Trend Micro Research on X: Scenario 2: If the user is not logged
Por um escritor misterioso
Last updated 31 março 2025
How to generate various logs in Trend Micro for Windows
Passed a potential security risk' in Virus/Malware Logs
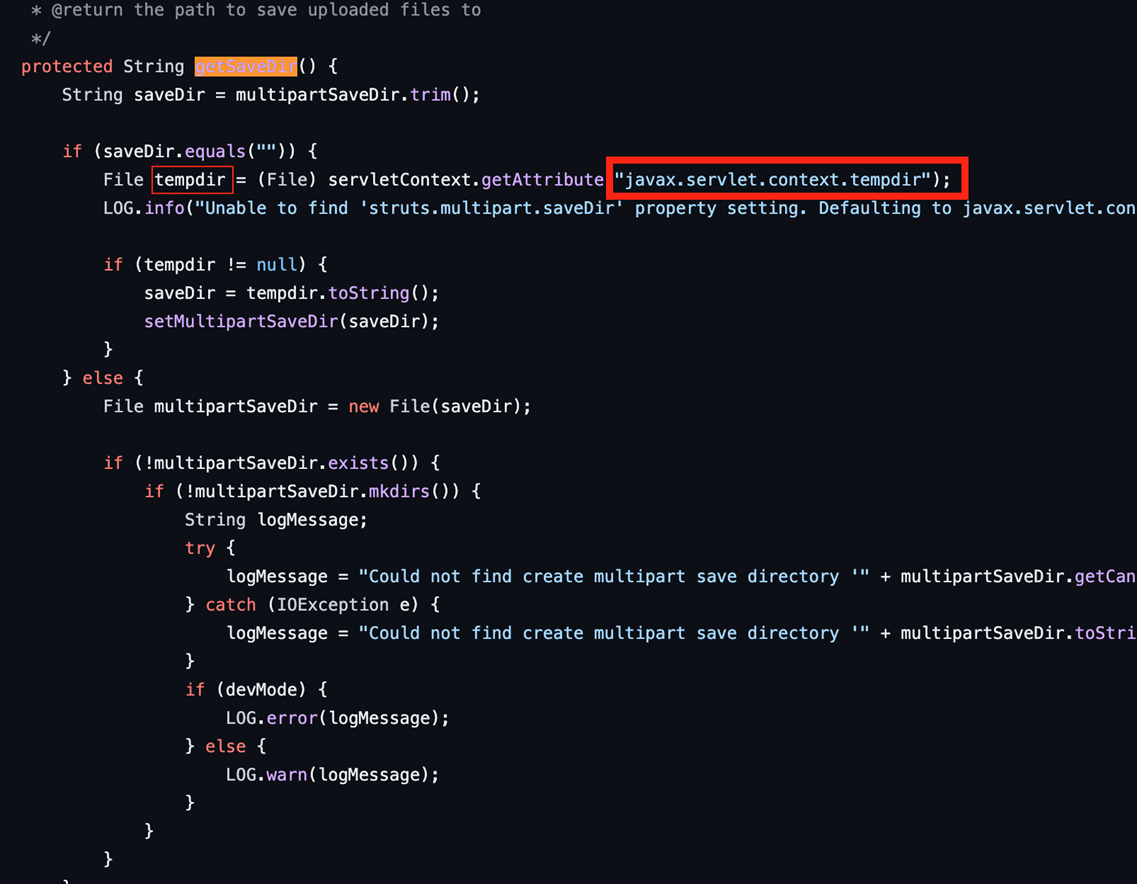
Decoding CVE-2023-50164: Unveiling the Apache Struts File Upload Exploit
Verification Unsuccessful error from Trend Micro Antivirus

Top 10 Data Loss Prevention Software
How to collect debug logs in Trend Micro Security on Windows

What is EAP-TLS?
