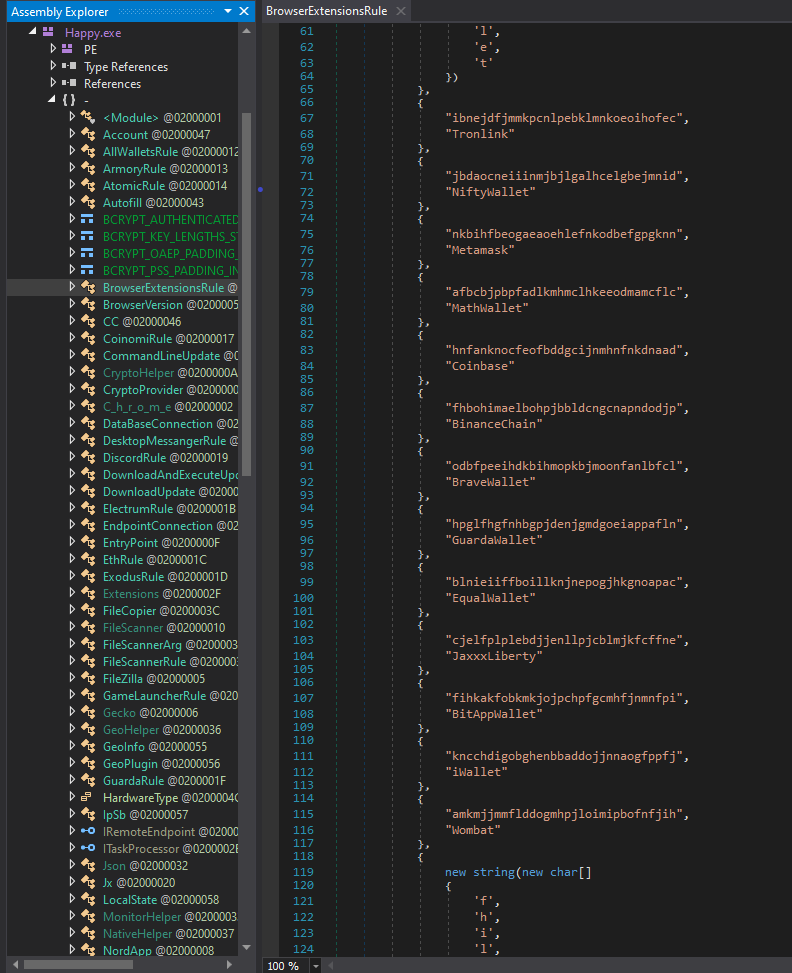
Do Not Cross The 'RedLine' Stealer: Detections and Analysis
Por um escritor misterioso
Last updated 28 março 2025

The Splunk Threat Research Team provides a deep dive analysis of the RedLine Stealer threat and shares valuable insights to help enable blue teamers to defend against and detect this malware variant.
Redline Stealer Malware Static Analysis, by Aaron Stratton

Do Not Cross The 'RedLine' Stealer: Detections and Analysis
Malicious AI Tool Ads Used to Deliver Redline Stealer
RedLine Stealer Campaign Using Binance Mystery Box Videos to Spread GitHub-Hosted Payload - Netskope
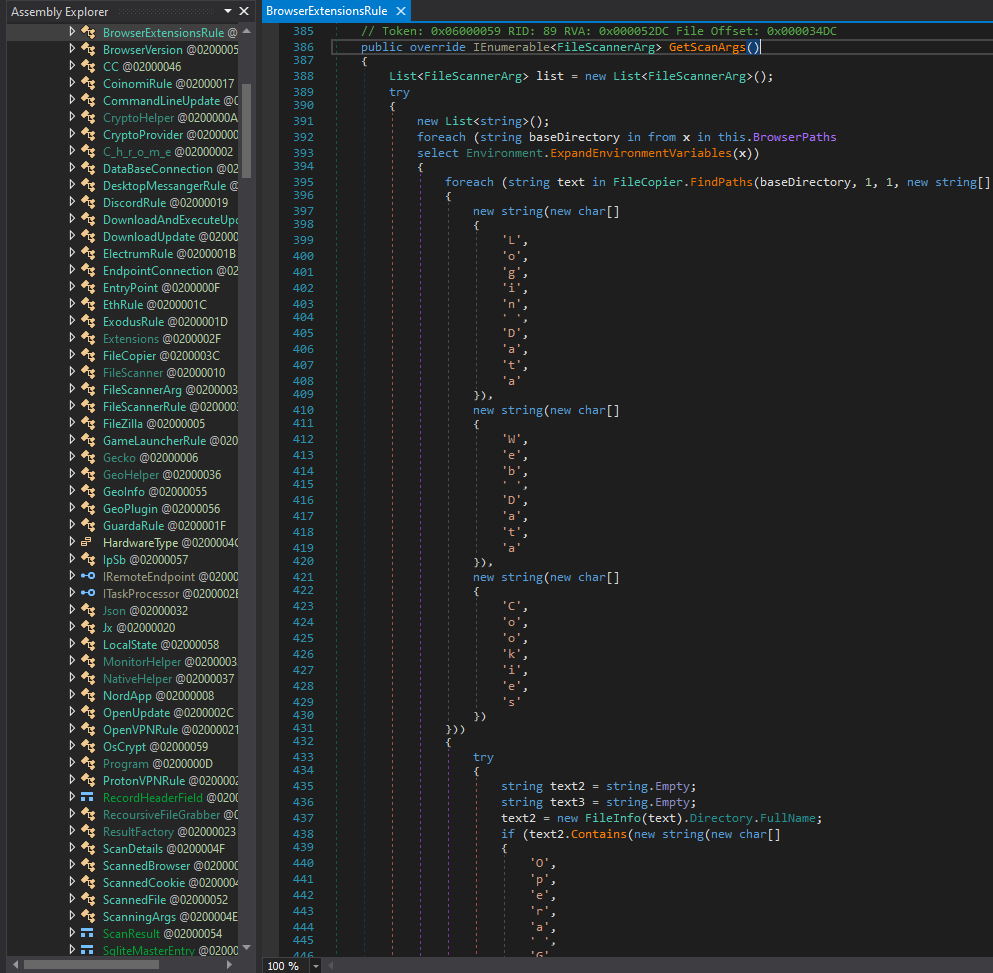
Redline Stealer Malware Static Analysis, by Aaron Stratton

RedLine Stealer malware responsible for stealing majority of the credentials

Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer
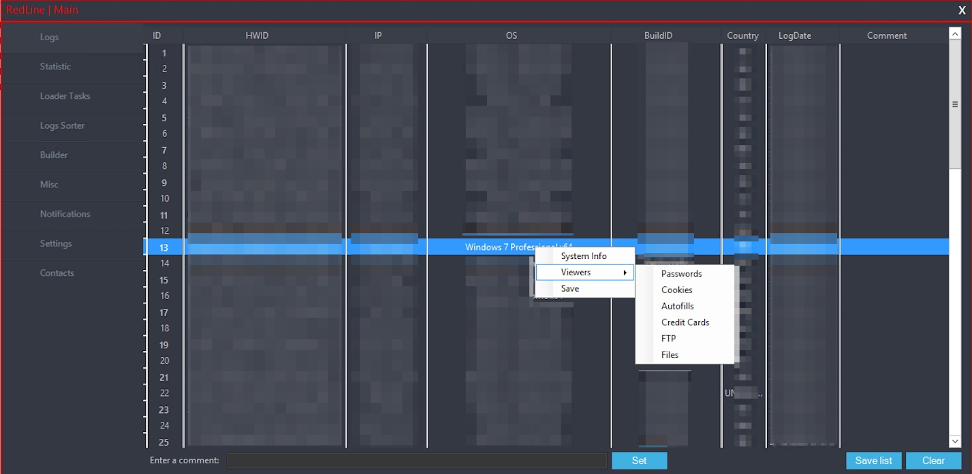
RedLine Stealer Malware - Password Stealer Virus

