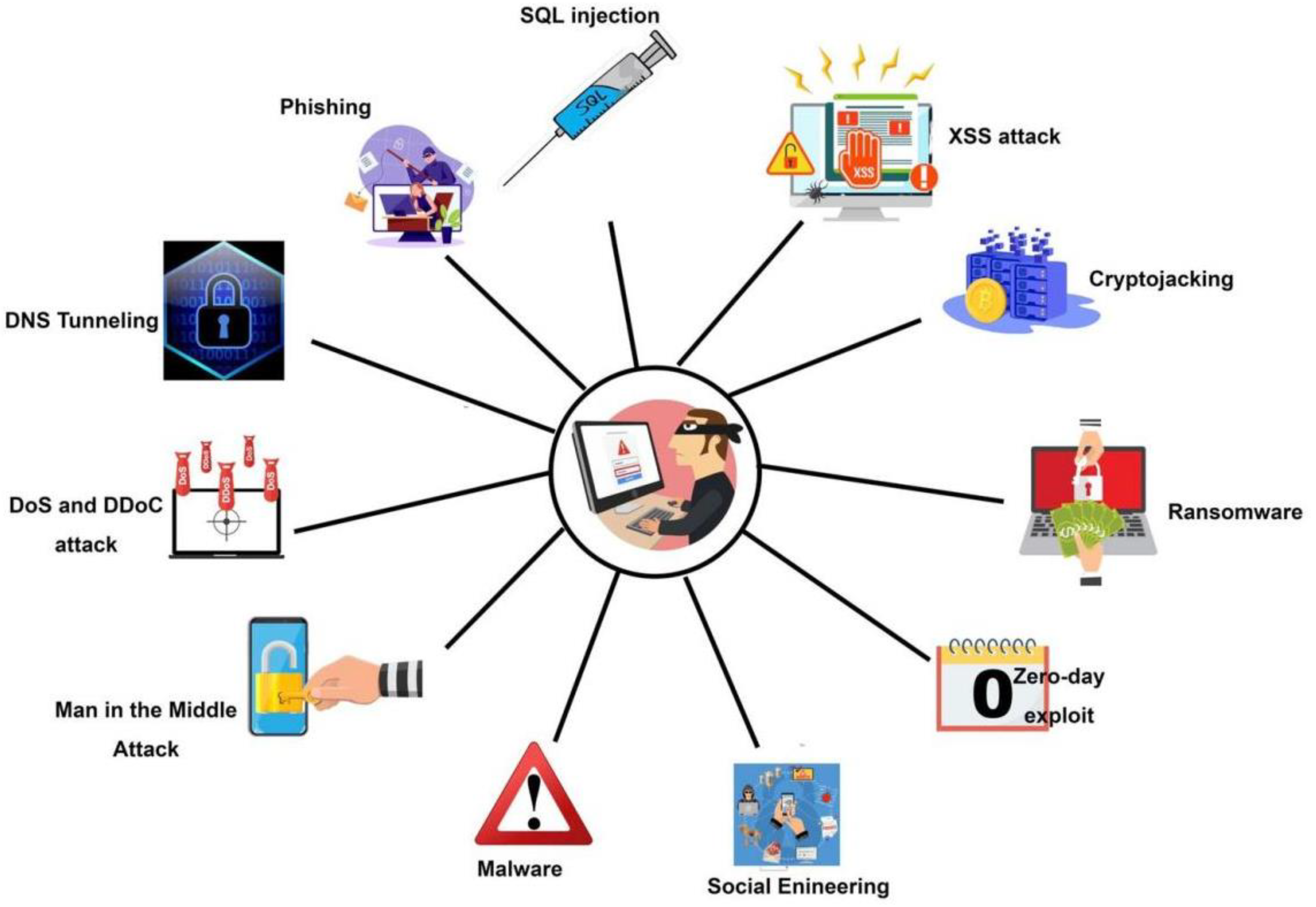
Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 28 março 2025

How AI is shaping malware analysis ~ VirusTotal Blog

Why Do You Need a Malware Sandbox? - Cyber Defense Magazine
Symmetry, Free Full-Text
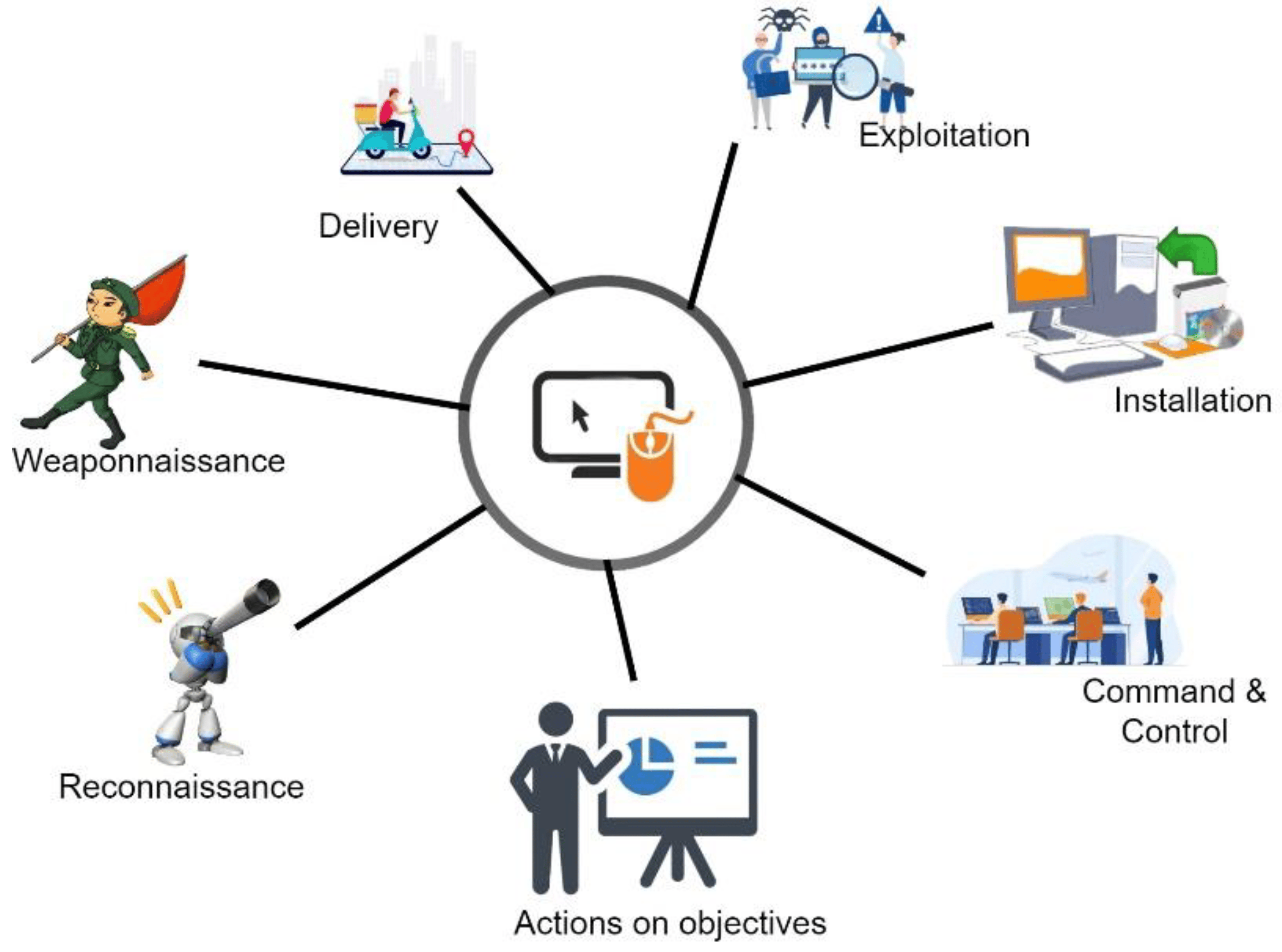
Symmetry, Free Full-Text

Malware Detection & Top Techniques Today
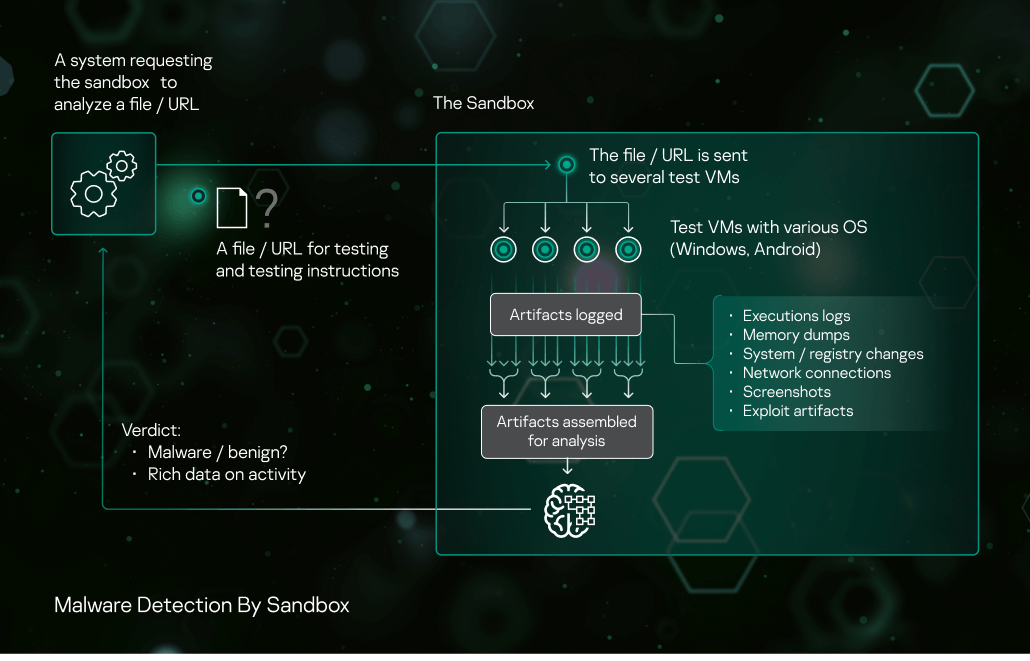
Sandbox Kaspersky
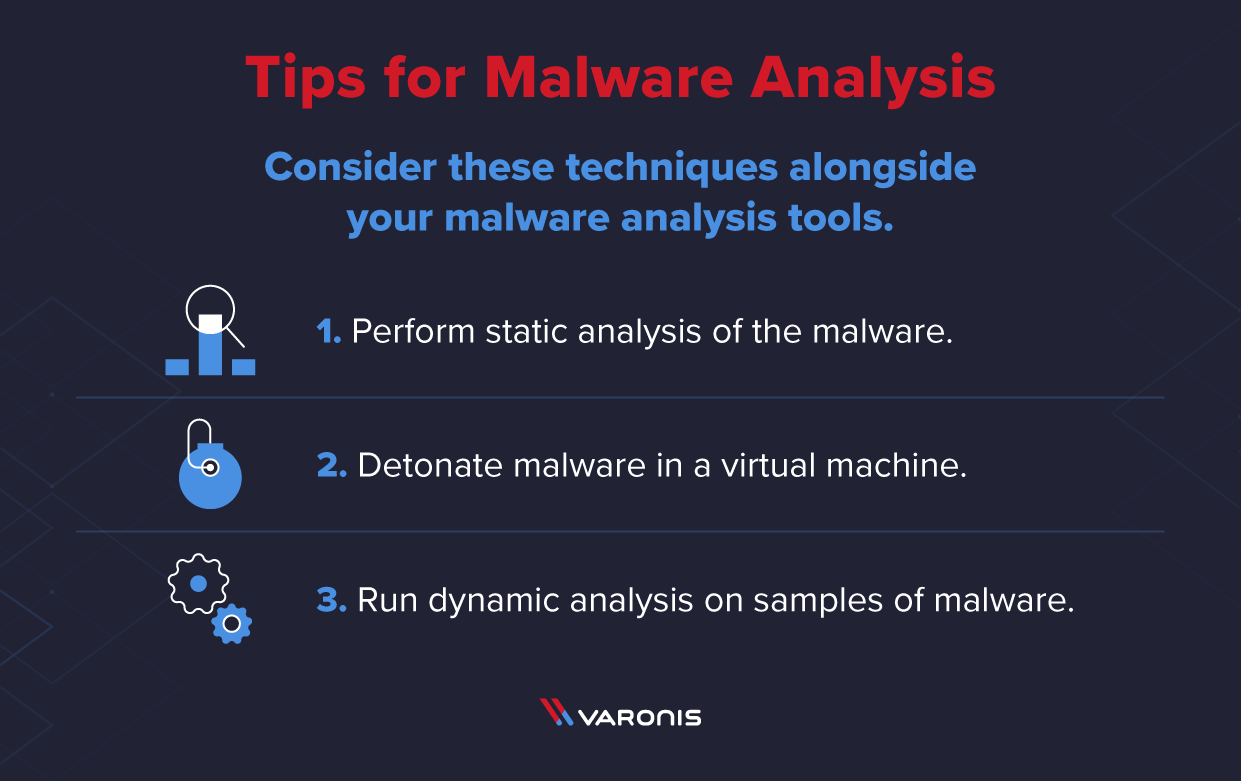
11 Best Malware Analysis Tools and Their Features

Malware Analysis - What is, Benefits & Types (Easily Explained)

7 Benefits Of Dynamic Malware Analysis

