Reverse engineering Emotet – Our approach to protect GRNET against the trojan
Por um escritor misterioso
Last updated 01 abril 2025
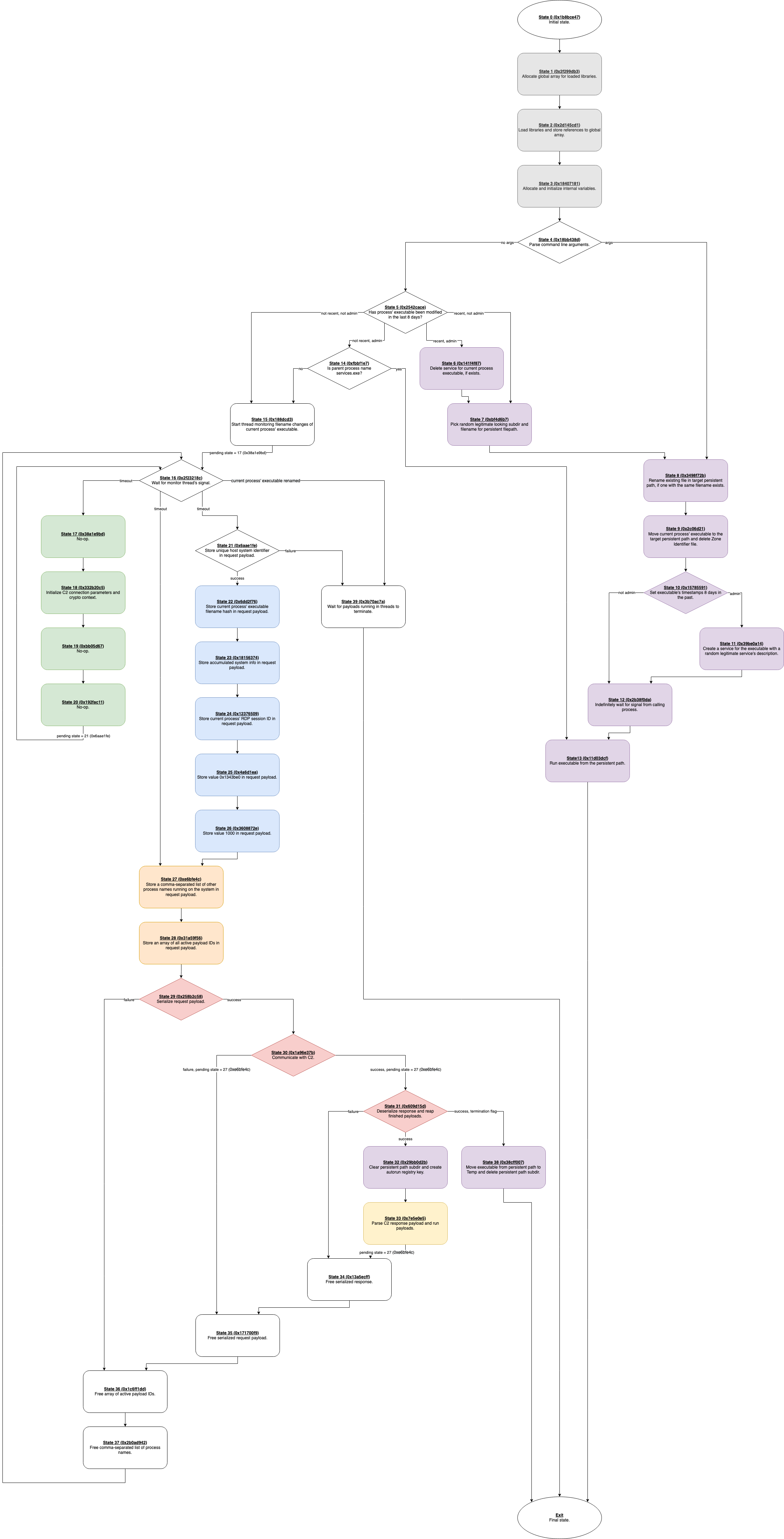
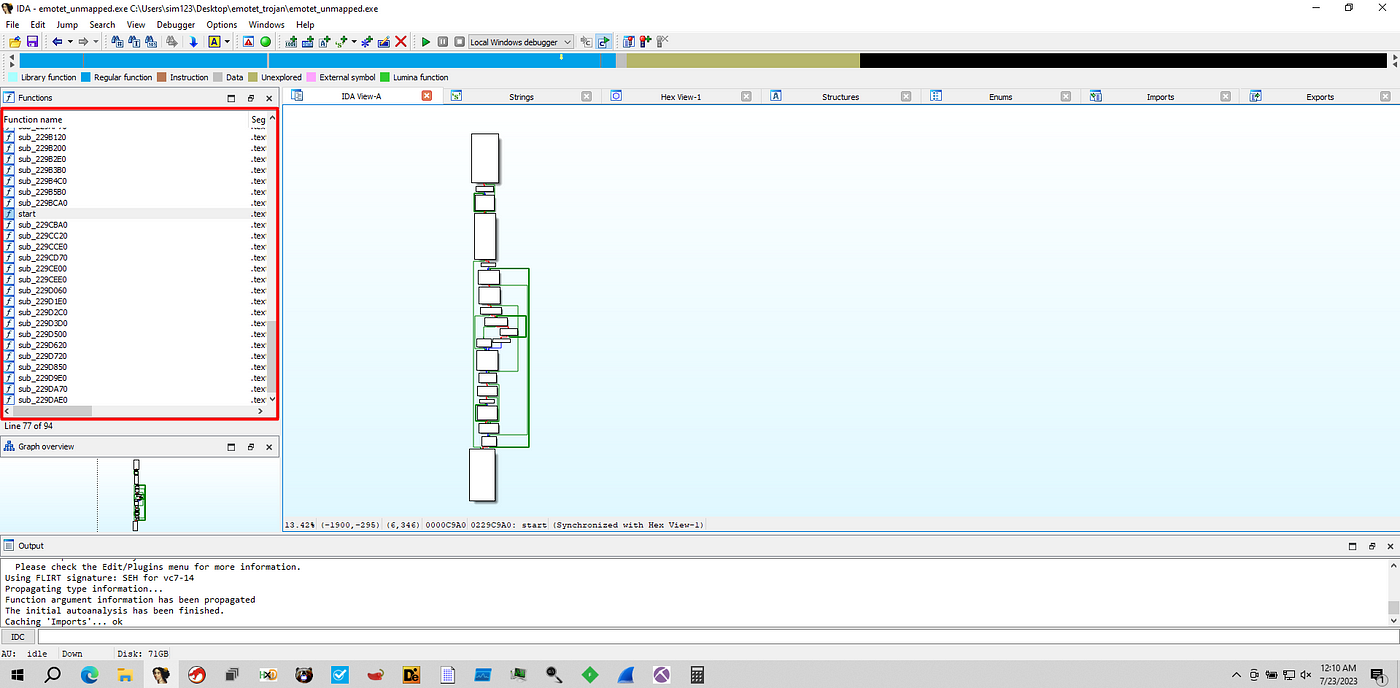
Unpacking Emotet Trojan. Emotet, in general, is a banking…, by mov eax, 27
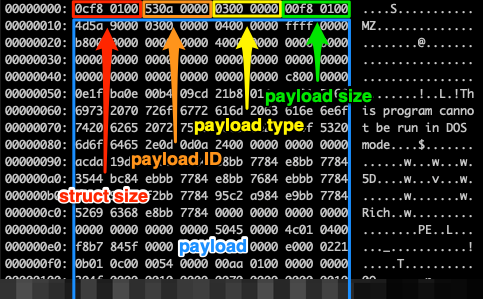
Reverse engineering Emotet – Our approach to protect GRNET against the trojan
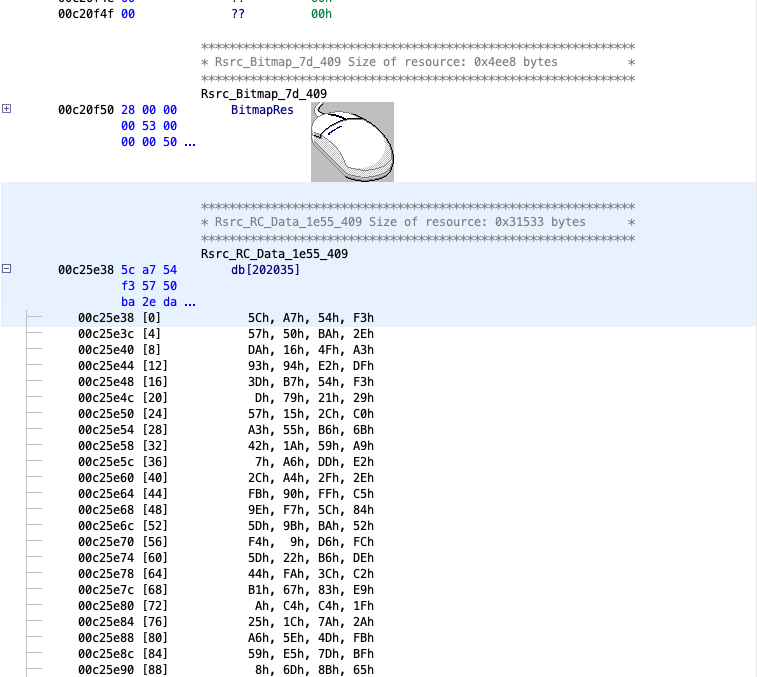
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

What is Emotet? And how to guard against this persistent Trojan malware

What is Emotet Malware and How Do You Defend Against it?
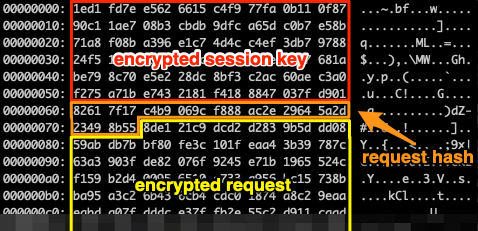
