Malware analysis Malicious activity
Por um escritor misterioso
Last updated 01 abril 2025
Malware Analysis - What is, Benefits & Types (Easily Explained)

How to Do Malware Analysis?

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey

Routers Roasting on an Open Firewall: the KV-botnet Investigation

AlienVault - Open Threat Exchange

Malware Analysis Benefits Incident Response

Malware Analysis: Steps & Examples - CrowdStrike

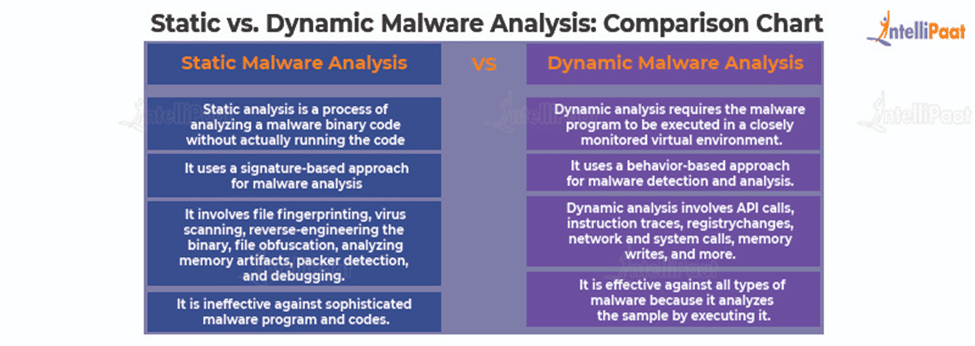
Dynamic malware analysis [34]
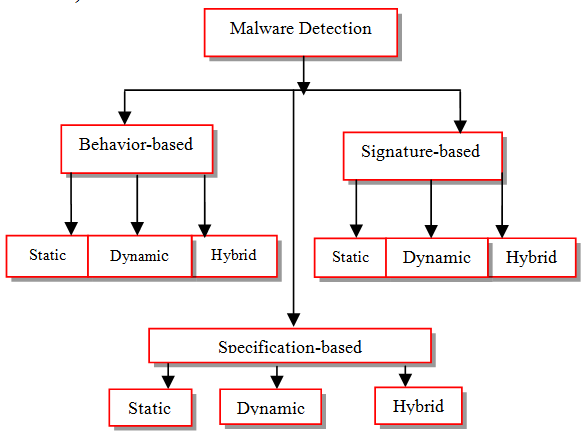
Organization of malware detection techniques (Elhadi et al., 2015
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Detail procedure of malware analysis
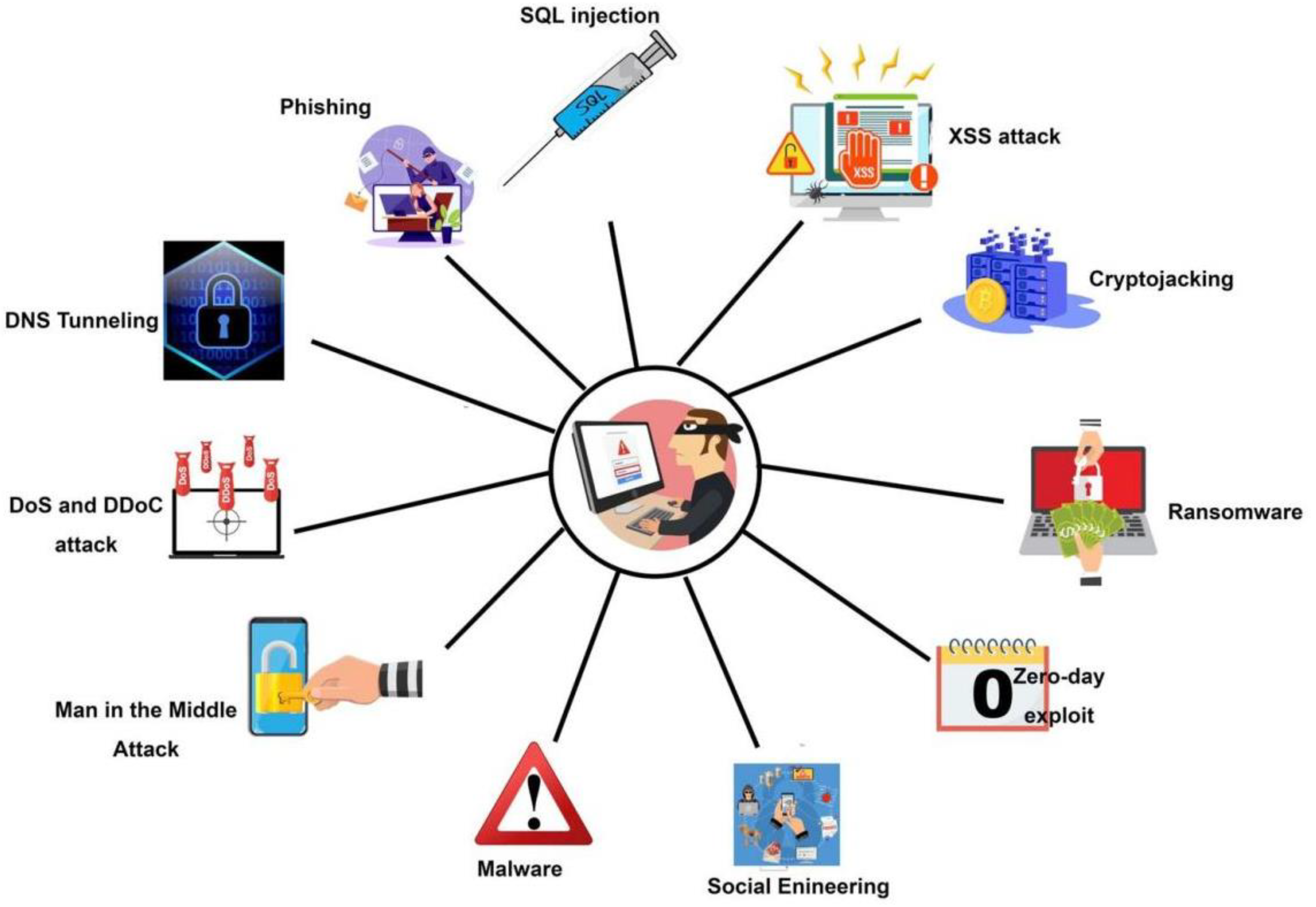
Symmetry, Free Full-Text

