Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 31 março 2025
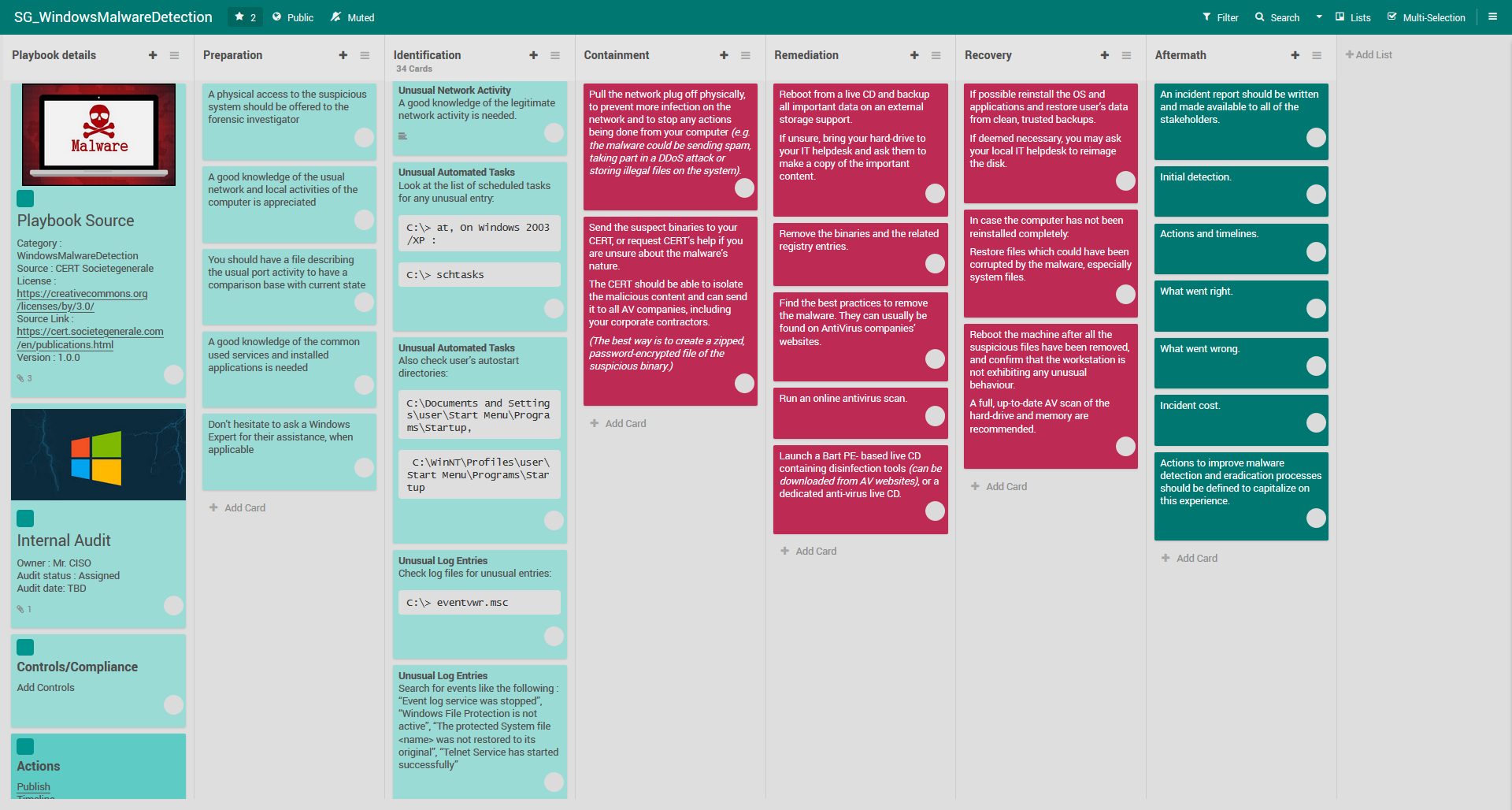
Playbook for Malware outbreak