Sensors, Free Full-Text

RADIUS Server Authentication: Explained
Generate CDT logs - InterScan Messaging Security Suite for Linux

Log Formatting: 7 Best Practices for Readable Log Files
How to generate various logs in Trend Micro for Windows
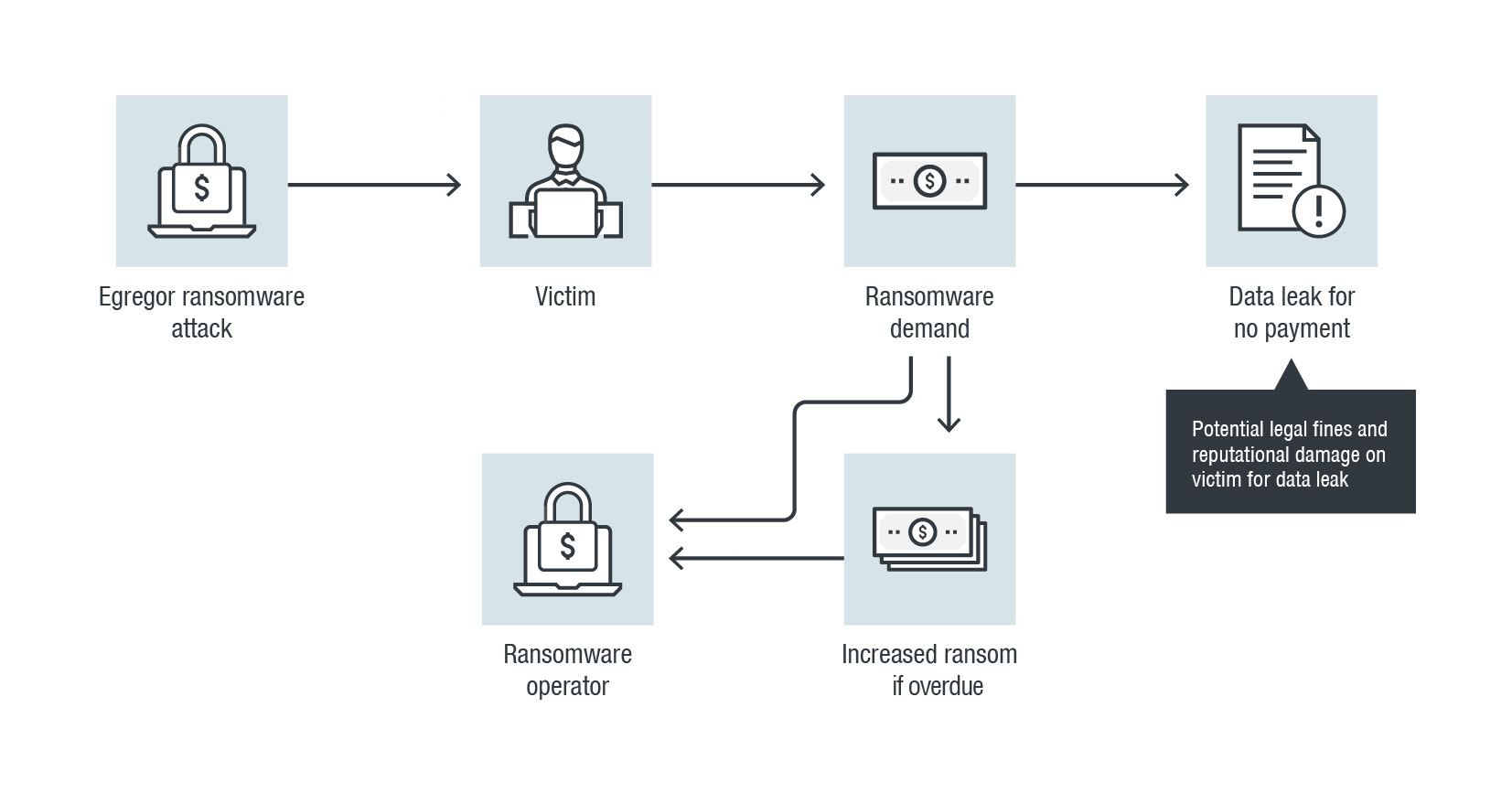
A Constant State of Flux: Trend Micro 2020 Annual Cybersecurity Report - Security Roundup
Recomendado para você
-
 How to Use Facebook Login on Your Website : Social Media Examiner31 março 2025
How to Use Facebook Login on Your Website : Social Media Examiner31 março 2025 -
 What to do when Facebook's homepage looks like gibberish?31 março 2025
What to do when Facebook's homepage looks like gibberish?31 março 2025 -
 Implement Facebook Login with PHP31 março 2025
Implement Facebook Login with PHP31 março 2025 -
 How To Add Facebook Login To Your Moodle 4.0+ Site - eLearning Themes31 março 2025
How To Add Facebook Login To Your Moodle 4.0+ Site - eLearning Themes31 março 2025 -
 Facebook login page redesign on Behance31 março 2025
Facebook login page redesign on Behance31 março 2025 -
 Inspiration Login Screen on Android by Facebook - UI Garage31 março 2025
Inspiration Login Screen on Android by Facebook - UI Garage31 março 2025 -
 Facebook Login/SignUp Page Design using Html & CSS 3 - Web Design31 março 2025
Facebook Login/SignUp Page Design using Html & CSS 3 - Web Design31 março 2025 -
 Facebook Login Form31 março 2025
Facebook Login Form31 março 2025 -
 SignUp with Facebook using VueJS. Sign-in / Sign-up with Facebook31 março 2025
SignUp with Facebook using VueJS. Sign-in / Sign-up with Facebook31 março 2025 -
