SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 28 março 2025

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

OSINTer - Elusive Sandman APT Targets Telecom Giants With LuaJIT Toolkit

Chinese Silkloader cyber attack tool falls into Russian hands

Pakistani Power Firms urged to establish Cyber Security guidelines

Cl0p hits Hitachi Energy. TikTok surveillance investigated. BreachForums arrest. Hacktivists, torrents in the hybrid war.
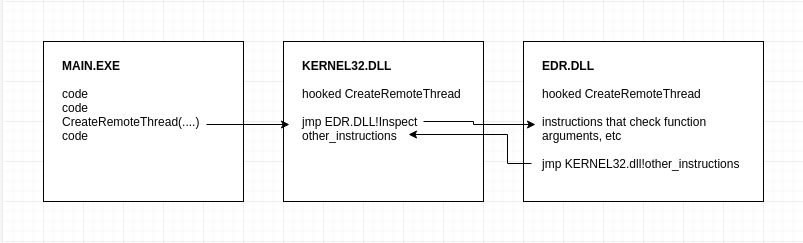
AV/EDR Evasion, Malware Development P-3
Risky Biz News: Google wants to reduce lifespan of TLS certificates from one year to just 90 days

Chinese Silkloader cyber attack tool falls into Russian hands
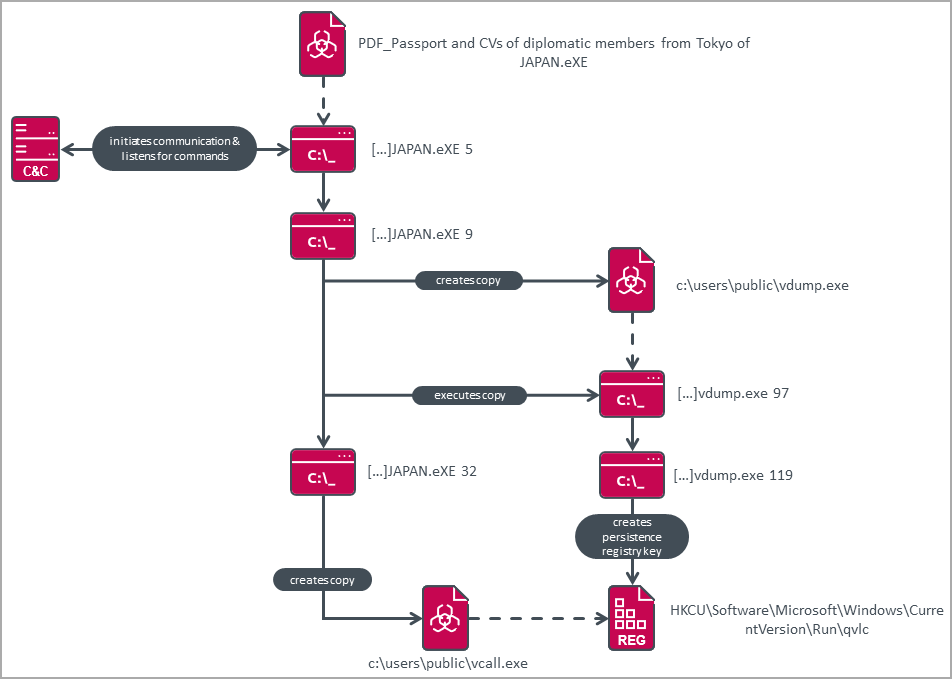
Chinese hackers use new custom backdoor to evade detection
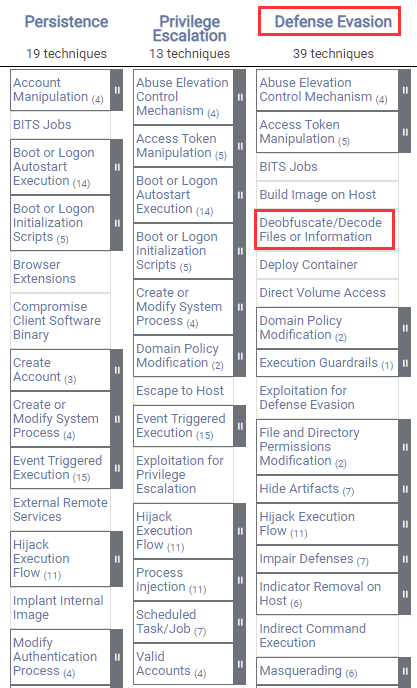
Windows Red Team Defense Evasion Techniques - HackerSploit Blog

