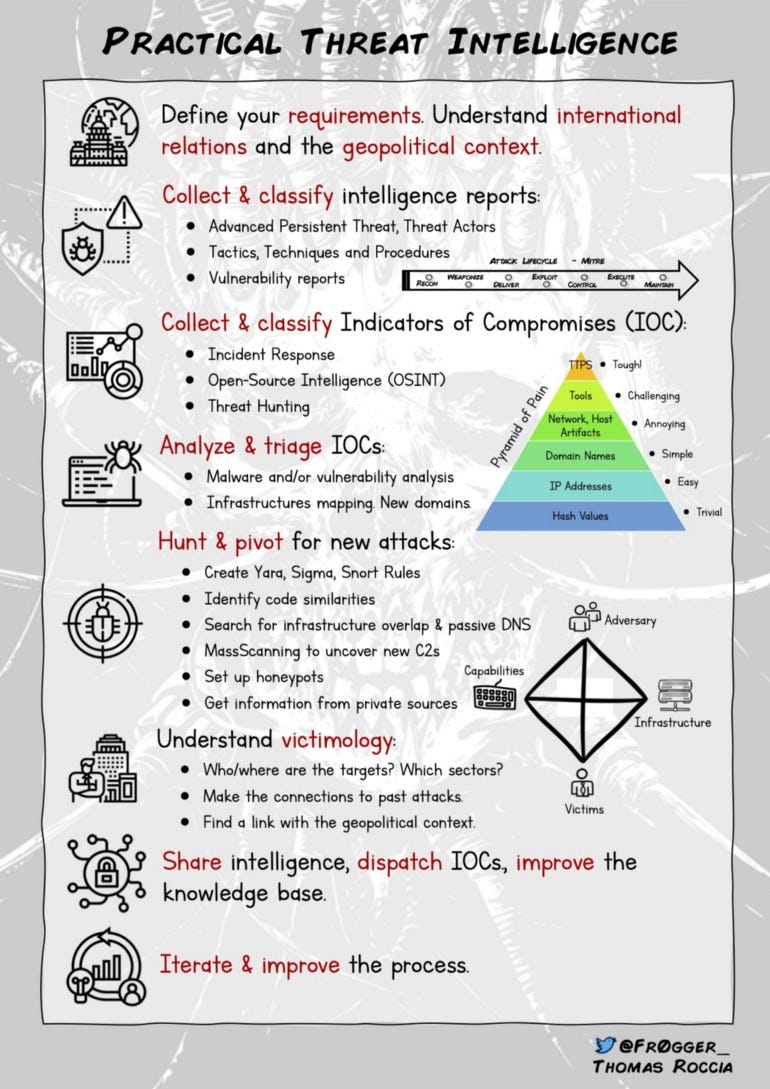
Security Infographics. I often do infographics to share…
Recomendado para você
-
GitHub - SonsoFsERpent/redEngine-Spoofer: With the redENGINE22 março 2025
-
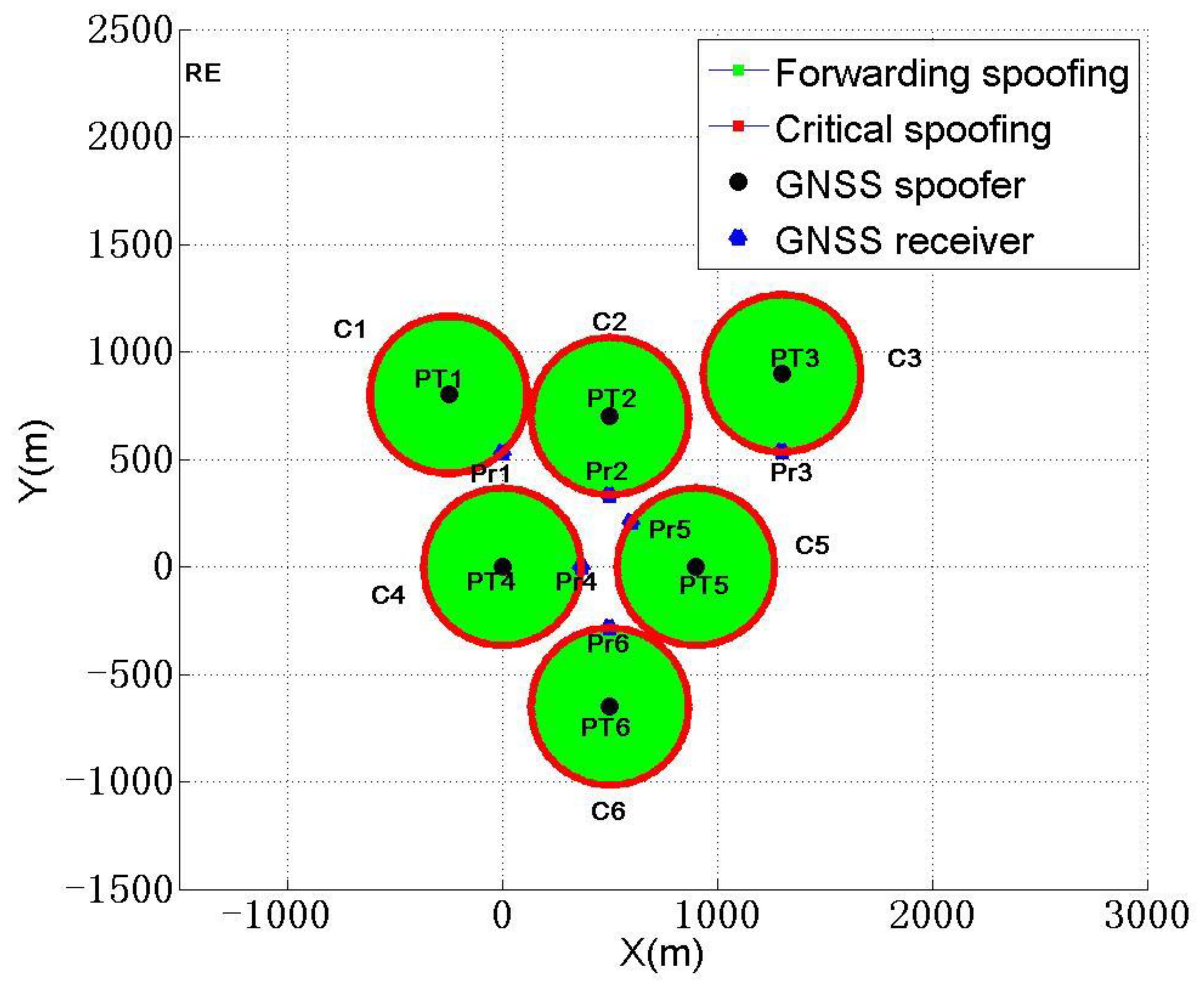 Sensors, Free Full-Text22 março 2025
Sensors, Free Full-Text22 março 2025 -
hwid-spoofer · GitHub Topics · GitHub22 março 2025
-
RoDAR the Equaliser22 março 2025
-
Eulen or redengine? #cheating #eulen #fivem #jus2rich #gaming22 março 2025
-
Cracked Hwid Spoofer22 março 2025
-
 How Do MAC Spoofing Attacks Work?22 março 2025
How Do MAC Spoofing Attacks Work?22 março 2025 -
HookSpoofer: The Modified Open Source Stealer Bundlers Making the Rounds22 março 2025
-
 GitHub - p2geedn7/redEngine: RedENGINE is the Best LUA Executor22 março 2025
GitHub - p2geedn7/redEngine: RedENGINE is the Best LUA Executor22 março 2025 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools22 março 2025
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools22 março 2025
você pode gostar
-
 Unraveling Intrigue: A Thrilling Journey into B: The Beginning Anime – Pinned Up Ink22 março 2025
Unraveling Intrigue: A Thrilling Journey into B: The Beginning Anime – Pinned Up Ink22 março 2025 -