Malware Analysis and Reverse Engineering, by Ensar Seker
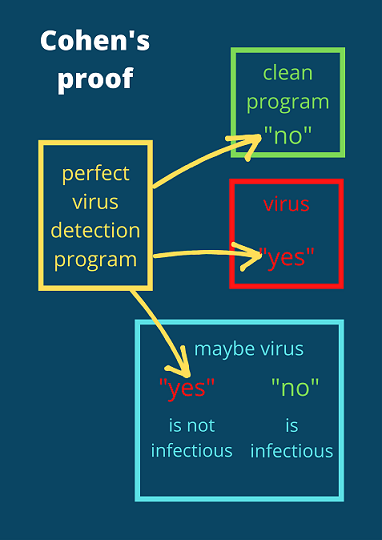
The real reason why malware detection is hard
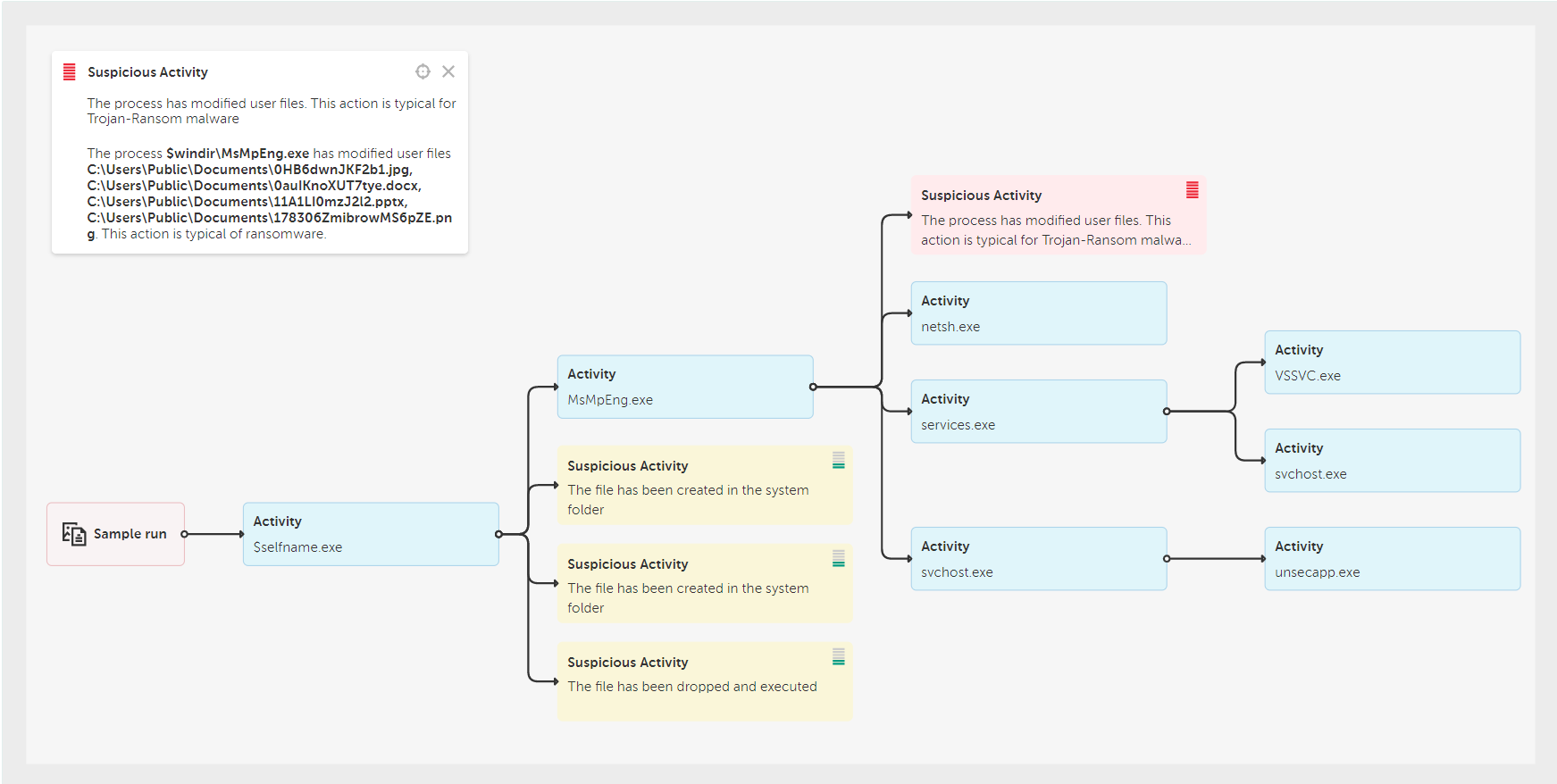
REvil ransomware attack against MSPs and its clients around the
Recomendado para você
-
 Show Your Public IP - Restreamer28 março 2025
Show Your Public IP - Restreamer28 março 2025 -
![🔴LIVE] How to know my Local PC IP address?](https://i.ytimg.com/vi/HbDJUHhXKhg/maxresdefault.jpg) 🔴LIVE] How to know my Local PC IP address?28 março 2025
🔴LIVE] How to know my Local PC IP address?28 março 2025 -