Reverse engineering Emotet – Our approach to protect GRNET against the trojan

Reverse engineering Emotet – Our approach to protect GRNET against the trojan

The Reemergence of the Emotet Trojan
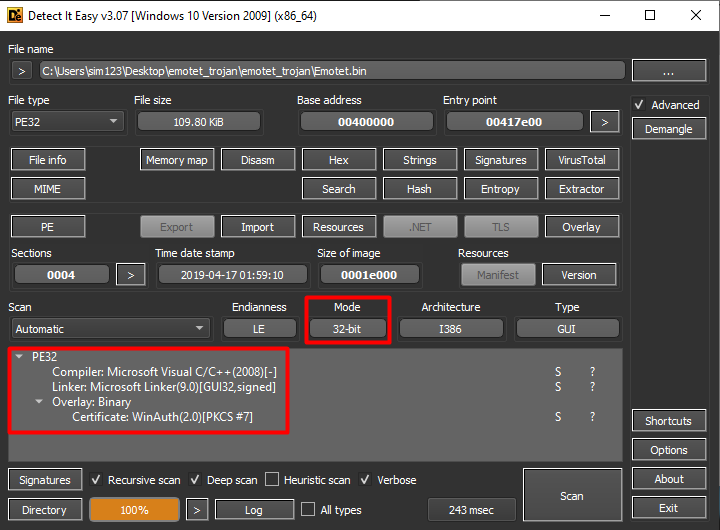
Unpacking Emotet Trojan. Emotet, in general, is a banking…, by mov eax, 27
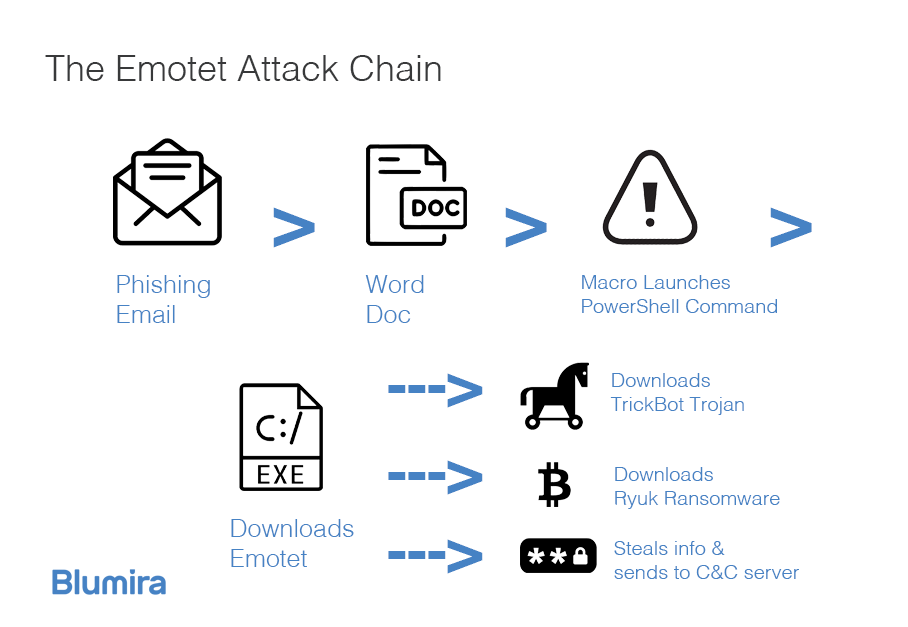
Detect and Protect Against the Return of Emotet Malware
Recomendado para você
-
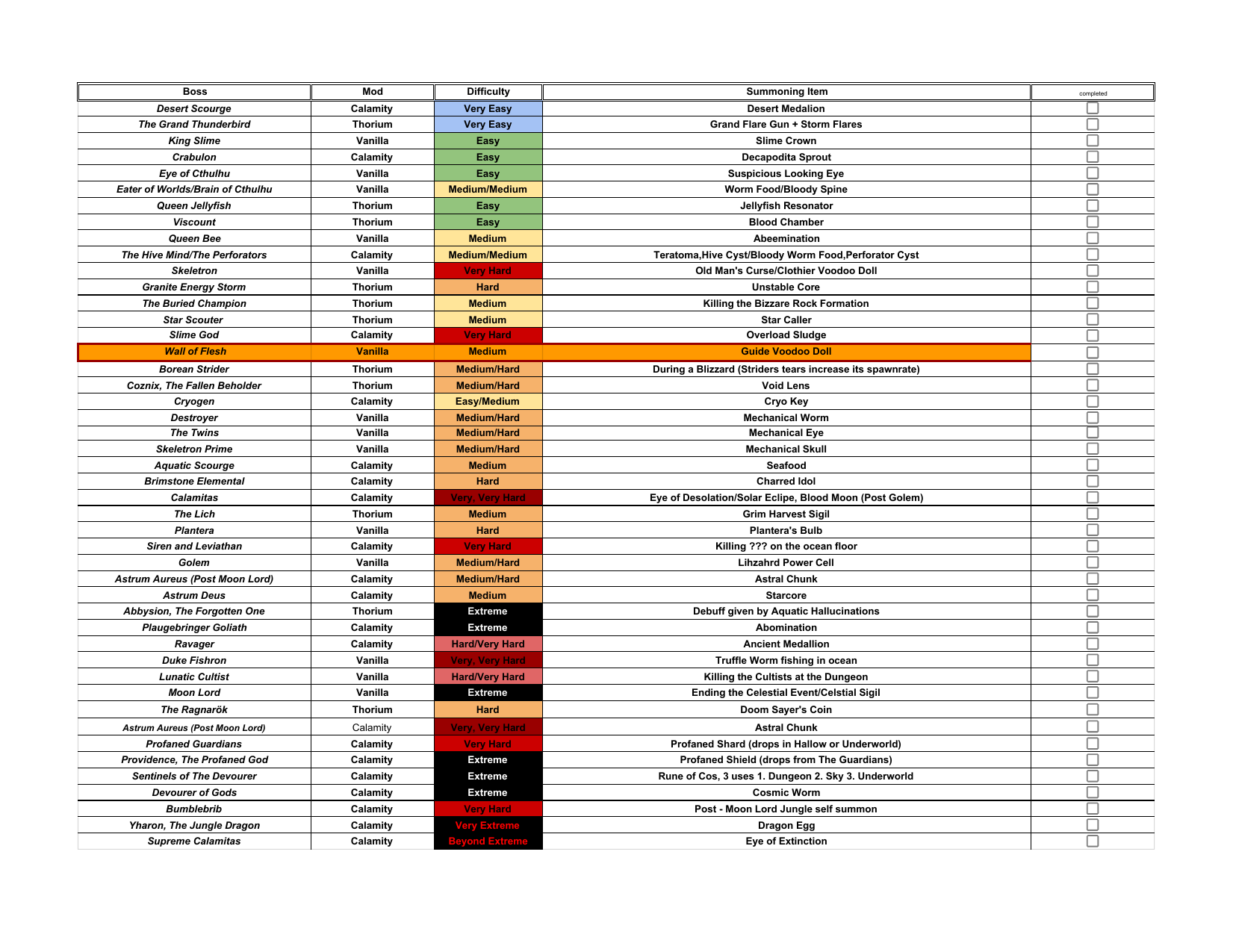
 My boss difficulty tier list. (With explanations in comments)Inspired by u/Inopryant. : r/Terraria01 abril 2025
My boss difficulty tier list. (With explanations in comments)Inspired by u/Inopryant. : r/Terraria01 abril 2025 -
