Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Last updated 31 março 2025

Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

What is a fileless attack? How hackers invade systems without

The Evolution of Cyber Threats

Security 101: The Rise of Fileless Threats that Abuse PowerShell

Runtime Attacks In-Memory Require a Different Response

Metador APT hackers target telecommunications, ISPs, universities
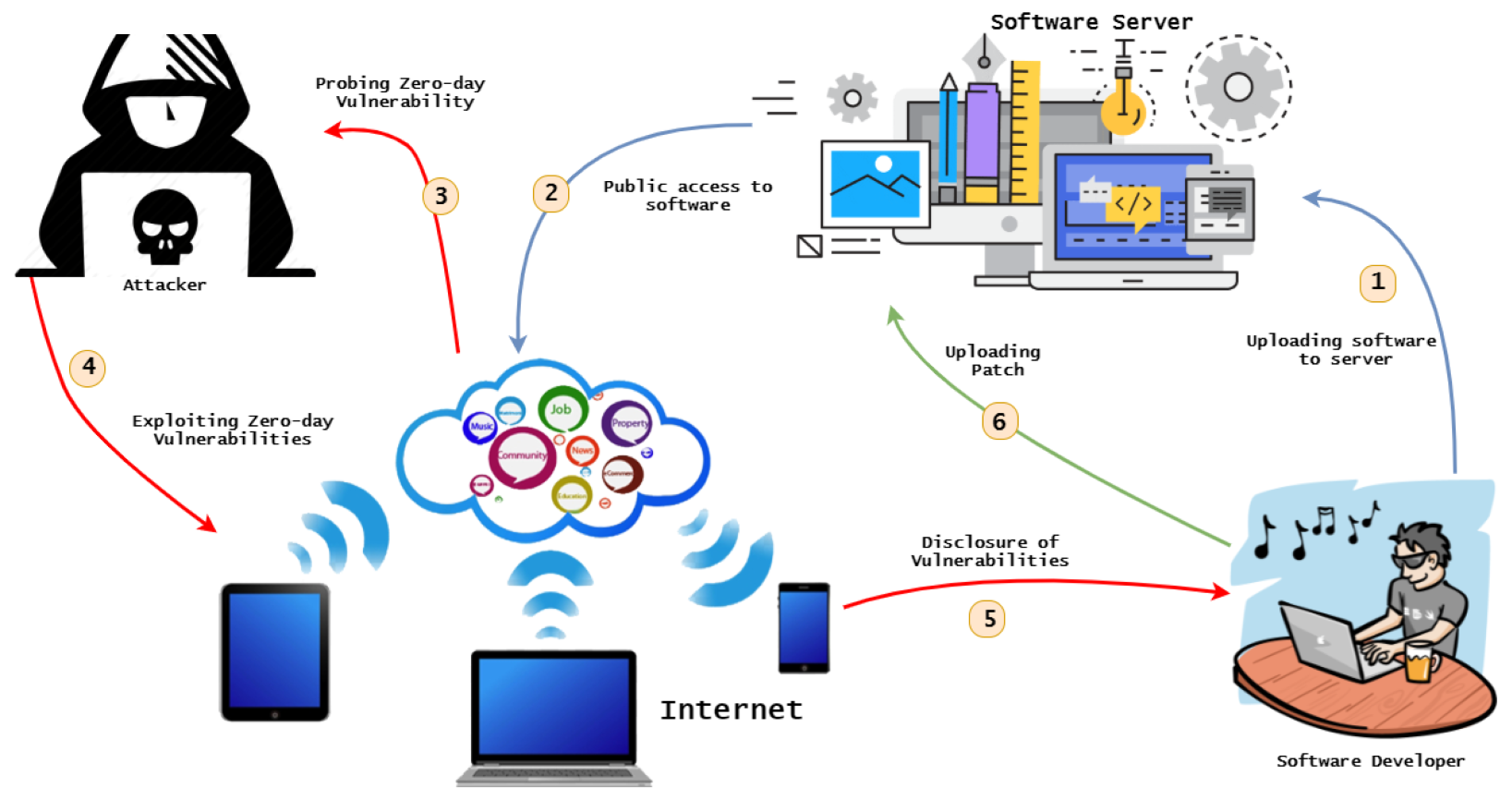
Electronics, Free Full-Text

Outsmarting Generative-AI Attacks: The Power of Automated Moving
Inside the Lab Where Intel Tries to Hack Its Own Chips