 Block ads on all your devices using pfSense, Squid & SquidGuard28 março 2025
Block ads on all your devices using pfSense, Squid & SquidGuard28 março 2025 -
USGPRO4: 'The gateway is unable to connect to the Internet' - but it is28 março 2025
-
 Port Scanner - an overview28 março 2025
Port Scanner - an overview28 março 2025 -
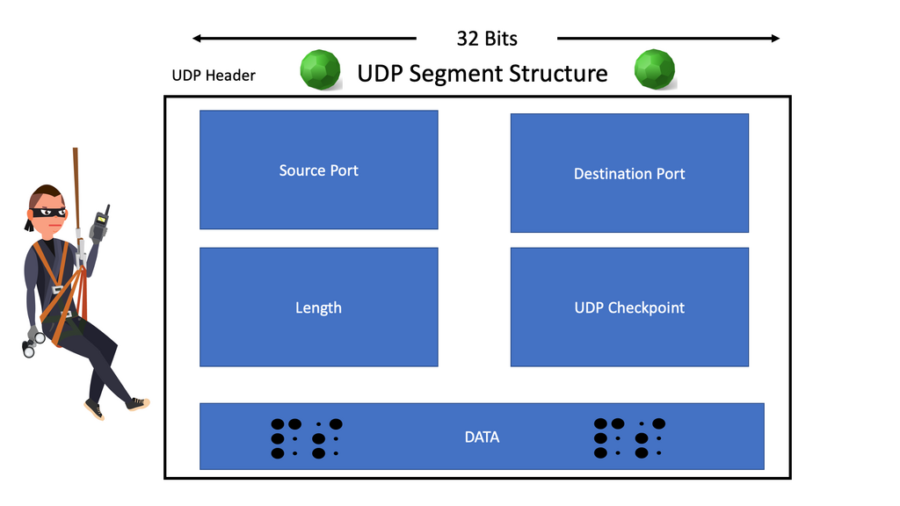 UDP Scan28 março 2025
UDP Scan28 março 2025 -
 LC EP1: TP Link ER-605/ER-7206 , OC-200, SG-2210P, EAP-235 Omada & SDN Out-of-Box Experience28 março 2025
LC EP1: TP Link ER-605/ER-7206 , OC-200, SG-2210P, EAP-235 Omada & SDN Out-of-Box Experience28 março 2025 -
