Malware analysis Malicious activity
Por um escritor misterioso
Last updated 31 março 2025

Malware Analysis: Steps & Examples - CrowdStrike

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

What is Malware? Definition, Types, Prevention - TechTarget
116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems

StopRansomware: Rhysida Ransomware

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
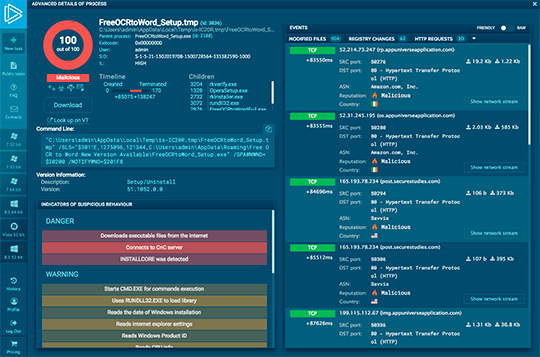
Interactive Online Malware Sandbox

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike

StopRansomware: Rhysida Ransomware

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware analysis index.html Malicious activity
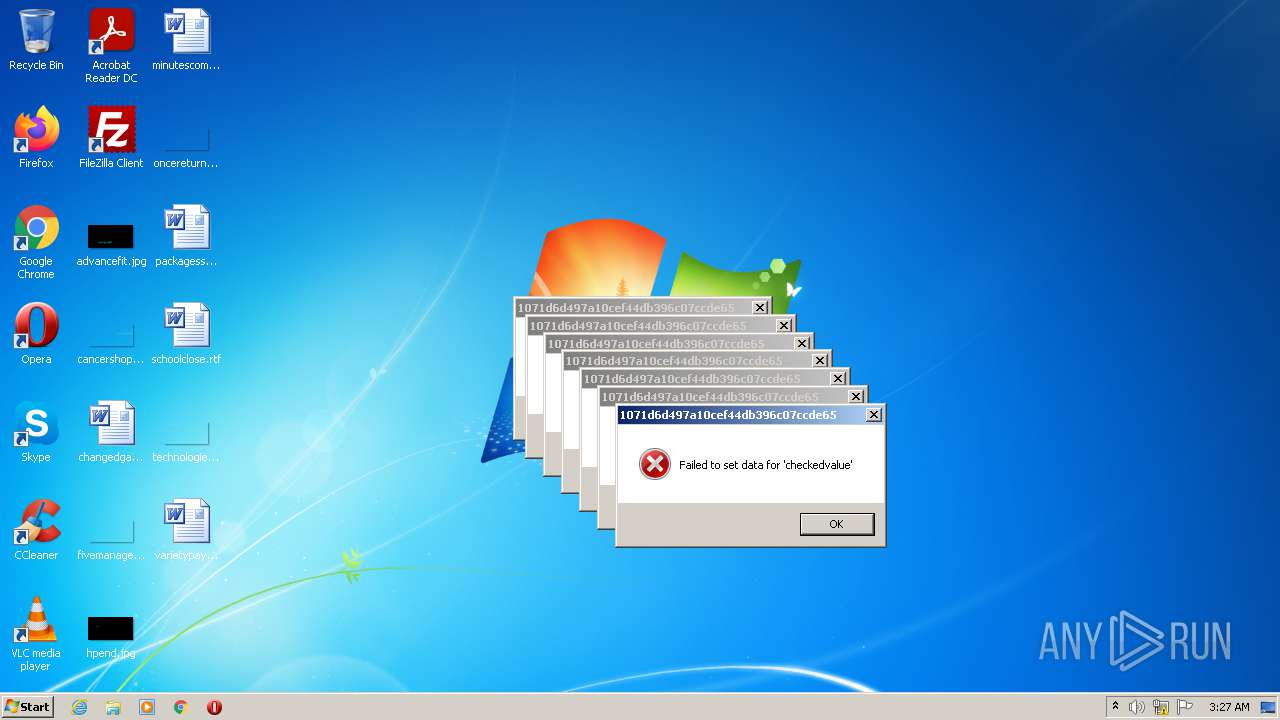
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
Recomendado para você
-
 Grand Theft Auto V Launcher by lordikman file - ModDB31 março 2025
Grand Theft Auto V Launcher by lordikman file - ModDB31 março 2025 -
 Gta 5 Pc 3dm Crack V5 Download31 março 2025
Gta 5 Pc 3dm Crack V5 Download31 março 2025 -
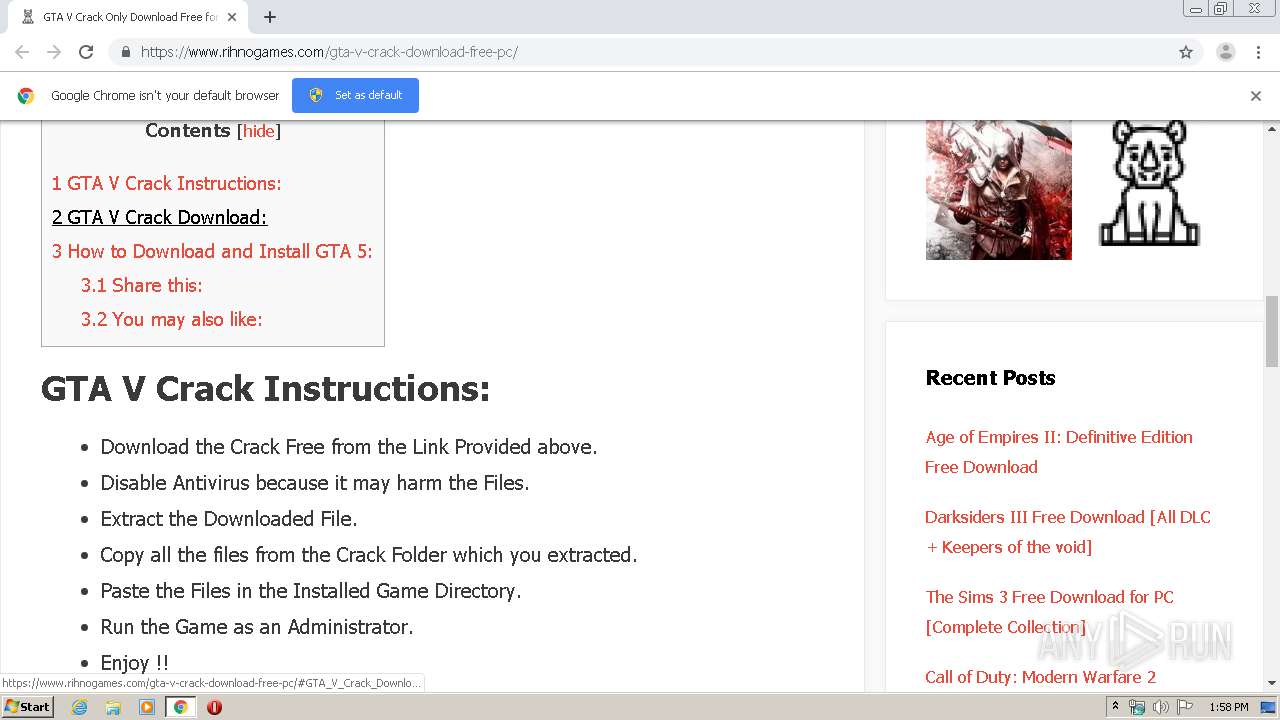
![GTA 5 Crack [Game Fix] - Direct Download {PC} (Latest)](https://i0.wp.com/activationkey.org/wp-content/uploads/2020/04/Grand-Theft-Auto-V-RockStar-500x600-1.jpg?resize=260%2C302&ssl=1) GTA 5 Crack [Game Fix] - Direct Download {PC} (Latest)31 março 2025
