Malware analysis Malicious activity
Por um escritor misterioso
Last updated 29 março 2025

AlienVault - Open Threat Exchange

Malware Analysis Framework v1.0
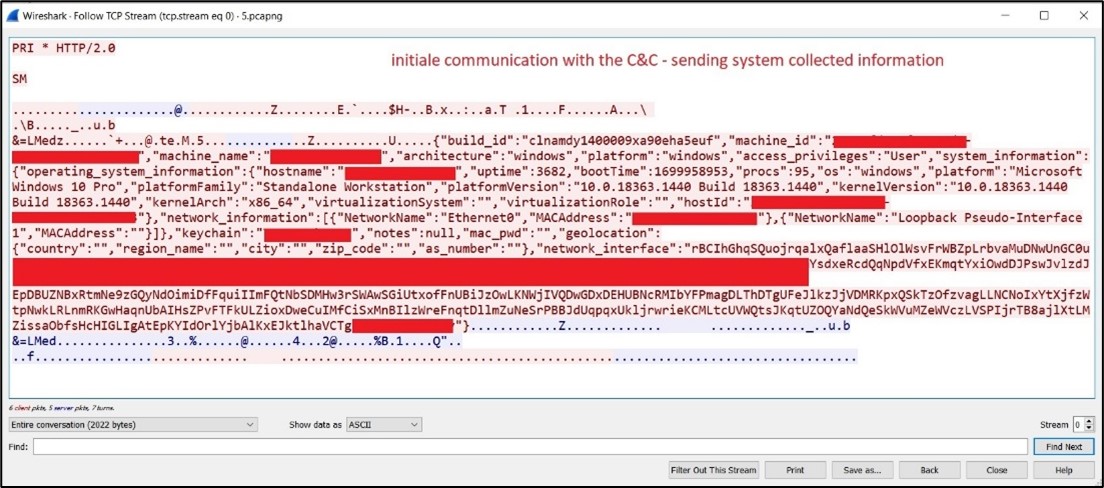
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
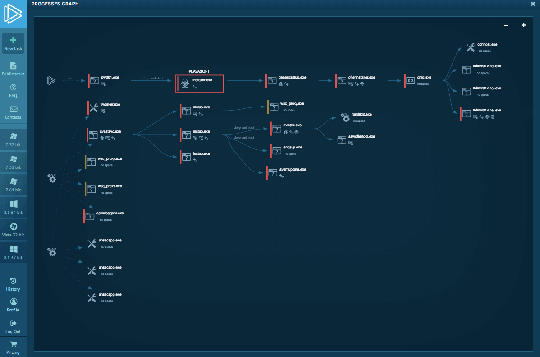
Interactive Online Malware Sandbox

Malware Analysis - What is, Benefits & Types (Easily Explained)