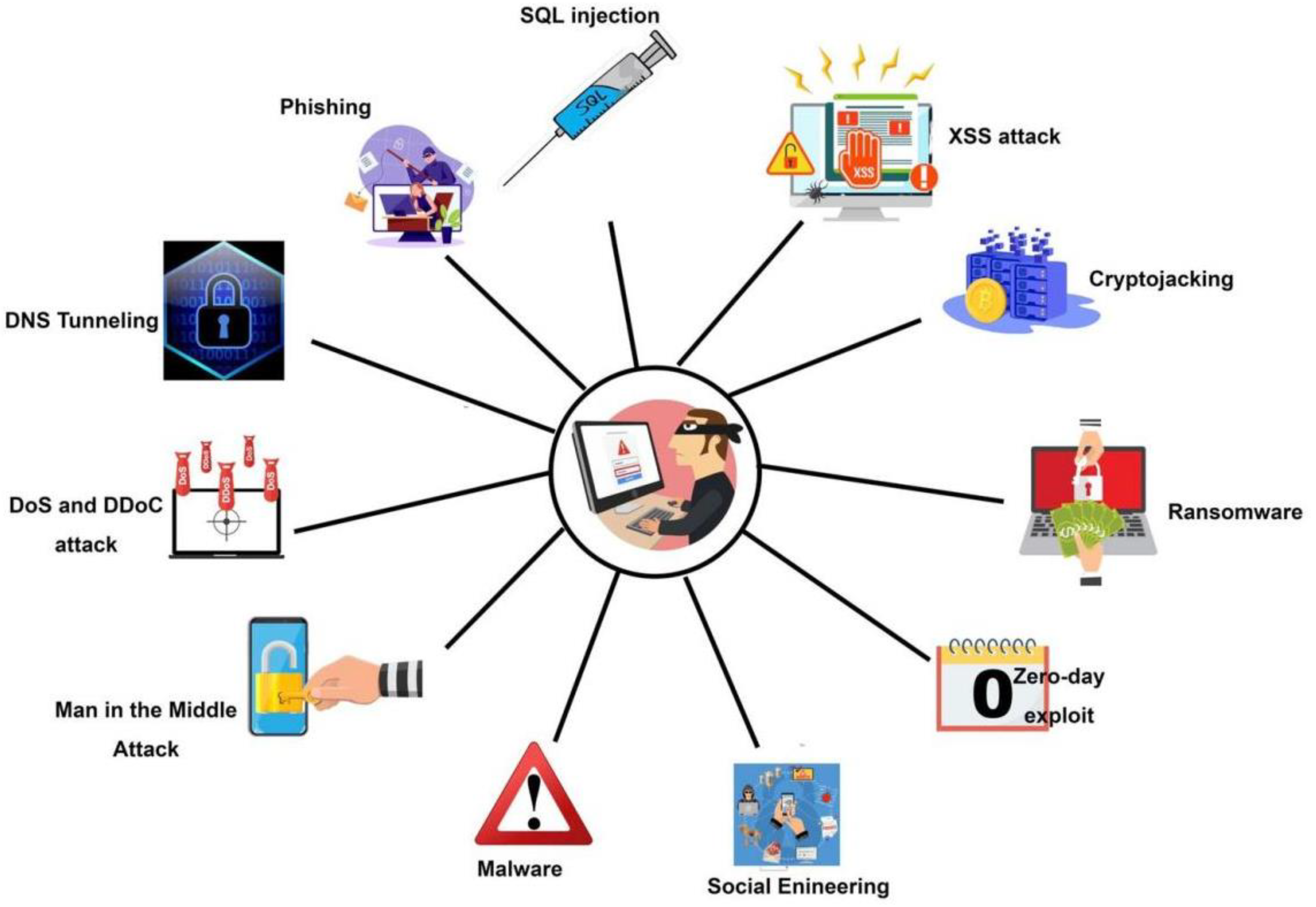
Symmetry, Free Full-Text
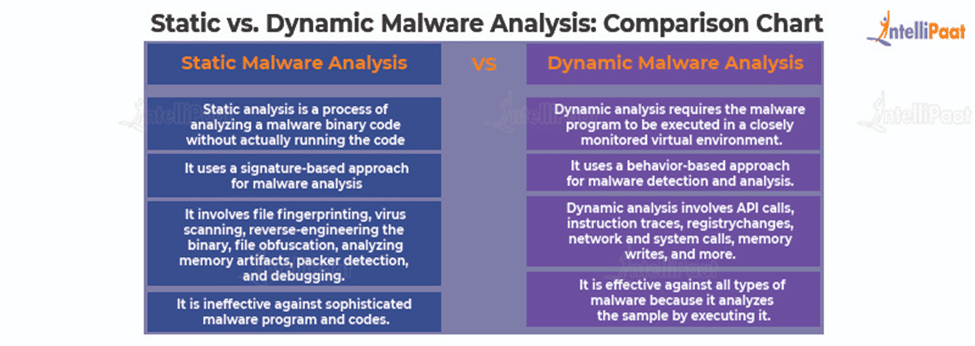
Malware Analysis - What is, Benefits & Types (Easily Explained)
