Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 02 abril 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
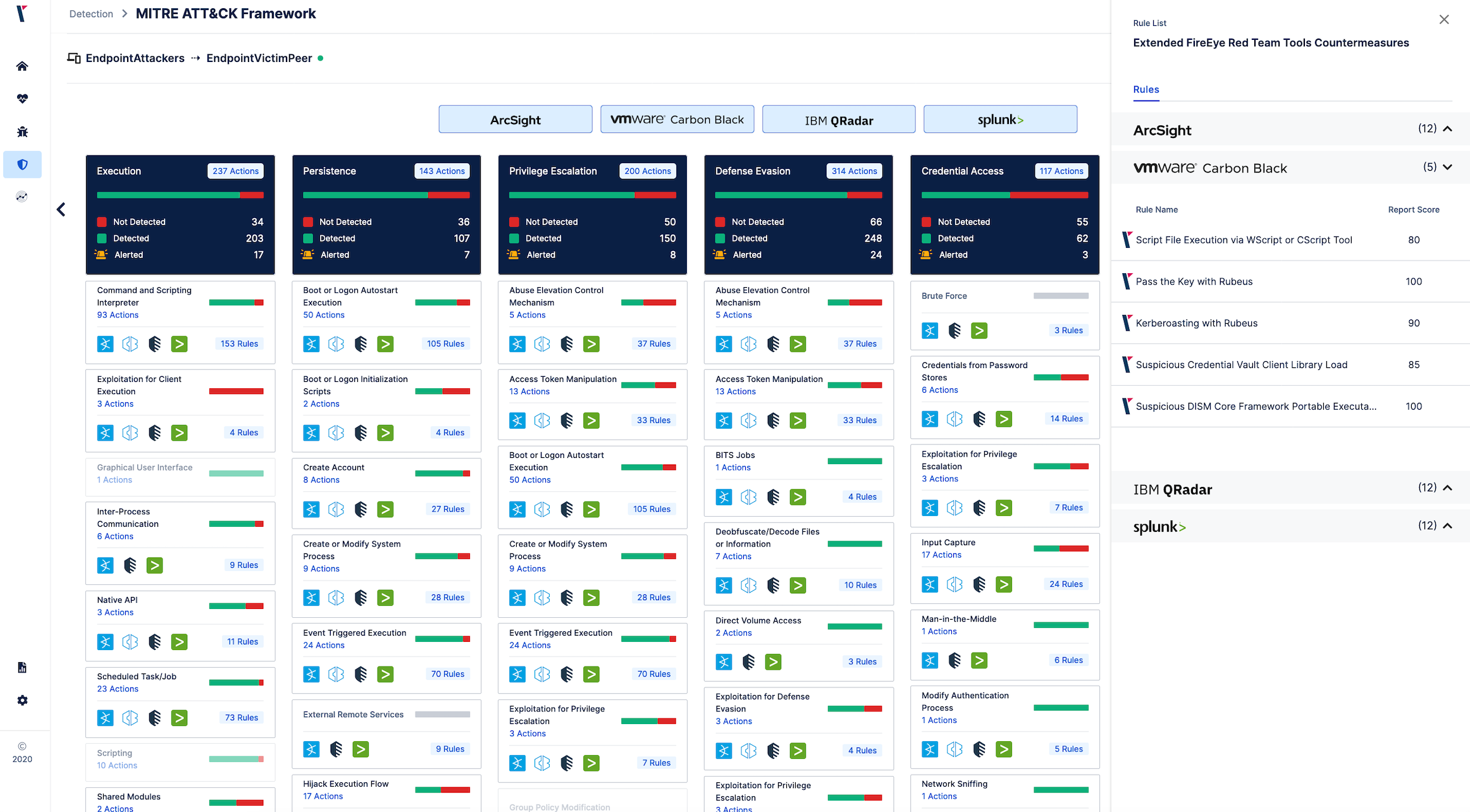
It is Time to Take Action - How to Defend Against FireEye's Red