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security
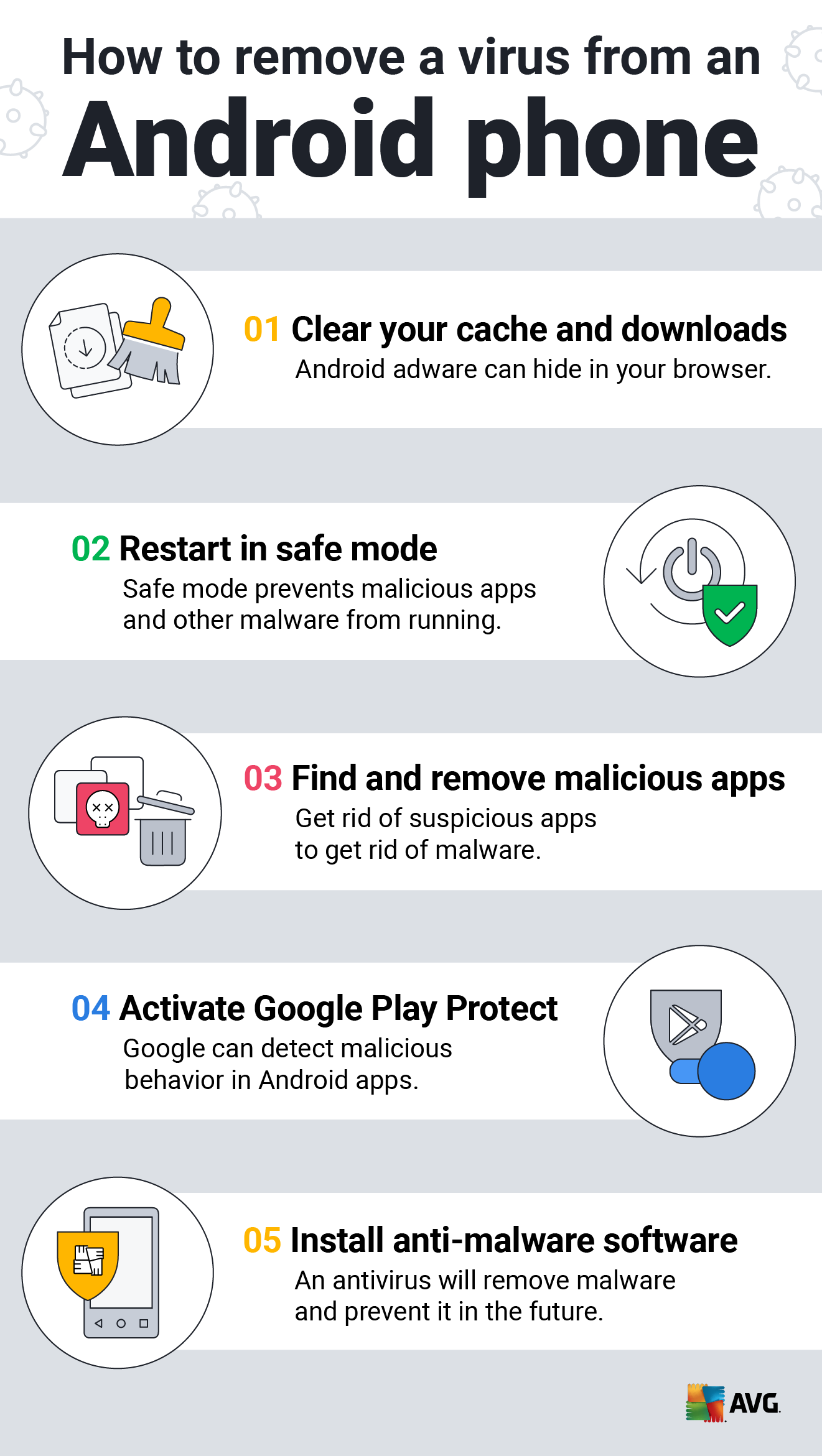
How to Clean an Android or iPhone from Viruses for Free
Malware analysis apksharp.com Malicious activity

