GootBot - Gootloader's new approach to post-exploitation
Por um escritor misterioso
Last updated 29 março 2025
IBM X-Force discovered a new variant of Gootloader — the "GootBot" implant. Learn more about this and how to combat it.

DONATO VIGGIANO on LinkedIn: Attackers use JavaScript URLs, API forms and more to scam users in popular…
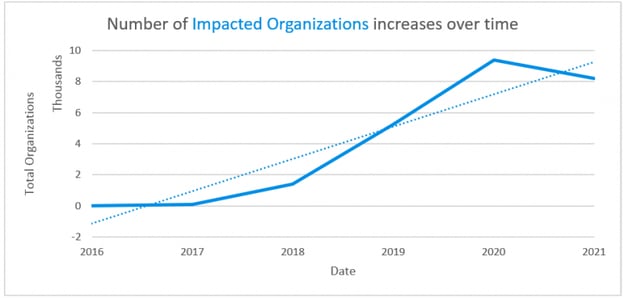
The Rise of Post-Exploitation Attack Frameworks

Three Lessons from the Target Hack of Encrypted PIN Data - Security Intelligence

Gootbot: A new post-exploitation implant for lateral movement

How human behavior research informs security strategies: Kai Roer explains., CyberCureME - Cyber Security Marketplace posted on the topic

The New Post-Exploitation framework- Exfiltrator-22 - The Sec Master

CyberCureME - Cyber Security Marketplace on LinkedIn: Thales CTE-RWP protects critical files and folders from ransomware…

Mitigating CVE-2023-3595 and CVE-2023-3596 Impacting Rockwell Automation ControlLogix Firmware : r/worldTechnology

