Malware analysis
Por um escritor misterioso
Last updated 29 março 2025

Figure .: Pros and Cons of Malware Analysis Methods

ChatGPT and Malware Analysis - ThreatMon - ThreatMon Blog

Malware Analysis: Steps & Examples - CrowdStrike

What is Malware Detection? Why Malware Threat System?
Master Reverse Engineering, Malware Analysis, Linux, Cyber Security, Ghidra,x86-64, IDA Pro, IDA Free, Assembly and NASM

Mastering Reverse Engineering & Malware Analysis | REMASM+

So You Want To Be A Malware Analyst

What is Malware Analysis? Benefits, Types, and Tools
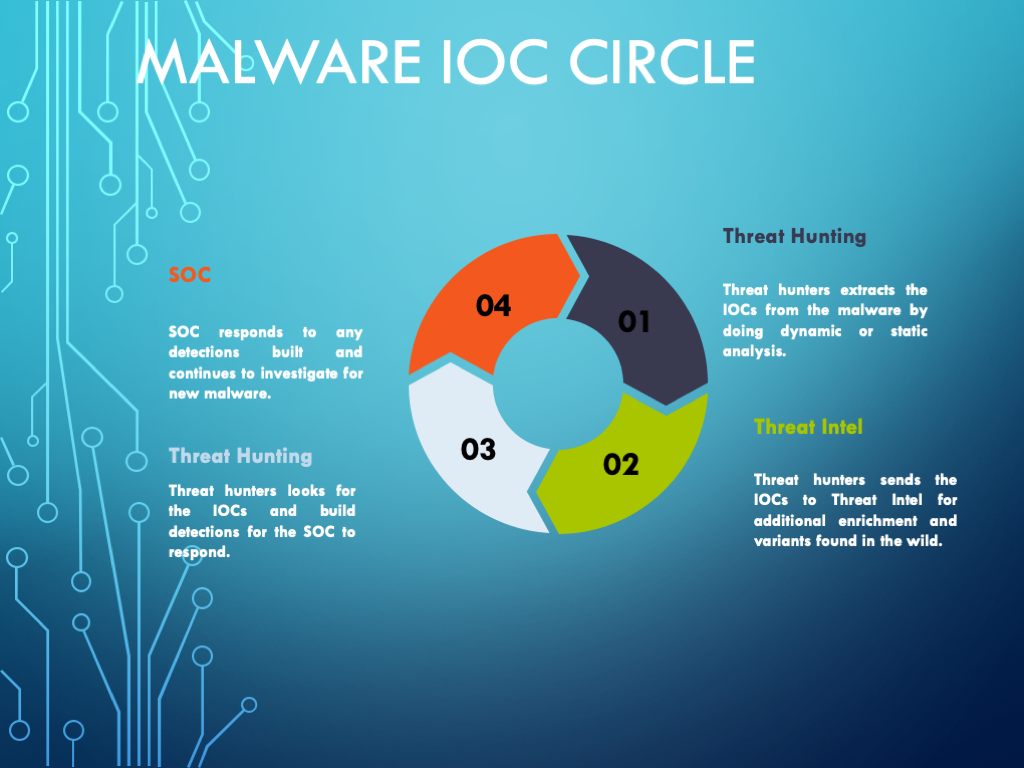
Malware Analysis Framework v1.0
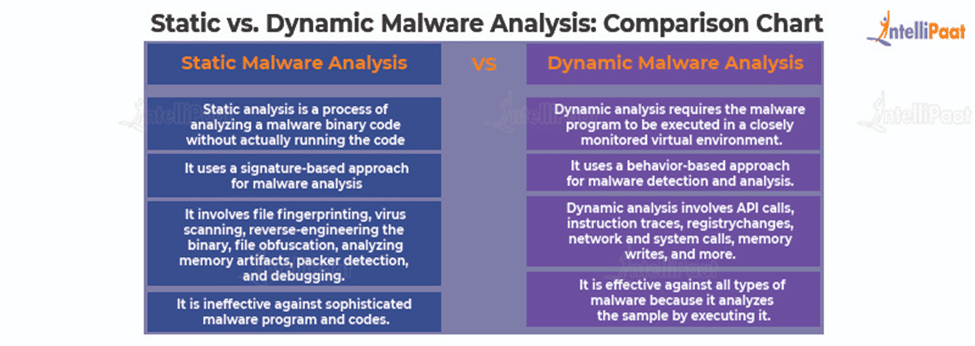
Malware Analysis - What is, Benefits & Types (Easily Explained)
Highlight, take notes, and search in the book In this edition, page numbers are just like the physical edition