What to Include in a Malware Analysis Report

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

A detailed analysis of the Menorah malware used by APT34
Recomendado para você
-
Search on google with me part 1: do a barrel roll@Google29 março 2025
-
BJIT on LinkedIn: Ramadan Kareem - The month of blessing29 março 2025
-
 Do a Barrel Roll 20 Times: The Ultimate Guide to Google's Fun-Filled Trick - Blog Spinel29 março 2025
Do a Barrel Roll 20 Times: The Ultimate Guide to Google's Fun-Filled Trick - Blog Spinel29 março 2025 -
 Do a Barrel Roll 100 Times Google tricks, Barrel roll, English tips29 março 2025
Do a Barrel Roll 100 Times Google tricks, Barrel roll, English tips29 março 2025 -
 10 Google Tricks for 2021 (And Bonus Google Game!)29 março 2025
10 Google Tricks for 2021 (And Bonus Google Game!)29 março 2025 -
 Do A Barrel Roll 10 Times: Is It The Best Google Trick?29 março 2025
Do A Barrel Roll 10 Times: Is It The Best Google Trick?29 março 2025 -
 Google Games: How to Play Do a Barrel Roll 20, 100, 1000, and29 março 2025
Google Games: How to Play Do a Barrel Roll 20, 100, 1000, and29 março 2025 -
 Google's hidden treasures - The Digital Studios29 março 2025
Google's hidden treasures - The Digital Studios29 março 2025 -
 So I was looking through Google to see what to look up and29 março 2025
So I was looking through Google to see what to look up and29 março 2025 -
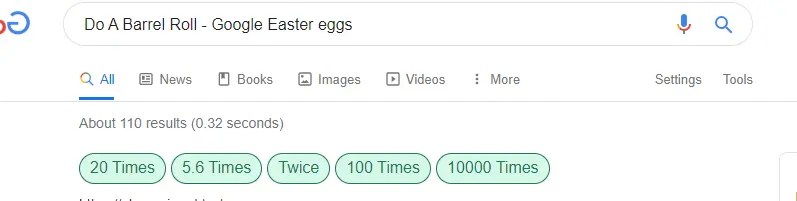 How To “Do A Barrel Roll 1 Million Times” On Google - All Tech29 março 2025
How To “Do A Barrel Roll 1 Million Times” On Google - All Tech29 março 2025
você pode gostar
-
:quality(70)/cloudfront-us-east-1.images.arcpublishing.com/metroworldnews/HOV6HK76DFGJDMIHWK3I5V7XIE.jpg) Céu permanece nublado e pode garoar em São Paulo – Metro World29 março 2025
Céu permanece nublado e pode garoar em São Paulo – Metro World29 março 2025 -
 Tank Race Codes for December 2023: Free Pets! - Try Hard Guides29 março 2025
Tank Race Codes for December 2023: Free Pets! - Try Hard Guides29 março 2025 -
 Ce a spus Leo Grozavu, după remiza cu Hermannstadt29 março 2025
Ce a spus Leo Grozavu, după remiza cu Hermannstadt29 março 2025 -
 Pokemon Go - How to evolve Galarian Slowpoke and Galarian Farfetch29 março 2025
Pokemon Go - How to evolve Galarian Slowpoke and Galarian Farfetch29 março 2025 -
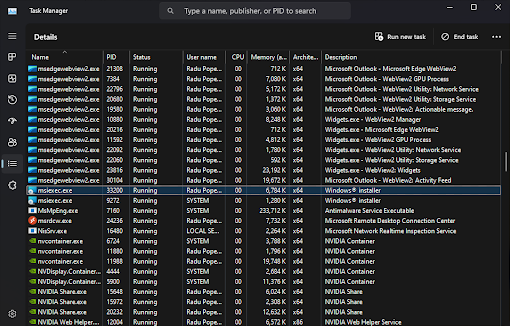 Msiexec.exe Command Line29 março 2025
Msiexec.exe Command Line29 março 2025 -
 Alimentos e Bebidas: Saquê e Bebidas a Base de Arroz na29 março 2025
Alimentos e Bebidas: Saquê e Bebidas a Base de Arroz na29 março 2025 -
 ATÉ 19.999 DIAMANTES?? COMO CHAMAR AMIGO DE VOLTA NO FREE FIRE29 março 2025
ATÉ 19.999 DIAMANTES?? COMO CHAMAR AMIGO DE VOLTA NO FREE FIRE29 março 2025 -
 Mortal Kombat Microsoft Xbox 360 Complete29 março 2025
Mortal Kombat Microsoft Xbox 360 Complete29 março 2025 -
 These were okay Nostalgic candy, Candy, Wonka shockers29 março 2025
These were okay Nostalgic candy, Candy, Wonka shockers29 março 2025 -
 Fundos Fotográficos - ColorDecor29 março 2025
Fundos Fotográficos - ColorDecor29 março 2025