Hack Like a Pro: How to Evade AV Detection with Veil-Evasion « Null Byte :: WonderHowTo
Recomendado para você
-
Evade Script Pastebin 202328 março 2025
-
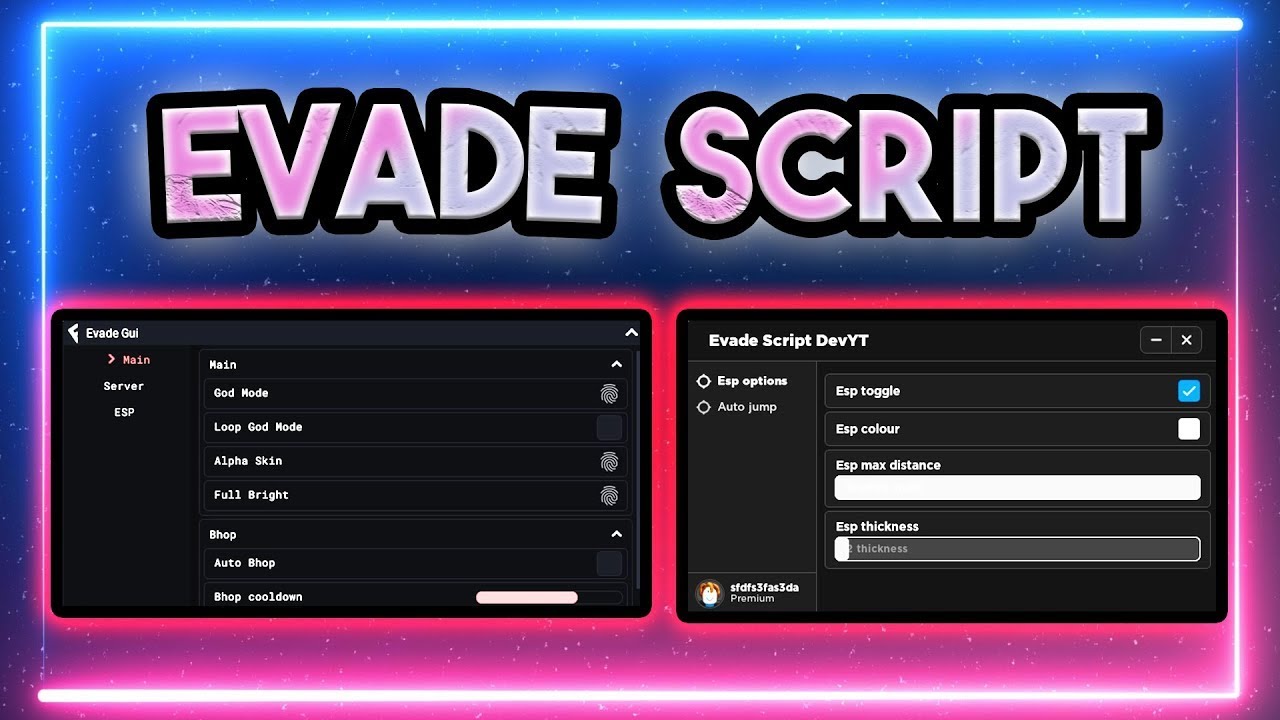 ⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD28 março 2025
⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD28 março 2025 -
Evade-script/script at main · Lux11111111/Evade-script · GitHub28 março 2025
-
evade script|TikTok Search28 março 2025
-
 CanHub Evade Script Download 100% Free28 março 2025
CanHub Evade Script Download 100% Free28 março 2025 -
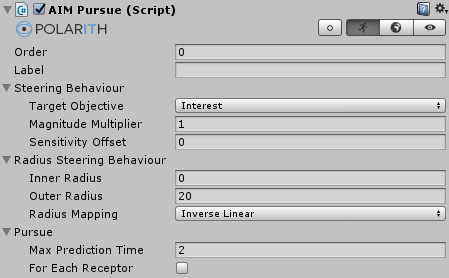 Polarith AI: Pursue and Evade28 março 2025
Polarith AI: Pursue and Evade28 março 2025 -
 BATLoader Lurks Under PowerShell Script to Evade Detection, Launch28 março 2025
BATLoader Lurks Under PowerShell Script to Evade Detection, Launch28 março 2025 -
 Python info-stealing malware uses Unicode to evade detection28 março 2025
Python info-stealing malware uses Unicode to evade detection28 março 2025 -
 Analyzing Ruby malware - VMRay28 março 2025
Analyzing Ruby malware - VMRay28 março 2025 -
Winnti Hackers Split Cobalt Strike Into 154 Pieces To Evade Detection28 março 2025
você pode gostar
-
 EMPRESTEI MEU PERFIL do ROBLOX PARA INSCRITOS e me ARREPENDI..28 março 2025
EMPRESTEI MEU PERFIL do ROBLOX PARA INSCRITOS e me ARREPENDI..28 março 2025 -
 Relogio xadrez dgt 2010 Black Friday Casas Bahia28 março 2025
Relogio xadrez dgt 2010 Black Friday Casas Bahia28 março 2025 -
 Cookie Clicker tips and strategy guide – Destructoid28 março 2025
Cookie Clicker tips and strategy guide – Destructoid28 março 2025 -
 Update: PlayStation Portal Remote Play Device Launches November 15 For $200 - Game Informer28 março 2025
Update: PlayStation Portal Remote Play Device Launches November 15 For $200 - Game Informer28 março 2025 -
pes 2011 mobile download apk|TikTok Search28 março 2025
-
 Kashima (Bokutachi wa Benkyou ga Dekinai) - Pictures28 março 2025
Kashima (Bokutachi wa Benkyou ga Dekinai) - Pictures28 março 2025 -
 Two People Playing Chess Game First Moves Of Stock Footage SBV-309451141 - Storyblocks28 março 2025
Two People Playing Chess Game First Moves Of Stock Footage SBV-309451141 - Storyblocks28 março 2025 -
![The Cuphead Show- Outcast Of Ink Part 1 [ON HOLD] - Prologue: Once](https://i.pinimg.com/564x/c4/b2/46/c4b2464734240ee8f5ceacc03aed94fc.jpg) The Cuphead Show- Outcast Of Ink Part 1 [ON HOLD] - Prologue: Once28 março 2025
The Cuphead Show- Outcast Of Ink Part 1 [ON HOLD] - Prologue: Once28 março 2025 -
 🇧🇷 Denji Finalmente Conseguiu C*mԐr a makima😳🤨 (Chainsaw Man28 março 2025
🇧🇷 Denji Finalmente Conseguiu C*mԐr a makima😳🤨 (Chainsaw Man28 março 2025 -
 Tomo-chan wa Onnanoko! Misaki Kousuke Anime icons yellow hair Blue28 março 2025
Tomo-chan wa Onnanoko! Misaki Kousuke Anime icons yellow hair Blue28 março 2025