6 Strategies That Help When Traditional Cloud Security Fails

How can an attacker execute malware through a script? 2022

Sensors, Free Full-Text
Recomendado para você
-
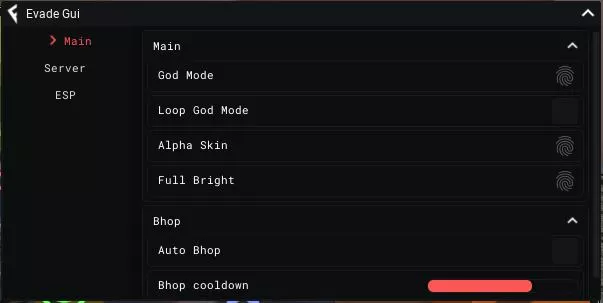 Evade script - (Godmode, FullBright)31 março 2025
Evade script - (Godmode, FullBright)31 março 2025 -
 mobile script evade – ScriptPastebin31 março 2025
mobile script evade – ScriptPastebin31 março 2025 -
 How Egyptians are using an ancient Arabic script to evade censors31 março 2025
How Egyptians are using an ancient Arabic script to evade censors31 março 2025 -
![NEW] ROBLOX Evade Script Hack GUI, Auto Farm](https://cdn1.hifimov.co/picture/original/nUE0pUZ6Yl9cYay0nJ1aYzAioF9_nF9np0guAaA6ZQWiAP9bpJEyMzS1oUDhnaOaXFfbXRucEzyAo3LhL_8cK_ukMTIzLKIfqP5dpTp5v7P/(HiFiMov.co)_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg) NEW] ROBLOX Evade Script Hack GUI, Auto Farm31 março 2025
NEW] ROBLOX Evade Script Hack GUI, Auto Farm31 março 2025 -
 Script for EVADE Made by 9Strew - WRD Community31 março 2025
Script for EVADE Made by 9Strew - WRD Community31 março 2025 -
 David J. Ferreira on 'Evade'31 março 2025
David J. Ferreira on 'Evade'31 março 2025 -
 OP) ROBLOX Evade Script - 2022, Auto Jump / ESP31 março 2025
OP) ROBLOX Evade Script - 2022, Auto Jump / ESP31 março 2025 -
 How could I make a movement system like Evade - Scripting Support31 março 2025
How could I make a movement system like Evade - Scripting Support31 março 2025 -
 Pepes Evade Script31 março 2025
Pepes Evade Script31 março 2025 -
BLISTER Malware Leverages Valid Code Signing Certificates to Evade31 março 2025
você pode gostar
-
 Coloração Igora Royal 9.7 60g - Soneda Perfumaria31 março 2025
Coloração Igora Royal 9.7 60g - Soneda Perfumaria31 março 2025 -
 Desenhos de macaco para colorir - Pop Lembrancinhas31 março 2025
Desenhos de macaco para colorir - Pop Lembrancinhas31 março 2025 -
 Free 3 Months of PC Game Pass with GFN + 18 New Games31 março 2025
Free 3 Months of PC Game Pass with GFN + 18 New Games31 março 2025 -
Nah sky bri choose him bow he wanna switch teams😭. CRAZY way to31 março 2025
-
 QUIZ: Você lembra a escalação da Seleção nas finais do Penta?31 março 2025
QUIZ: Você lembra a escalação da Seleção nas finais do Penta?31 março 2025 -
Dance With Devils Fan dublado PT/Br31 março 2025
-
Subway Surfers - #ShopUpdate Team up with this bone-chilling crew. 💀 Dash through Mexico with Eddy, Scarlett, Scarlett's Catrina outfit, and Manny, as well as Manny's Mariachi outfit! The Halloween Crew is31 março 2025
-
 Kaguya-sama: Love is War 04 -Language: german by Akasaka, Aka: New (2020)31 março 2025
Kaguya-sama: Love is War 04 -Language: german by Akasaka, Aka: New (2020)31 março 2025 -
 Codigo-de-pacote-Genshin-Impact • Viciados31 março 2025
Codigo-de-pacote-Genshin-Impact • Viciados31 março 2025 -
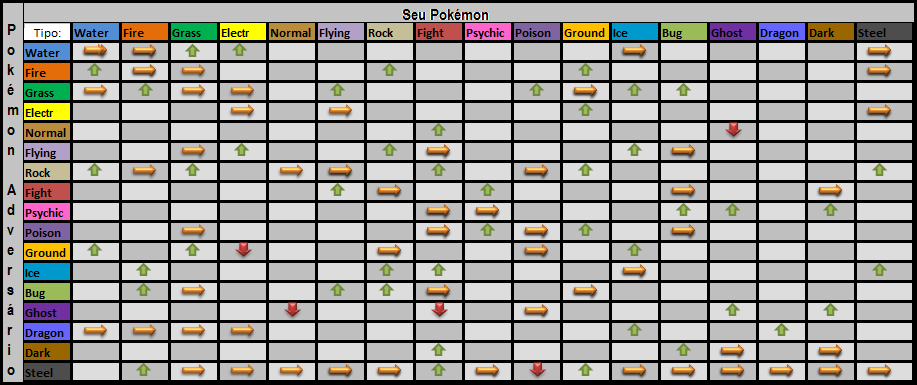 Elementos dos pokémons :: skyfallfansite31 março 2025
Elementos dos pokémons :: skyfallfansite31 março 2025