 Bosses - Official Calamity Mod Wiki01 abril 2025
Bosses - Official Calamity Mod Wiki01 abril 2025 -
 Moon Lord - Terraria Wiki01 abril 2025
Moon Lord - Terraria Wiki01 abril 2025 -
 Terraria Calamity Mod Progression Guide; Hardmode01 abril 2025
Terraria Calamity Mod Progression Guide; Hardmode01 abril 2025 -
 Terraria Modded - Boss progression (Expert Revengeance)01 abril 2025
Terraria Modded - Boss progression (Expert Revengeance)01 abril 2025 -
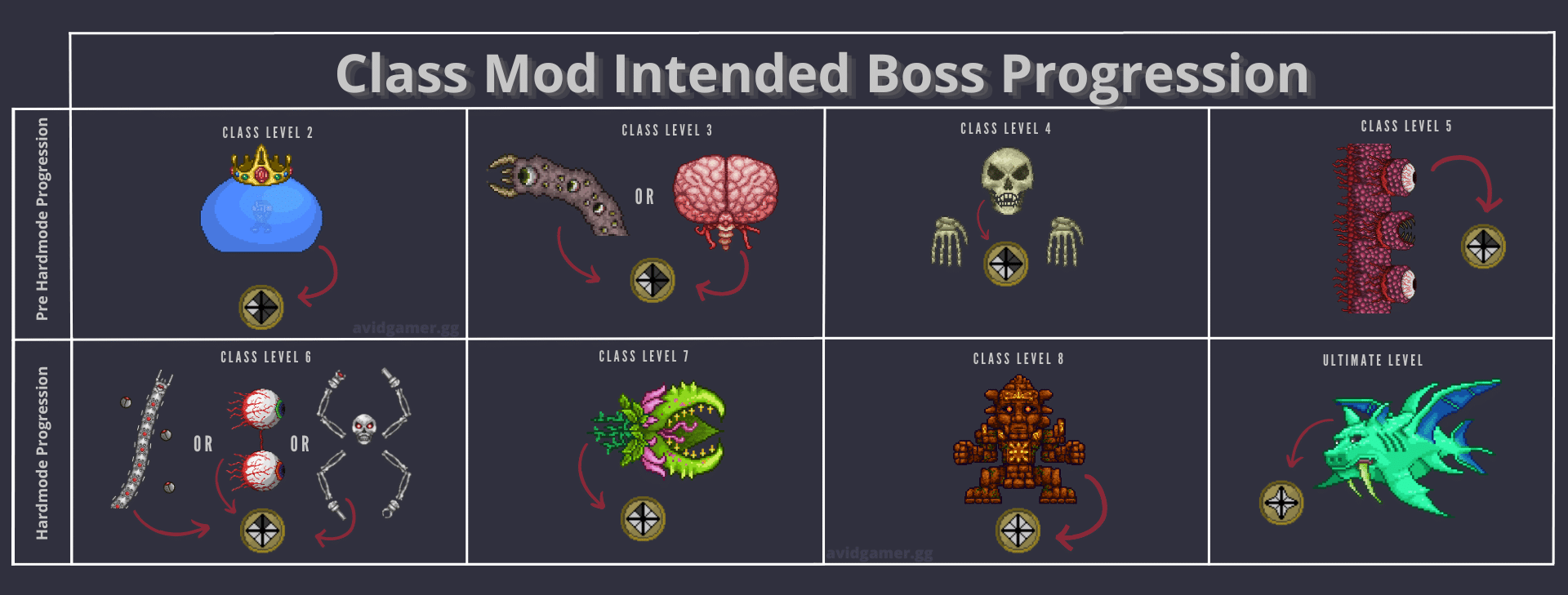 Terraria Apacchii's Class Mod (2023) Download and Review01 abril 2025
Terraria Apacchii's Class Mod (2023) Download and Review01 abril 2025 -