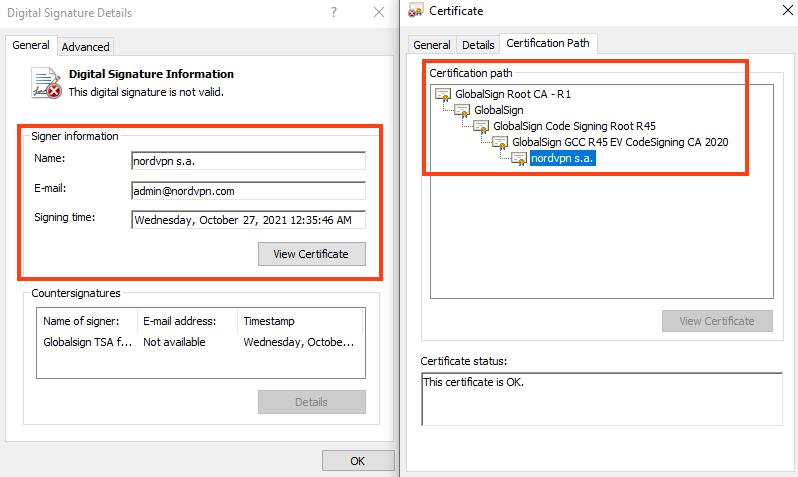
eSentire eSentire Threat Intelligence Malware Analysis: Redline…
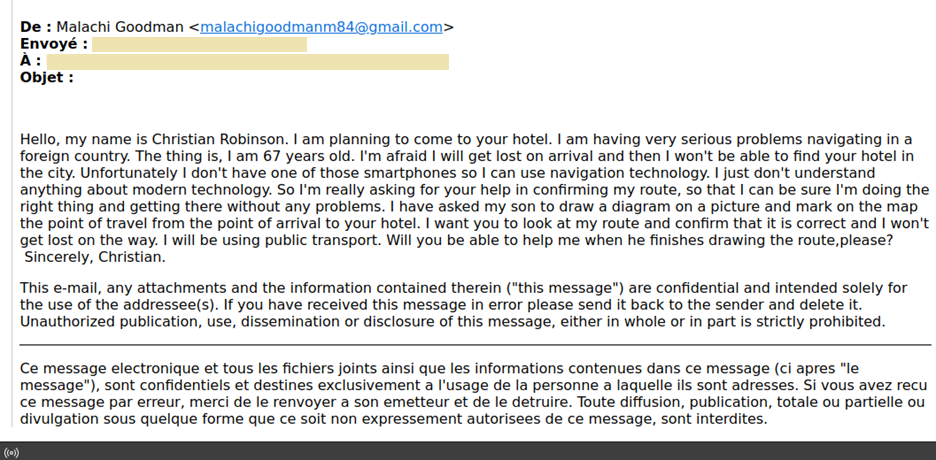
Managed XDR Exposes Spear-Phishing Campaign Targeting Hospitality Industry Using RedLine Stealer
Recomendado para você
-
 Roblox music codes, The best song IDs to use28 março 2025
Roblox music codes, The best song IDs to use28 março 2025 -
 Roblox Pls Donate Codes (June 2023) - Prima Games28 março 2025
Roblox Pls Donate Codes (June 2023) - Prima Games28 março 2025 -
 Evolution Evade Tower Defense Codes - Roblox - December 202328 março 2025
Evolution Evade Tower Defense Codes - Roblox - December 202328 março 2025 -
Codes, Roblox Evade Wiki28 março 2025
-
 Murder Mystery 2 Codes (December 2023) - Knives, Gold & more28 março 2025
Murder Mystery 2 Codes (December 2023) - Knives, Gold & more28 março 2025 -
 All Evade Codes(Roblox) - Tested December 2022 - Player Assist28 março 2025