Malware Analysis and Detection Engineering: A Comprehensive Approach to Detect and Analyze Modern Malware
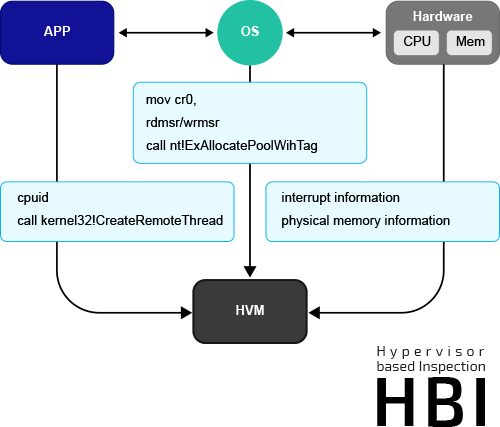
Deep Malware Analysis - Joe Sandbox Technology

How To Set Up Malware Analysis Environment? - The Sec Master

CYBER 5W

Intro to Malware Analysis: What It Is & How It Works - InfoSec

A Guide for Beginners in Malware Analysis: The Roadmap, Job Career
Recomendado para você
-
 Drawception29 março 2025
Drawception29 março 2025 -
 /watch?v=dQw4w9WgXcQ29 março 2025
/watch?v=dQw4w9WgXcQ29 março 2025 -
 r/memes29 março 2025
r/memes29 março 2025 -
dQw4w9WgXcQ - song and lyrics by Muqdisho29 março 2025
-
 python - Carriage return in QTextBrowser in PyQt5 - Stack Overflow29 março 2025
python - Carriage return in QTextBrowser in PyQt5 - Stack Overflow29 março 2025 -
 Pokemon Rick Astley 47129 março 2025
Pokemon Rick Astley 47129 março 2025 -
 r/dankmemes29 março 2025
r/dankmemes29 março 2025 -
 watch?v=dQw4w9WgXcQ - 9GAG29 março 2025
watch?v=dQw4w9WgXcQ - 9GAG29 março 2025 -
 Thor Gift (thorgift.com) - If you like it please buy some from ThorGift.com29 março 2025
Thor Gift (thorgift.com) - If you like it please buy some from ThorGift.com29 março 2025 -
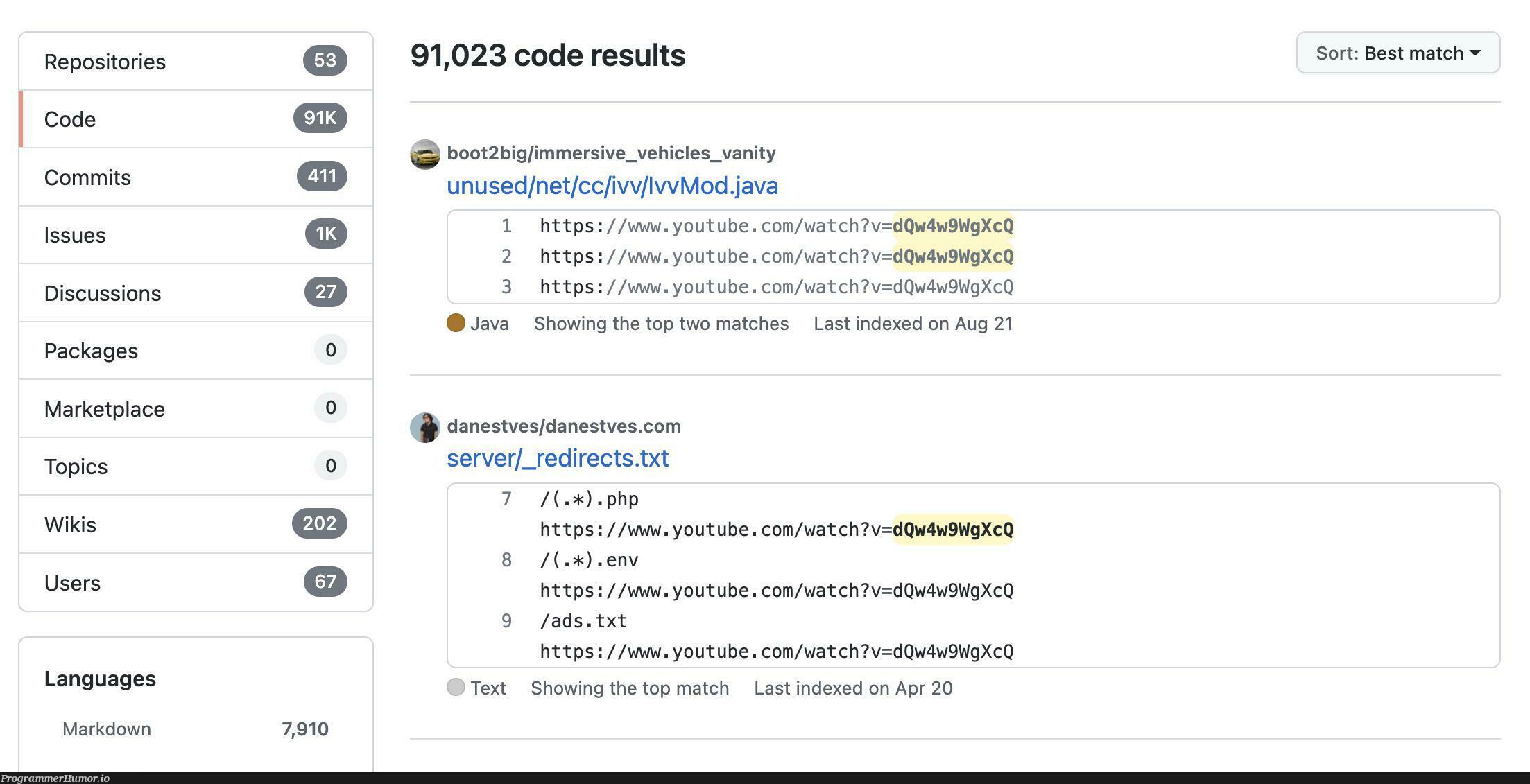 There are 91,000+ instances of the video ID “dQw4w9WgXcQ” in code on GitHub –29 março 2025
There are 91,000+ instances of the video ID “dQw4w9WgXcQ” in code on GitHub –29 março 2025
você pode gostar
-
 Sonic - O Filme é o mais visto pelos americanos em casa, diz29 março 2025
Sonic - O Filme é o mais visto pelos americanos em casa, diz29 março 2025 -