GTA 5 Crack [Game Fix] - Direct Download {PC} (Latest)31 março 2025 -
Grand Theft Auto V GTA5 FANS31 março 2025
-
 Download New crack from VicemanUral for GTA 131 março 2025
Download New crack from VicemanUral for GTA 131 março 2025 -
 COVERS.BOX.SK ::: Gta 5 (2013) XBOX 360 - high quality DVD31 março 2025
COVERS.BOX.SK ::: Gta 5 (2013) XBOX 360 - high quality DVD31 março 2025 -
 Tải Game GTA V - Grand Theft Auto V Việt Hóa - Download Full PC Free31 março 2025
Tải Game GTA V - Grand Theft Auto V Việt Hóa - Download Full PC Free31 março 2025 -
 Download Franklin Clinton from GTA 5 for GTA Vice City31 março 2025
Download Franklin Clinton from GTA 5 for GTA Vice City31 março 2025 -
 Pin on Free Softwares31 março 2025
Pin on Free Softwares31 março 2025 -
 GTA 5 Cracked PC Full Unlocked Version Download Online Multiplayer31 março 2025
GTA 5 Cracked PC Full Unlocked Version Download Online Multiplayer31 março 2025
você pode gostar
-
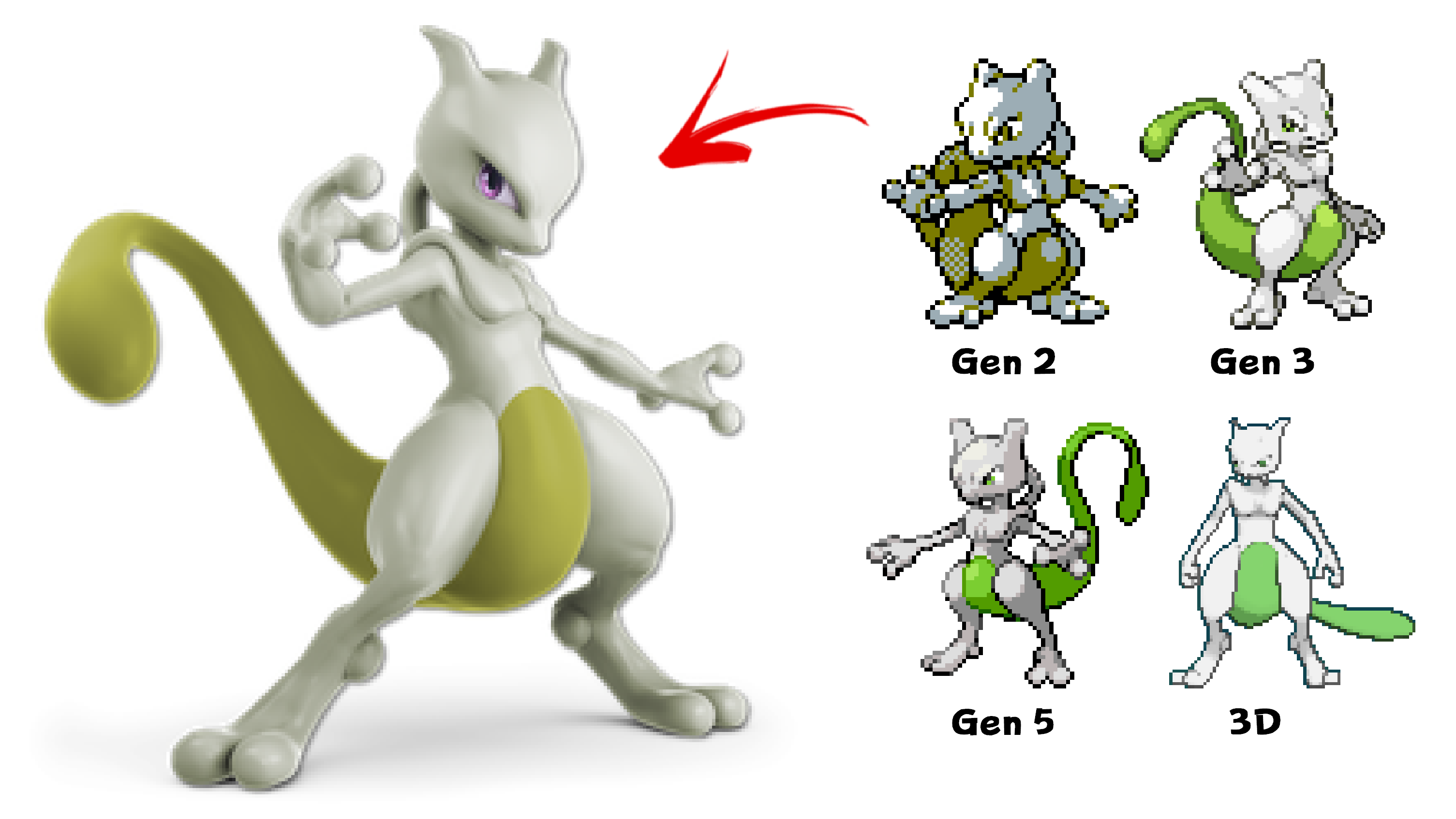
Dr. Lava on X: Banished to Smash: Shiny Mewtwo was originally yellow, but later got changed to green. Yellow Mewtwo no longer exists in the Pokemon series, but there's still one place31 março 2025
-
 Dias & Wilson Rivals - runthefutmarket on Twitch31 março 2025