 and now gg roblox Archives - freegenerter.eu22 março 2025
and now gg roblox Archives - freegenerter.eu22 março 2025 -
 closed. — Lucy Hale GIF hunt directory22 março 2025
closed. — Lucy Hale GIF hunt directory22 março 2025 -
PROYECTO KONOBI! CAPITULO 1 PARTE 1 Porfin! despues de tanta preparacion eh aqui la primera parte de nuestro proyecto fandub, espero que lo disfrutes y que lo compartas con tus amigos!!22 março 2025
-
 Cavaleiros do Zodíaco - Cavaleiros do Zodiaco Saint Seya Batalha das 12 Casas #122 março 2025
Cavaleiros do Zodíaco - Cavaleiros do Zodiaco Saint Seya Batalha das 12 Casas #122 março 2025 -
 O brasileiro é um dos que mais jogam o Dinossauro do Chrome22 março 2025
O brasileiro é um dos que mais jogam o Dinossauro do Chrome22 março 2025 -
 KIT Baralho Cigano Lenormand 36 Cartas + Athame Dourado - META22 março 2025
KIT Baralho Cigano Lenormand 36 Cartas + Athame Dourado - META22 março 2025 -
 Crítica Assassinos da Lua das Flores22 março 2025
Crítica Assassinos da Lua das Flores22 março 2025 -
 SAIU 14 MEGA CÓDIGOS *FUNCIONANDO* NO KING LEGACY22 março 2025
SAIU 14 MEGA CÓDIGOS *FUNCIONANDO* NO KING LEGACY22 março 2025 -
 Game maze runner wheels22 março 2025
Game maze runner wheels22 março 2025