 LIVE from Radiance Apr. 21, 2023 - The Panama Canal - Canal au Niveau de la Mer - Page 14 - Royal Caribbean International - Cruise Critic Community28 março 2025
LIVE from Radiance Apr. 21, 2023 - The Panama Canal - Canal au Niveau de la Mer - Page 14 - Royal Caribbean International - Cruise Critic Community28 março 2025 -
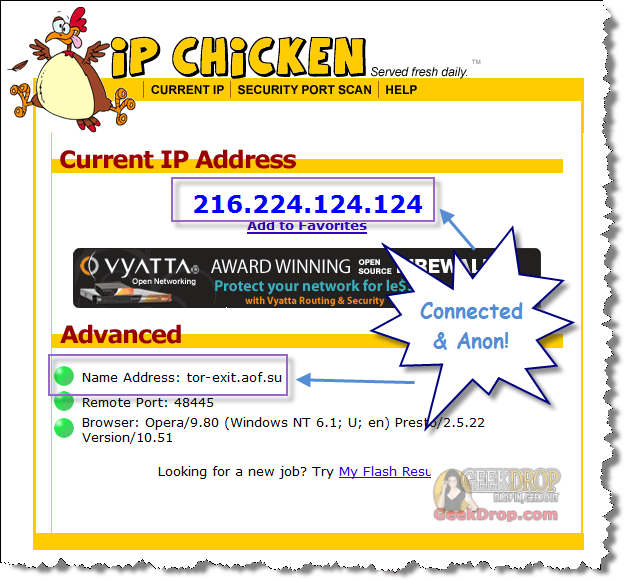 How To Use Tor With Opera Web Browser (With Polipo) For Beginners28 março 2025
How To Use Tor With Opera Web Browser (With Polipo) For Beginners28 março 2025 -
 Hacking Package Pickup28 março 2025
Hacking Package Pickup28 março 2025
você pode gostar
-