Terraria's BEST Pre-Boss Melee Progression!!! 😜 #terraria #game #stea, terraria01 abril 2025
-
r/Terraria 🌳 على X: I drew mini versions of every boss (Calamity included because it's a lifestyle) / X01 abril 2025
-
 Terraria - 1.4.2 Master Mode summon class progression guide (grand chief!)01 abril 2025
Terraria - 1.4.2 Master Mode summon class progression guide (grand chief!)01 abril 2025 -
 Bosses - Terraria Wiki01 abril 2025
Bosses - Terraria Wiki01 abril 2025
você pode gostar
-
 Live a Live Part #57 - Mecha - Update # 301 abril 2025
Live a Live Part #57 - Mecha - Update # 301 abril 2025 -
 Pin em Dicas de estudo01 abril 2025
Pin em Dicas de estudo01 abril 2025 -
 Download AI Art Image Generator – GoArt APKs for Android - APKMirror01 abril 2025
Download AI Art Image Generator – GoArt APKs for Android - APKMirror01 abril 2025 -
 Hollywood Game Night Battle of the Sexes III (TV Episode 2016) - IMDb01 abril 2025
Hollywood Game Night Battle of the Sexes III (TV Episode 2016) - IMDb01 abril 2025 -
 Fifa 19, ecco la Web App per guadagnare crediti Fut01 abril 2025
Fifa 19, ecco la Web App per guadagnare crediti Fut01 abril 2025 -
 Couvre-lit for Sale avec l'œuvre « TRC - Fai Kurogane » de l'artiste smileyna01 abril 2025
Couvre-lit for Sale avec l'œuvre « TRC - Fai Kurogane » de l'artiste smileyna01 abril 2025 -
 Fairy Tail Photo: Lucy!^-^ Fairy tail lucy, Fairy tail anime lucy, Fairy tail images01 abril 2025
Fairy Tail Photo: Lucy!^-^ Fairy tail lucy, Fairy tail anime lucy, Fairy tail images01 abril 2025 -
 Seeker Is The Ultimate Hybrid Dragon's Dogma Online01 abril 2025
Seeker Is The Ultimate Hybrid Dragon's Dogma Online01 abril 2025 -
 Tudo que precisa saber sobre UEFA Champions League 202201 abril 2025
Tudo que precisa saber sobre UEFA Champions League 202201 abril 2025 -
 Adopt Me News! ❄️🎄 on X: Do you all prefer the new Roblox Studio logo or the old one? #Roblox Image: Bloxy News / X01 abril 2025
Adopt Me News! ❄️🎄 on X: Do you all prefer the new Roblox Studio logo or the old one? #Roblox Image: Bloxy News / X01 abril 2025