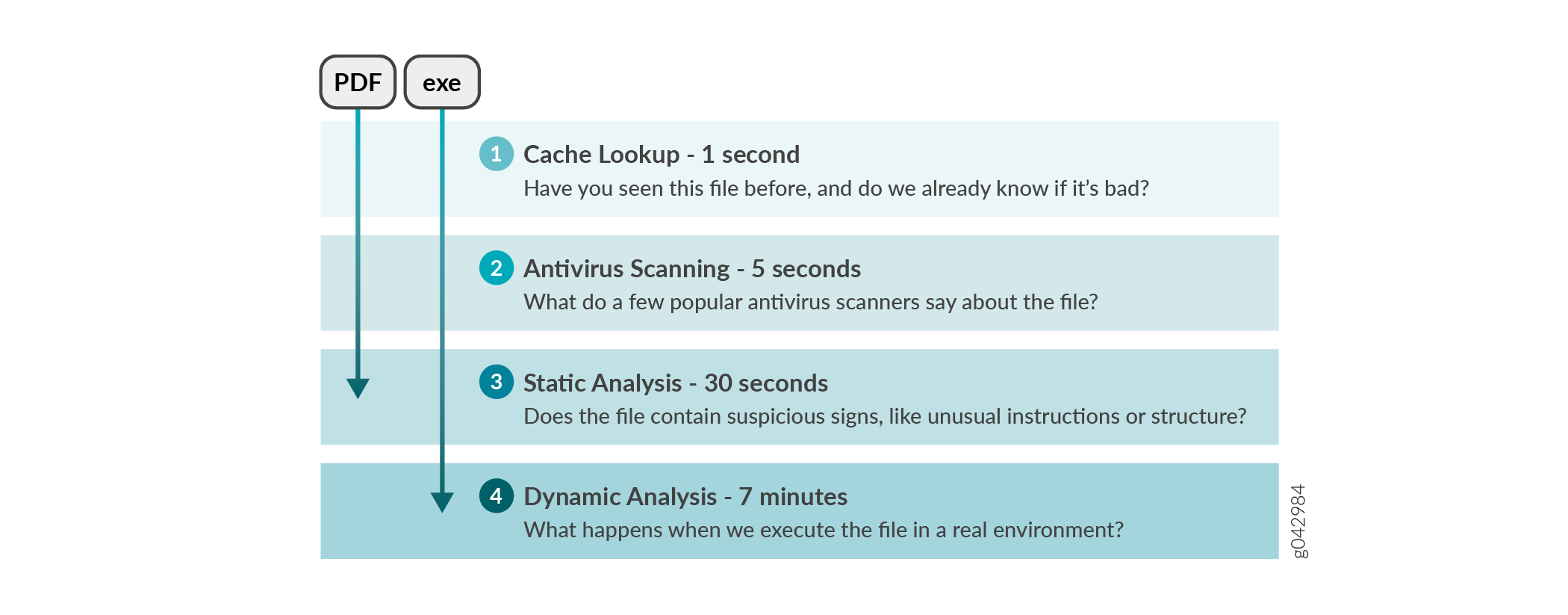
How is Malware Analyzed and Detected?, ATP Cloud
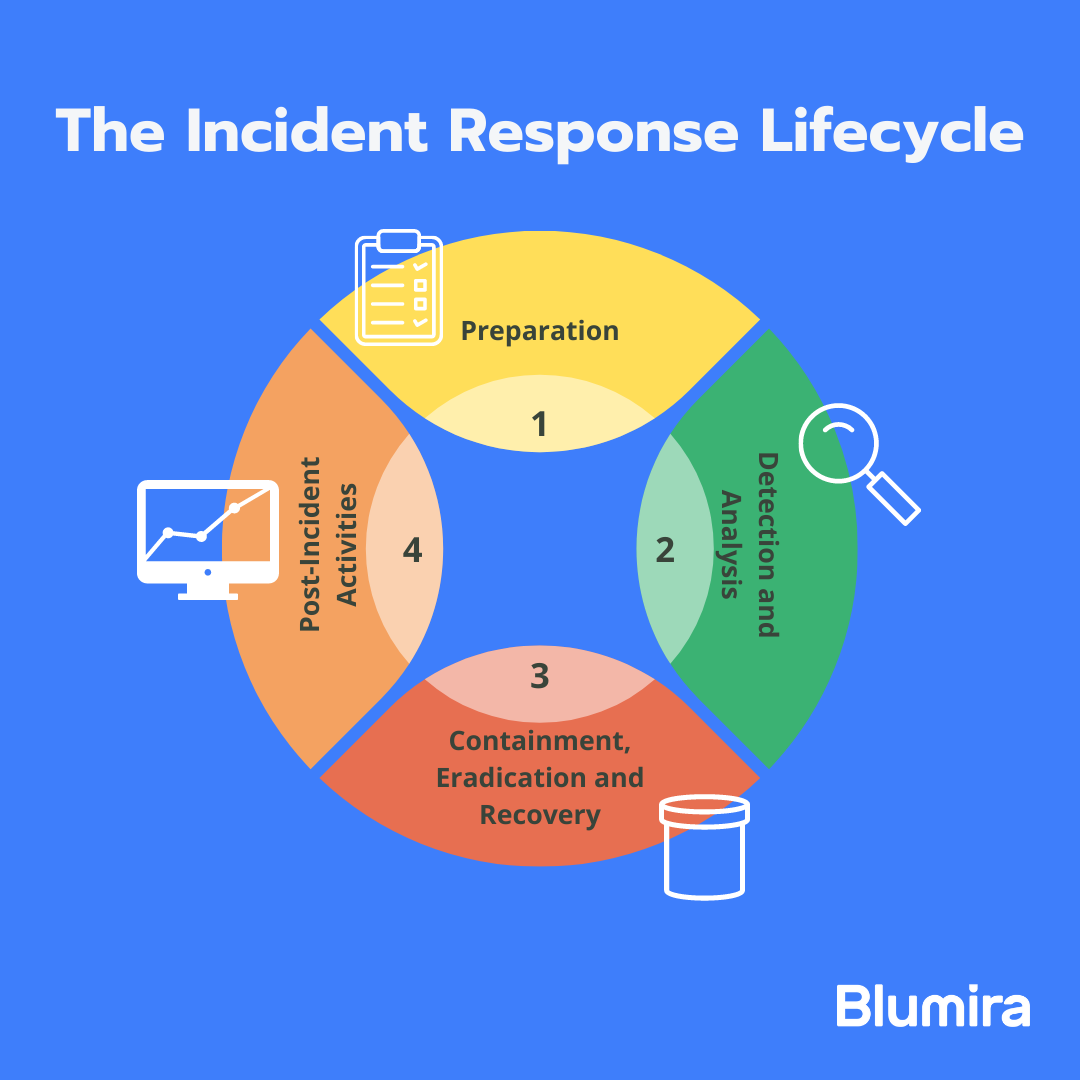
Building Effective Incident Response Procedures

REMnux toolkit for malware analysis version 7 released - Help Net

How to Analyze Malware Infections?