 Facebook login page Stock Photo - Alamy31 março 2025
Facebook login page Stock Photo - Alamy31 março 2025
você pode gostar
-
 1 HORA DE EFEITOS SONOROS RODRIGO FARO VAI DAR NAMORO31 março 2025
1 HORA DE EFEITOS SONOROS RODRIGO FARO VAI DAR NAMORO31 março 2025 -
![Aegislash EX (65/119) [XY: Phantom Forces]](https://finalround.games/cdn/shop/products/049daeb5-7194-43c1-a9b4-ebe4bc813ecd_7cd8aa6e-a240-4295-a4cd-9aa73bc769a7_1000x1000.png?v=1696334836) Aegislash EX (65/119) [XY: Phantom Forces]31 março 2025
Aegislash EX (65/119) [XY: Phantom Forces]31 março 2025 -
 BLOODBORNE PC VERSION CONFIRMED!!! (NEW INFO)31 março 2025
BLOODBORNE PC VERSION CONFIRMED!!! (NEW INFO)31 março 2025 -
 Naruto Pop-Up Shop Features Characters in East Asian Outfits31 março 2025
Naruto Pop-Up Shop Features Characters in East Asian Outfits31 março 2025 -
 Hasbro Nerf Roblox SharkBite: Web Launcher Rocker Blaster, Includes Code to Redeem Exclusive Virtual Item, 2 Nerf Rockets, Pump Action31 março 2025
Hasbro Nerf Roblox SharkBite: Web Launcher Rocker Blaster, Includes Code to Redeem Exclusive Virtual Item, 2 Nerf Rockets, Pump Action31 março 2025 -
 Koi wa Sekai Seifuku no Ato de Merch31 março 2025
Koi wa Sekai Seifuku no Ato de Merch31 março 2025 -
 Sufficiency on Steam31 março 2025
Sufficiency on Steam31 março 2025 -
 Livro - Xadrez Vitorioso - Táticas em Promoção na Americanas31 março 2025
Livro - Xadrez Vitorioso - Táticas em Promoção na Americanas31 março 2025 -
 Finally!31 março 2025
Finally!31 março 2025 -
 Premium Vector Green leaf nature plant conceptual symbol vector31 março 2025
Premium Vector Green leaf nature plant conceptual symbol vector31 março 2025