 Gear 5 Luffy GIF28 março 2025
Gear 5 Luffy GIF28 março 2025 -
 Fly or Die - Free Play & No Download28 março 2025
Fly or Die - Free Play & No Download28 março 2025 -
Titanfall® 2: Northstar Prime Price28 março 2025
-
 NEW* ALL WORKING CODES FOR FRUIT WARRIORS IN 2023! ROBLOX FRUIT WARRIORS CODES28 março 2025
NEW* ALL WORKING CODES FOR FRUIT WARRIORS IN 2023! ROBLOX FRUIT WARRIORS CODES28 março 2025 -
 Meloetta, Trovões Perdidos, Banco de Dados de Cards do Estampas Ilustradas28 março 2025
Meloetta, Trovões Perdidos, Banco de Dados de Cards do Estampas Ilustradas28 março 2025 -
Checkmate in 3 Moves PDF, PDF, Abstract Strategy Games28 março 2025
-
 Sailor Moon Crystal - OFFICIAL English Subtitled Trailer - Starts 7/5/1428 março 2025
Sailor Moon Crystal - OFFICIAL English Subtitled Trailer - Starts 7/5/1428 março 2025 -
 Wesley Safadão chora compulsivamente e Xand Avião passa mal em28 março 2025
Wesley Safadão chora compulsivamente e Xand Avião passa mal em28 março 2025 -
 The Walking Dead: Telltale Games Fan Casting28 março 2025
The Walking Dead: Telltale Games Fan Casting28 março 2025 -
 Cursed emoji Greeting Card for Sale by PedestrianWalk28 março 2025
Cursed emoji Greeting Card for Sale by PedestrianWalk28 março 2025