Two Important Lessons From the Ashley Madison Breach
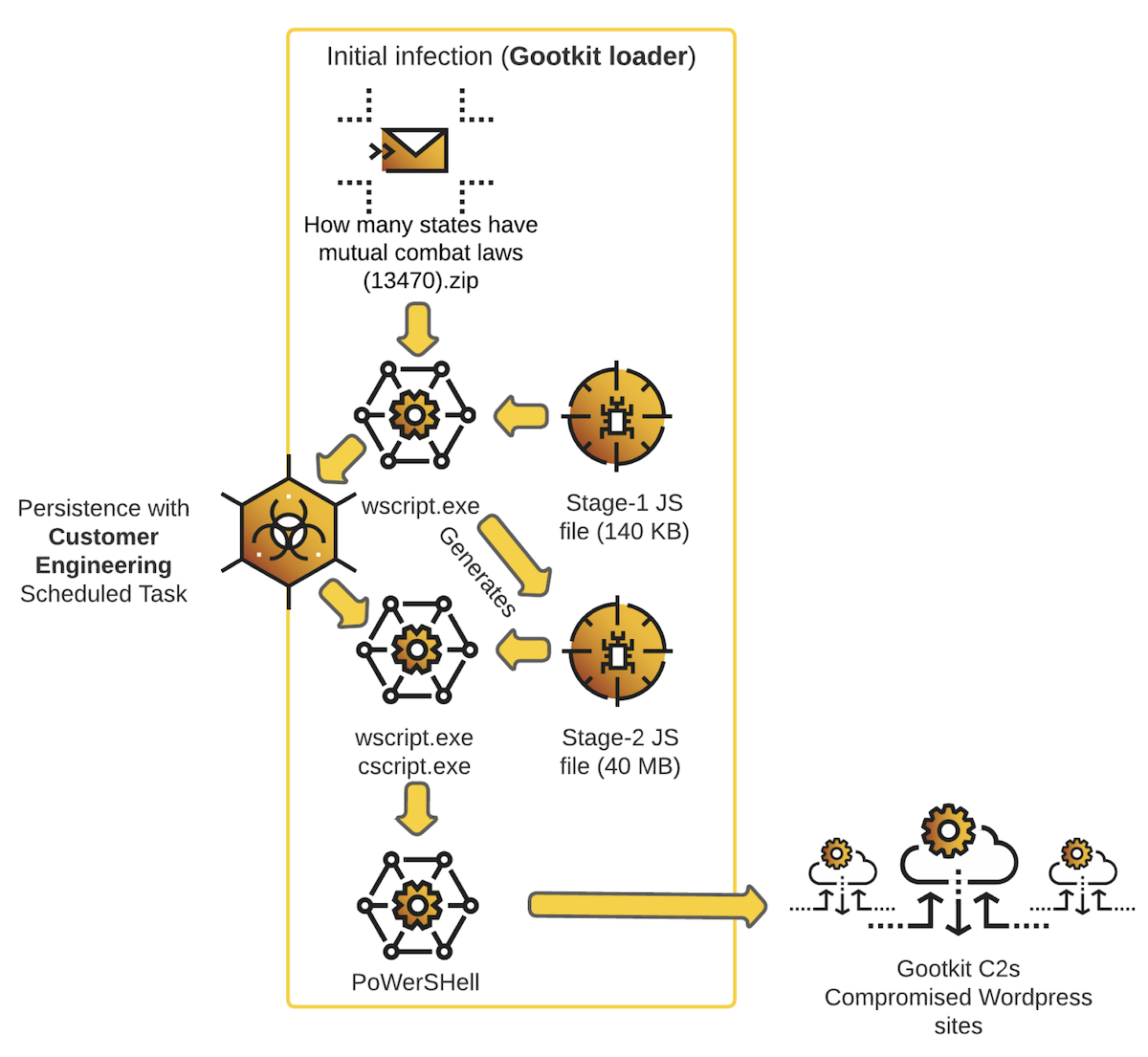
A Deep Dive Into the Growing GootLoader Threat - SecurityWeek
Recomendado para você
-
Bbc android iplayer download29 março 2025
-
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!29 março 2025
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!29 março 2025 -
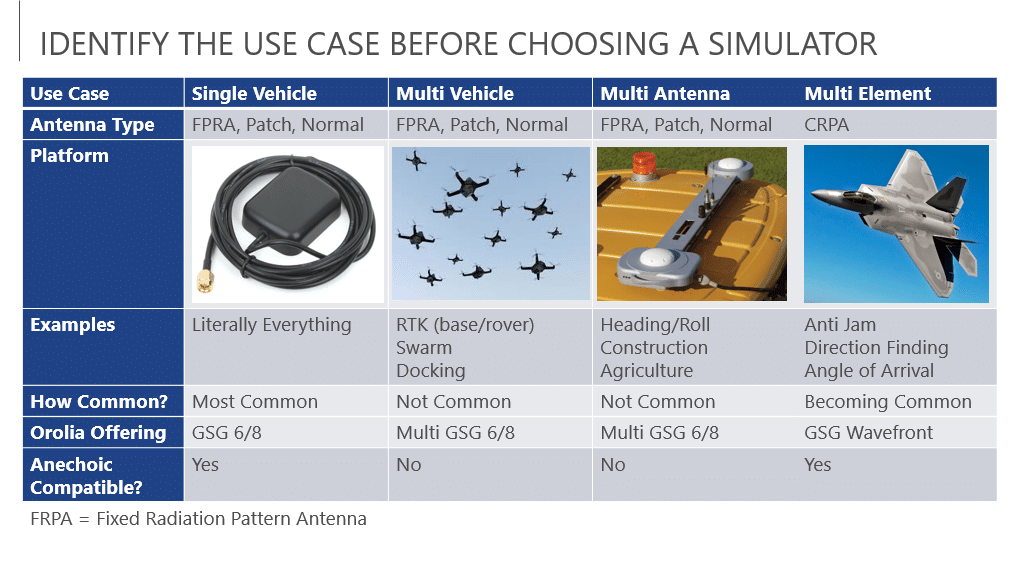 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing29 março 2025
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing29 março 2025 -
 1PC In-line Fan Simulator Spoofer Remover for AntiMiner T9 T9 for29 março 2025
1PC In-line Fan Simulator Spoofer Remover for AntiMiner T9 T9 for29 março 2025 -
Raj Echambadi on LinkedIn: Illinois Tech's CARNATIONS Receives $1029 março 2025
-
 Beware of Spoof Websites - RCB Bank29 março 2025
Beware of Spoof Websites - RCB Bank29 março 2025 -
Red Engine Un Ban29 março 2025
-
 US7814533B2 - Secure customer interface for Web based data management - Google Patents29 março 2025
US7814533B2 - Secure customer interface for Web based data management - Google Patents29 março 2025 -
 redENGINE – FiveM Spoofer29 março 2025
redENGINE – FiveM Spoofer29 março 2025 -