All Evade Codes(Roblox) - Tested December 2022 - Player Assist28 março 2025 -
 Redtrite28 março 2025
Redtrite28 março 2025 -
 All Secret Evade Codes 2023 - Roblox Code28 março 2025
All Secret Evade Codes 2023 - Roblox Code28 março 2025 -
 Full code Evade Roblox mới nhất 2023, cách nhập code28 março 2025
Full code Evade Roblox mới nhất 2023, cách nhập code28 março 2025 -
Data Encoder Crypter28 março 2025
você pode gostar
-
 Smurf: Rescue in Gargamel's Castle : Video Games28 março 2025
Smurf: Rescue in Gargamel's Castle : Video Games28 março 2025 -
Miami Motocross Park28 março 2025
-
/cdn.vox-cdn.com/uploads/chorus_asset/file/19210970/sirfetchd.jpg) Pokémon Sword and Shield's newest Pokémon revealed: Sirfetch'd - Polygon28 março 2025
Pokémon Sword and Shield's newest Pokémon revealed: Sirfetch'd - Polygon28 março 2025 -
 107 Desenhos Lilo e Stitch para imprimir e colorir28 março 2025
107 Desenhos Lilo e Stitch para imprimir e colorir28 março 2025 -
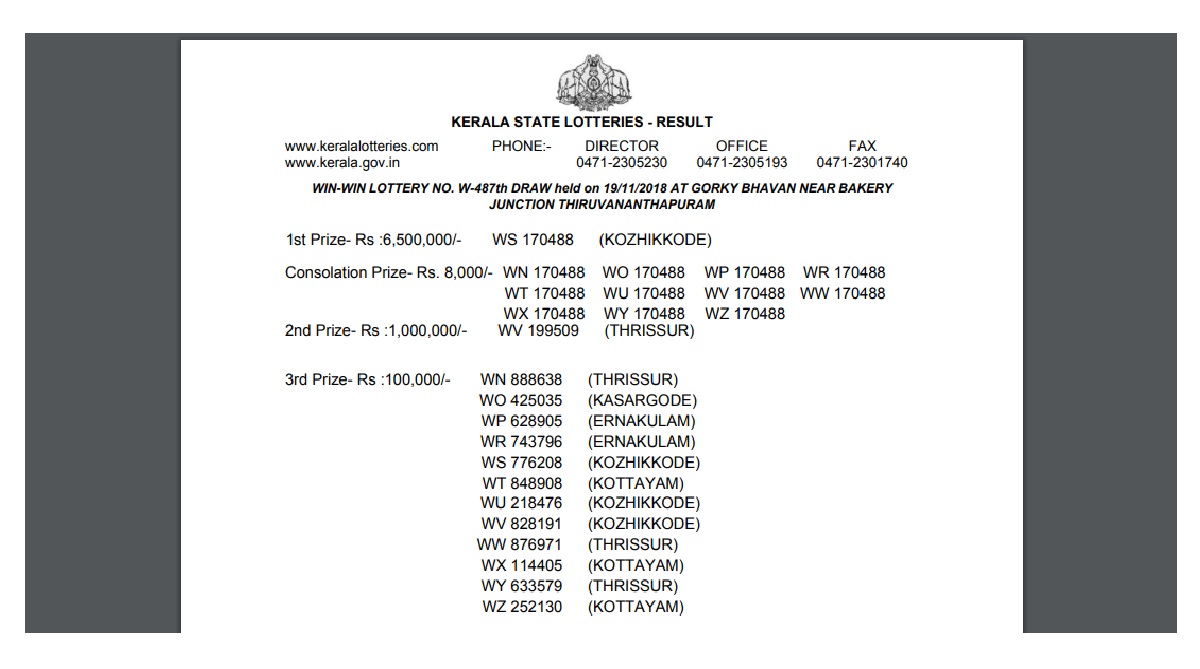 Kerala Lottery Results 2018: WIN WIN W 487 Lottery Draw Results announced at keralalotteries.com28 março 2025
Kerala Lottery Results 2018: WIN WIN W 487 Lottery Draw Results announced at keralalotteries.com28 março 2025 -
 Netojuu no Susume - Anime - AniDB28 março 2025
Netojuu no Susume - Anime - AniDB28 março 2025 -
 Pokemon The Red & Blue Sequel (GBA) Download - PokéHarbor28 março 2025
Pokemon The Red & Blue Sequel (GBA) Download - PokéHarbor28 março 2025 -
 Armenia, Official Travel Website28 março 2025
Armenia, Official Travel Website28 março 2025 -
SE Palmeiras - O segundo jogo na Florida Cup será contra o Spartak Moscow-RUS! Garanta seu pacote com a #PalmeirasTour e nos vemos lá 🇺🇸 ➤ #FloridaCup #ReadyForUniversal28 março 2025
-
 Steaua Bucharest wallpaper. Football wallpaper, Football logo, Uefa champions league28 março 2025
Steaua Bucharest wallpaper. Football wallpaper, Football logo, Uefa champions league28 março 2025