Adversary Emulation and Red Team Exercises - EDUCAUSE
Hackers' Favourite Scripting Languages Part 2: Offensive and
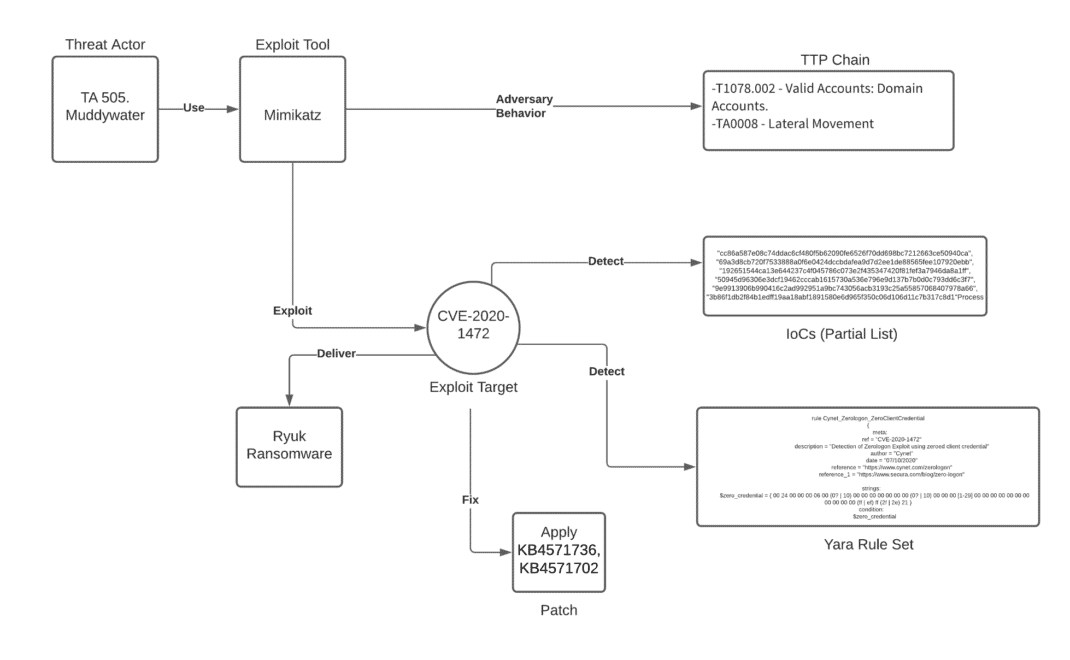
Unpacking the CVEs in the FireEye Breach - Start Here First

The Stolen FireEye Red Team Tools Are Mostly Open Source

Stamus ND/NDR is Armed to Detect Stolen FireEye Red Team Tools
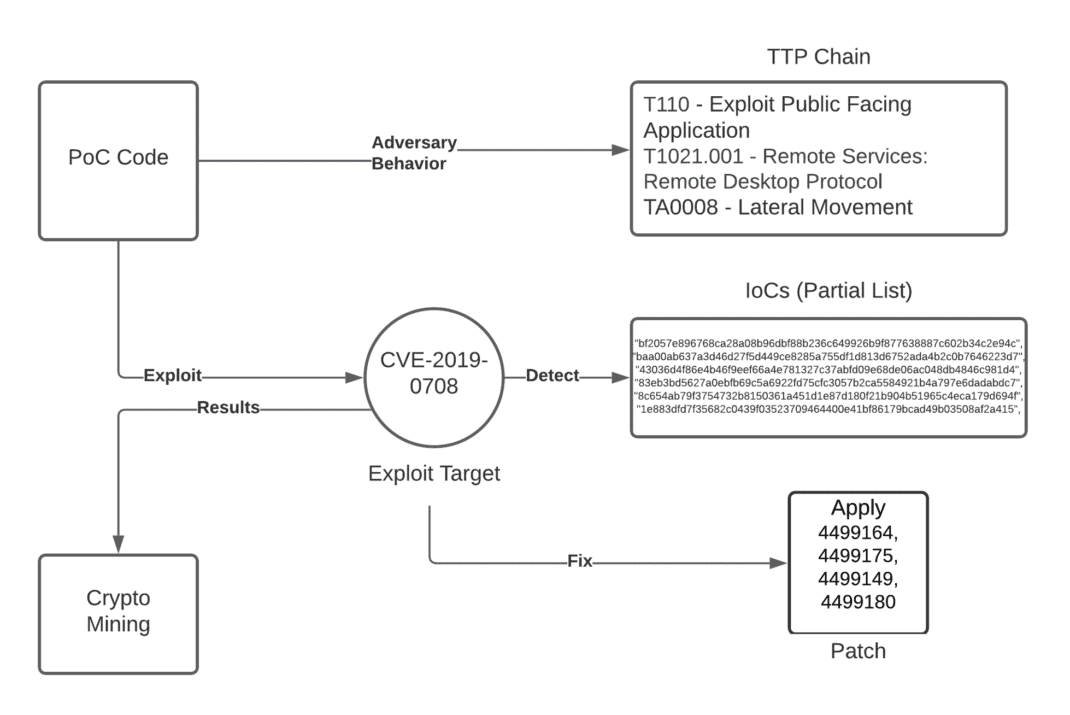
Unpacking the CVEs in the FireEye Breach - Start Here First