How to Detect New Threats via Suspicious Activities

Malware Analysis: Steps & Examples - CrowdStrike

What is Malware Analysis

Intro to Malware Analysis: What It Is & How It Works - InfoSec
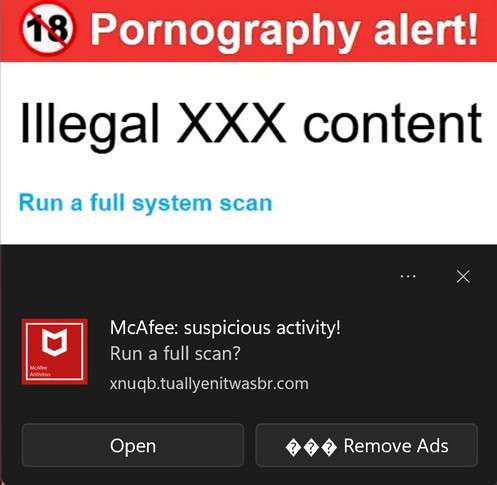
Remove McAfee Suspicious Activity Pop-ups [Virus Removal]

Tools and Techniques for Collection and Analysis of Internet-of

How Malware Analysis Works - NetWitness Community - 669511
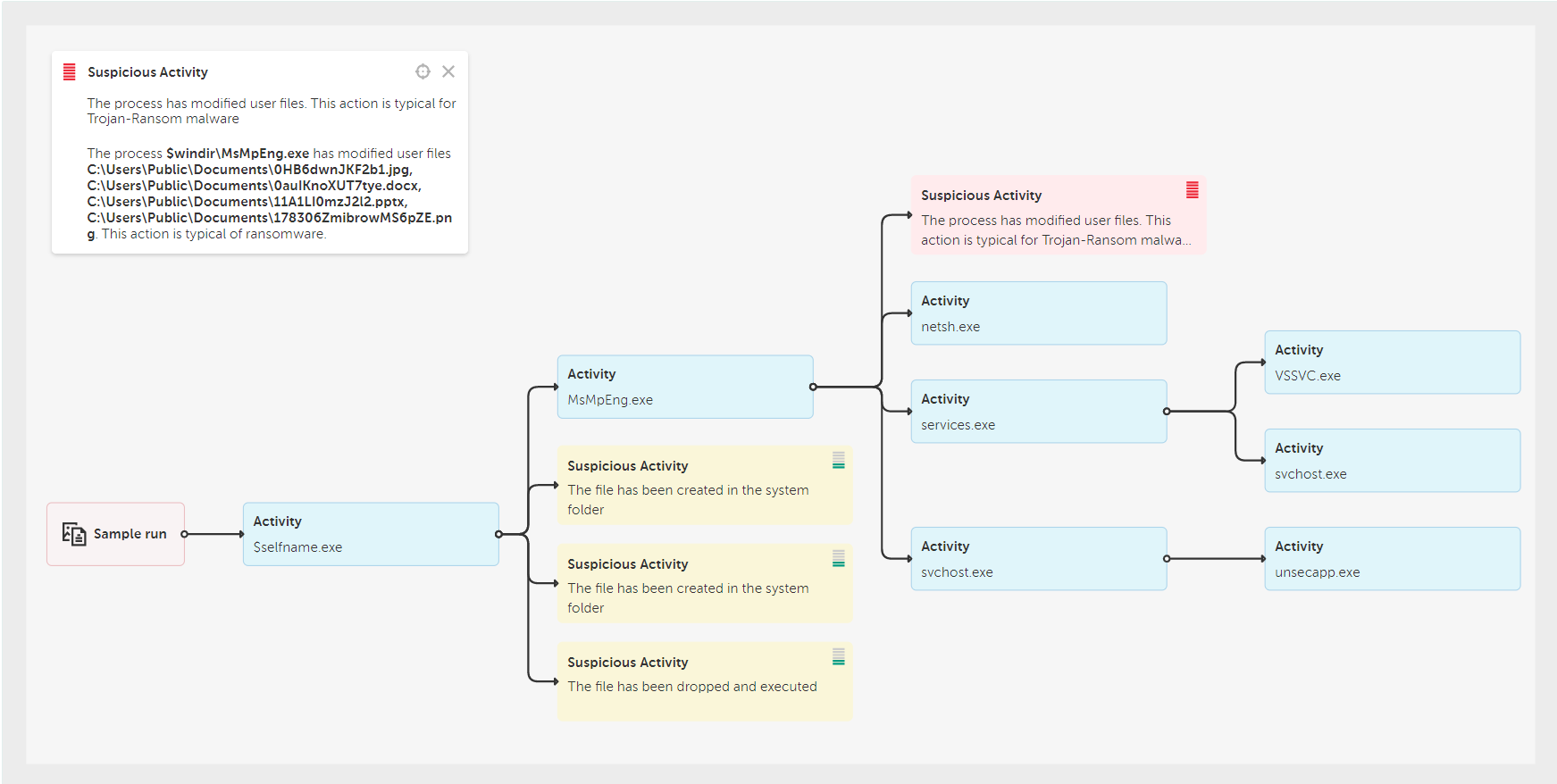
REvil ransomware attack against MSPs and its clients around the
Recomendado para você
-
 How to Play Roblox on Your PC31 março 2025
How to Play Roblox on Your PC31 março 2025 -
 Roblox android iOS apk download for free-TapTap31 março 2025
Roblox android iOS apk download for free-TapTap31 março 2025 -
Phantom Forces PC - Roblox31 março 2025
-
 Pin em Roblox Hack 202131 março 2025
Pin em Roblox Hack 202131 março 2025 -
 Hack roblox download celular31 março 2025
Hack roblox download celular31 março 2025 -
 hacker roblox download31 março 2025
hacker roblox download31 março 2025 -
Spring Update] Hack Pet Simulator X! - Roblox31 março 2025
-
 roblox mod menu mobile update 20|TikTok Search31 março 2025
roblox mod menu mobile update 20|TikTok Search31 março 2025 -
 Roblox Hack Roblox pictures, Roblox, Ios games31 março 2025
Roblox Hack Roblox pictures, Roblox, Ios games31 março 2025 -
 Stream Roblox Fluxus APK: Download and Play Roblox with Unlimited Features from Tara Sheldon31 março 2025
Stream Roblox Fluxus APK: Download and Play Roblox with Unlimited Features from Tara Sheldon31 março 2025
você pode gostar
-
 Wrath of Man (2021) - IMDb31 março 2025
Wrath of Man (2021) - IMDb31 março 2025 -