 Como apostar: empate anula aposta e ambos marcam29 março 2025
Como apostar: empate anula aposta e ambos marcam29 março 2025 -
Minecraft 1.20 APK Download grátis para Android 202329 março 2025
-
![Pin by Sayali V on 86 [Eighty Six]](https://i.pinimg.com/originals/58/03/39/5803390e76dc712fd58acc952de7ab58.jpg) Pin by Sayali V on 86 [Eighty Six]29 março 2025
Pin by Sayali V on 86 [Eighty Six]29 março 2025 -
 20 Bethesda games coming to Game Pass on Xbox, PC, and Cloud tomorrow29 março 2025
20 Bethesda games coming to Game Pass on Xbox, PC, and Cloud tomorrow29 março 2025 -
 Taylor Swift Friendship Bracelets Die Cut Sticker29 março 2025
Taylor Swift Friendship Bracelets Die Cut Sticker29 março 2025 -
 Home Decor Funny Gift 6 Kitchen Wall Art Prints Kitchenware with Sayings Unframed Farmhouse Home Office organization Signs Bar Accessories Decorations sets white house Deco Kitchen Decor (8x10)29 março 2025
Home Decor Funny Gift 6 Kitchen Wall Art Prints Kitchenware with Sayings Unframed Farmhouse Home Office organization Signs Bar Accessories Decorations sets white house Deco Kitchen Decor (8x10)29 março 2025 -
 Verification - Giratina Origin Shiny is live : r/TheSilphRoad29 março 2025
Verification - Giratina Origin Shiny is live : r/TheSilphRoad29 março 2025 -
 therm on X: YOU WIN. PERFECT! ↳Cammy Fortnite Outfit #Fortnite29 março 2025
therm on X: YOU WIN. PERFECT! ↳Cammy Fortnite Outfit #Fortnite29 março 2025 -
 Rex Clinkscales Wins 2012-13 WSOP Circuit Harrah's Philadelphia Main Event29 março 2025
Rex Clinkscales Wins 2012-13 WSOP Circuit Harrah's Philadelphia Main Event29 março 2025