Dias & Wilson Rivals - runthefutmarket on Twitch31 março 2025 -
 Jogo Gangorra De Sapos Sapinhos Mantenha O Equilíbrio - Alfabay - Cubo Mágico - Quebra Cabeças - A loja de Profissionais e Colecionadores!31 março 2025
Jogo Gangorra De Sapos Sapinhos Mantenha O Equilíbrio - Alfabay - Cubo Mágico - Quebra Cabeças - A loja de Profissionais e Colecionadores!31 março 2025 -
![ArtStation - Los Santos Vagos [Restoration]](https://cdna.artstation.com/p/assets/images/images/067/665/948/large/anastasia-dungeeva-2a.jpg?1695911826) ArtStation - Los Santos Vagos [Restoration]31 março 2025
ArtStation - Los Santos Vagos [Restoration]31 março 2025 -
 Nike Air Force 1 Low Misplaced Swooshes White Multi Men's - CK721431 março 2025
Nike Air Force 1 Low Misplaced Swooshes White Multi Men's - CK721431 março 2025 -
Rockstar Recovery Orange Energy Drink - 16 fl oz Can31 março 2025
-
 Hogwarts Legacy - Review: Hogwarts Legacy só não é excepcional31 março 2025
Hogwarts Legacy - Review: Hogwarts Legacy só não é excepcional31 março 2025 -
 Legendary pokemon coloring pages articuno31 março 2025
Legendary pokemon coloring pages articuno31 março 2025 -
 Ravena & Mutano - Jenna Aramlis - Wattpad31 março 2025
Ravena & Mutano - Jenna Aramlis - Wattpad31 março 2025 -
Character Design e dubladores dos - Dungeon ni Deai Brasil31 março 2025