FireEye Hack Turns into a Global Supply Chain Attack – Radware Blog

The five most significant IT security incidents of the last 10

Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

Threat Brief: FireEye Red Team Tool Breach

GitHub - A-poc/RedTeam-Tools: Tools and Techniques for Red Team

Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's

Big Russian hack used a technique experts had warned about for
Recomendado para você
-
 Interfacing with CAST Navigation GNSS/INS Simulation Solutions02 abril 2025
Interfacing with CAST Navigation GNSS/INS Simulation Solutions02 abril 2025 -
 Off-Road Racebikes—Ty Cullins' 2022 TM EN 30002 abril 2025
Off-Road Racebikes—Ty Cullins' 2022 TM EN 30002 abril 2025 -
 Who Killed Art Deco?: A Novel - Kindle edition by Barris, Chuck02 abril 2025
Who Killed Art Deco?: A Novel - Kindle edition by Barris, Chuck02 abril 2025 -
 Device Fingerprinting - SEON Docs02 abril 2025
Device Fingerprinting - SEON Docs02 abril 2025 -
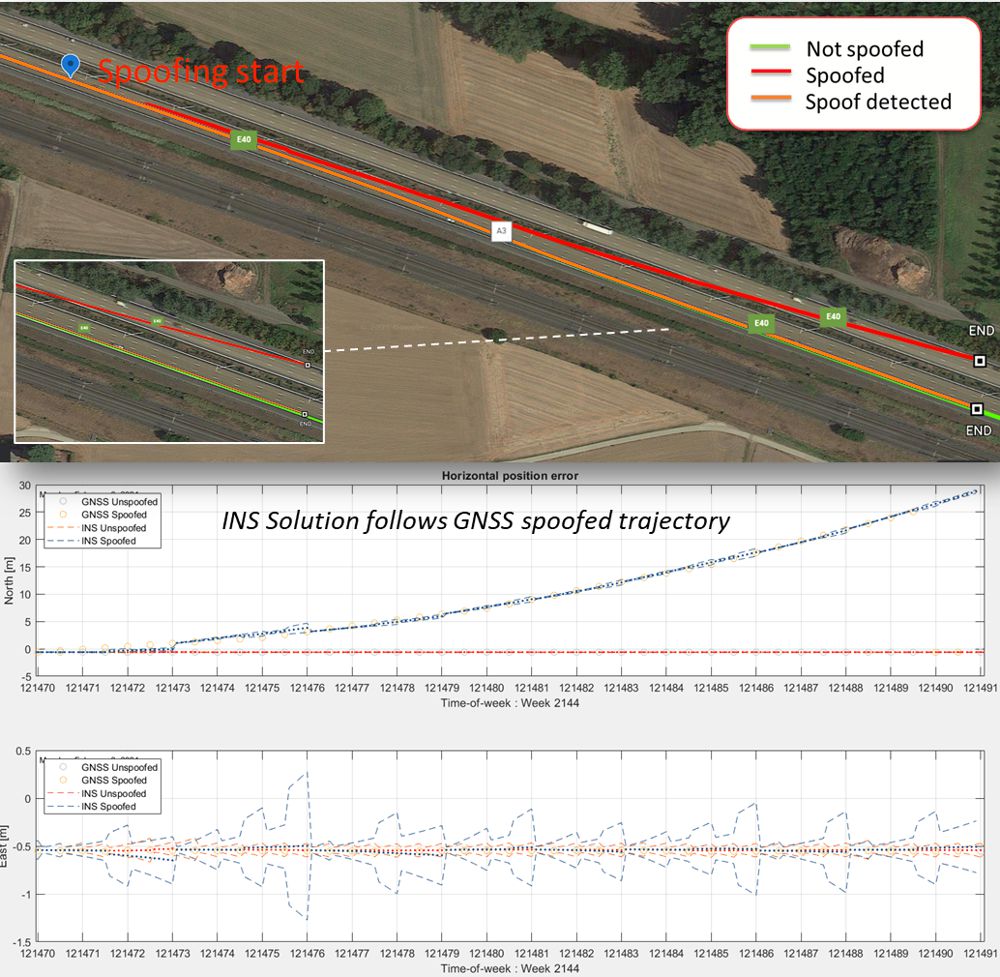 Secure GPS receivers are crucial for GNSS/INS systems - Highways Today02 abril 2025
Secure GPS receivers are crucial for GNSS/INS systems - Highways Today02 abril 2025 -
 11 Types of Spoofing Attacks Every Security Professional Should02 abril 2025
11 Types of Spoofing Attacks Every Security Professional Should02 abril 2025 -
 GitHub - sCANd3ww/RedEngineX: RedENGINE is the Best LUA Executor and Spoofer for FiveM with features Like: Premium Menu, Dumper, Stopper Ressource, Event Logger, Aimbot,ESP.02 abril 2025
GitHub - sCANd3ww/RedEngineX: RedENGINE is the Best LUA Executor and Spoofer for FiveM with features Like: Premium Menu, Dumper, Stopper Ressource, Event Logger, Aimbot,ESP.02 abril 2025 -
 ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks02 abril 2025
ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks02 abril 2025 -
 How Do MAC Spoofing Attacks Work?02 abril 2025
How Do MAC Spoofing Attacks Work?02 abril 2025 -
HookSpoofer: The Modified Open Source Stealer Bundlers Making the Rounds02 abril 2025
você pode gostar
-
 Anime artwork, Manga art, Manga anime02 abril 2025
Anime artwork, Manga art, Manga anime02 abril 2025 -
 Shark 7's Slot Casino – Lucky Wheel Deluxe Game by Ante Ruzic02 abril 2025
Shark 7's Slot Casino – Lucky Wheel Deluxe Game by Ante Ruzic02 abril 2025 -
 Gioca Friday Night Funkin (FNF) contro NekoFreak Unblocked : r/Y9FreeGames02 abril 2025
Gioca Friday Night Funkin (FNF) contro NekoFreak Unblocked : r/Y9FreeGames02 abril 2025 -
 poki subway surfers 🍀 Um Cassino Líder em Criptomoedas com Milhares de Jogos. –poki subway surfers02 abril 2025
poki subway surfers 🍀 Um Cassino Líder em Criptomoedas com Milhares de Jogos. –poki subway surfers02 abril 2025 -
 Devil May Cry 5: Deluxe Edition - What's included02 abril 2025
Devil May Cry 5: Deluxe Edition - What's included02 abril 2025 -
 Fairy Tail Online 3D đã được mua về Việt Nam02 abril 2025
Fairy Tail Online 3D đã được mua về Việt Nam02 abril 2025 -
![Ace Combat 7: Skies Unknown [Gameplay] - IGN](https://assets1.ignimgs.com/thumbs/userUploaded/2018/12/10/ace-combat-art-1544464138848.jpg) Ace Combat 7: Skies Unknown [Gameplay] - IGN02 abril 2025
Ace Combat 7: Skies Unknown [Gameplay] - IGN02 abril 2025 -
 Camisa do Independiente 202302 abril 2025
Camisa do Independiente 202302 abril 2025 -
 COMO DESENHAR O NARUTO SHIPPUDEN02 abril 2025
COMO DESENHAR O NARUTO SHIPPUDEN02 abril 2025 -
 Roblox Sheep Race Simulator Codes: Sprint to Victory - 2023 August-Redeem Code-LDPlayer02 abril 2025
Roblox Sheep Race Simulator Codes: Sprint to Victory - 2023 August-Redeem Code-LDPlayer02 abril 2025