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
2023 Delta exploits for #videos01 abril 2025
-
roblox · GitHub Topics · GitHub01 abril 2025
-
 Conta De Executor Synapse X Para Roblox *Melhor Executor* - Others - DFG01 abril 2025
Conta De Executor Synapse X Para Roblox *Melhor Executor* - Others - DFG01 abril 2025 -
 CapCut_roblox executor no key01 abril 2025
CapCut_roblox executor no key01 abril 2025 -
 roblox moment : r/robloxhackers01 abril 2025
roblox moment : r/robloxhackers01 abril 2025 -
how to delete delta executor on roblox|TikTok Search01 abril 2025
-
 Trigon Evo (Roblox Mod)01 abril 2025
Trigon Evo (Roblox Mod)01 abril 2025 -
 why my roblox executor is not working?01 abril 2025
why my roblox executor is not working?01 abril 2025 -
_undetected-free-roblox-executor-nezur-web-version-amp-microsoft-version-preview-hqdefault.jpg) UNDETECTED FREE Roblox Executor Nezur (Web Version & Microsoft Version) from exploit injectors for roblox Watch Video01 abril 2025
UNDETECTED FREE Roblox Executor Nezur (Web Version & Microsoft Version) from exploit injectors for roblox Watch Video01 abril 2025 -
 TUTORIAL - ROBLOX EXECUTOR 2023 WEB VERSION / BYFRON BYPASS UPDATE / ROBLOX EXPLOIT KEYLESS FREE ST01 abril 2025
TUTORIAL - ROBLOX EXECUTOR 2023 WEB VERSION / BYFRON BYPASS UPDATE / ROBLOX EXPLOIT KEYLESS FREE ST01 abril 2025
você pode gostar
-
 Coritiba: Seis jogos que explicam a história do Coxa01 abril 2025
Coritiba: Seis jogos que explicam a história do Coxa01 abril 2025 -
 Toy World Magazine October 2022 by TOYWORLD MAGAZINE - Issuu01 abril 2025
Toy World Magazine October 2022 by TOYWORLD MAGAZINE - Issuu01 abril 2025 -
MoonWalker 🚀 on X: April Fools only just started and it didn't take long for me to Rick Roll most of my discord server. / X01 abril 2025
-
azul babão do roblox|TikTok Search01 abril 2025
-
 Assistir Pokemon Sun and Moon - Episódio 09 Online - Download01 abril 2025
Assistir Pokemon Sun and Moon - Episódio 09 Online - Download01 abril 2025 -
 Introducing Configure Group - Announcements - Developer Forum01 abril 2025
Introducing Configure Group - Announcements - Developer Forum01 abril 2025 -
 A história triste do espanhol que é o meme mais hilariante da Internet – NiT01 abril 2025
A história triste do espanhol que é o meme mais hilariante da Internet – NiT01 abril 2025 -
/i.s3.glbimg.com/v1/AUTH_fde5cd494fb04473a83fa5fd57ad4542/internal_photos/bs/2023/n/o/Z1EMgAQyA2llXOR0k6Qg/2021-06-02-dylan-nolte-rssqjpezn6o-unsplash.jpeg) 9 pontos para entender o que é e como funciona o jogo do bicho, Curiosidade01 abril 2025
9 pontos para entender o que é e como funciona o jogo do bicho, Curiosidade01 abril 2025 -
 MR Robot Wallpaper - wallpaper post - Imgur01 abril 2025
MR Robot Wallpaper - wallpaper post - Imgur01 abril 2025 -
 Hoje tem estreia do Brasil na Copa do Mundo Feminina, jogo é contra o Panamá – Portal Rondon01 abril 2025
Hoje tem estreia do Brasil na Copa do Mundo Feminina, jogo é contra o Panamá – Portal Rondon01 abril 2025