Famosas Sem Maquiagem CANAL FAMOSOS PARA SEMPRE #famosas #maquiagem @t31 março 2025
-
 Animador da BioWare lança curta incrível de Dante's Inferno - Critical Hits31 março 2025
Animador da BioWare lança curta incrível de Dante's Inferno - Critical Hits31 março 2025 -
 Dino Run 2 Roster by dinorun2 on DeviantArt31 março 2025
Dino Run 2 Roster by dinorun2 on DeviantArt31 março 2025 -
 HUGE FREE STEAM PC GAME REVEALED - COUNTER STRIKE 2 IS COMING SOON!31 março 2025
HUGE FREE STEAM PC GAME REVEALED - COUNTER STRIKE 2 IS COMING SOON!31 março 2025 -
 GTA 5 (Grand Theft Auto V): Guia completo : Retomada de Posse31 março 2025
GTA 5 (Grand Theft Auto V): Guia completo : Retomada de Posse31 março 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/3/w/cAyzetQPCwhBHBI5ycvg/adventure-5.png) Riot lança novos jogos e anuncia mais títulos do universo de LOL31 março 2025
Riot lança novos jogos e anuncia mais títulos do universo de LOL31 março 2025 -
 Call of Duty: Modern Warfare (2019) - Internet Movie Firearms Database - Guns in Movies, TV and Video Games31 março 2025
Call of Duty: Modern Warfare (2019) - Internet Movie Firearms Database - Guns in Movies, TV and Video Games31 março 2025 -
 PlayStation 5 pode receber integração com Discord - Game Arena31 março 2025
PlayStation 5 pode receber integração com Discord - Game Arena31 março 2025 -
 Knocked Loose surprise everyone, release 'Mistakes Like Fractures' 7 EP on Pure Noise Records — TIACP31 março 2025
Knocked Loose surprise everyone, release 'Mistakes Like Fractures' 7 EP on Pure Noise Records — TIACP31 março 2025

![Spring Update] Hack Pet Simulator X! - Roblox](https://tr.rbxcdn.com/e10271b17ca3d33b5631fb6590524b25/500/280/Image/Jpeg)