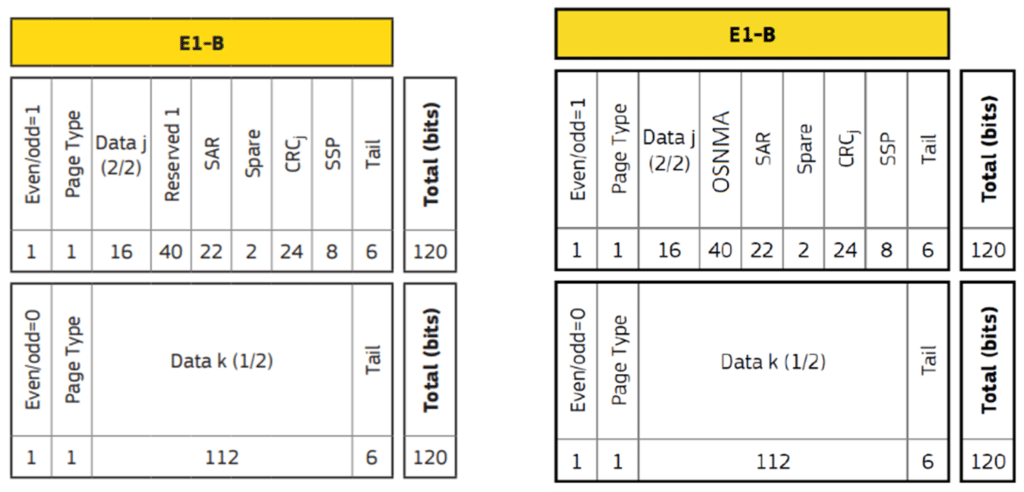 Testing a Receiver's Galileo OS-NMA Capability Using Skydel29 março 2025
Testing a Receiver's Galileo OS-NMA Capability Using Skydel29 março 2025
você pode gostar
-
 Concurso PM BA Soldado - História29 março 2025
Concurso PM BA Soldado - História29 março 2025 -
kurfi on X: day 4 of making sapnap skins! 🔥 this time29 março 2025
-
 Professora do UniBrasil é homenageada29 março 2025
Professora do UniBrasil é homenageada29 março 2025 -
 Bolo do Minecraft, Como Fazer Bolo de Aniversário do Minecraft29 março 2025
Bolo do Minecraft, Como Fazer Bolo de Aniversário do Minecraft29 março 2025 -
 Portal: Forbidden Testing Tracks on Steam29 março 2025
Portal: Forbidden Testing Tracks on Steam29 março 2025 -
 VTuber Maker Bring VTuber Avatar to Life29 março 2025
VTuber Maker Bring VTuber Avatar to Life29 março 2025 -
 BLOG DO ROBERTO ALMEIDA: A INCRÍVEL HISTÓRIA DE PHIONA MUTESI29 março 2025
BLOG DO ROBERTO ALMEIDA: A INCRÍVEL HISTÓRIA DE PHIONA MUTESI29 março 2025 -
 garfield jogo no friv29 março 2025
garfield jogo no friv29 março 2025 -
Dishonored: Dunwall City Trials PC Steam Downloadable Content29 março 2025
-
 10 MELHORES Jogos de fuga e escape em Lisboa - Tripadvisor29 março 2025
10 MELHORES Jogos de fuga e escape em Lisboa - Tripadvisor29 março 2025



