DigitalResidue's Forensics: Malware Incident Response pt. 2. (Collecting Volatile and Non-Volatile data)
Por um escritor misterioso
Last updated 28 março 2025
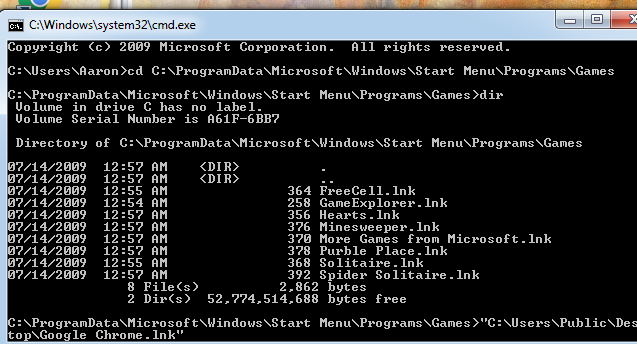
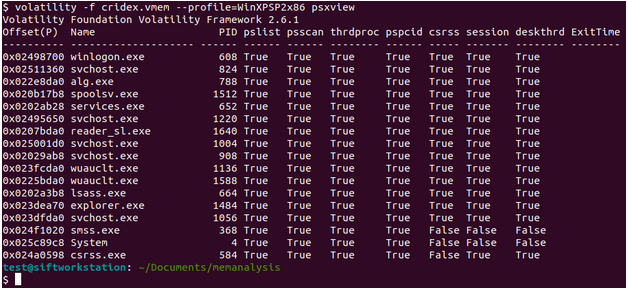
Memory CTF with Volatility Part 1 – Westoahu Cybersecurity

DigitalResidue's Forensics

DigitalResidue's Forensics: Malware Incident Response pt. 2. (Collecting Volatile and Non-Volatile data)

Incident Response - The order of volatility

Distributed forensics and incident response in the enterprise - ScienceDirect

DigitalResidue's Forensics
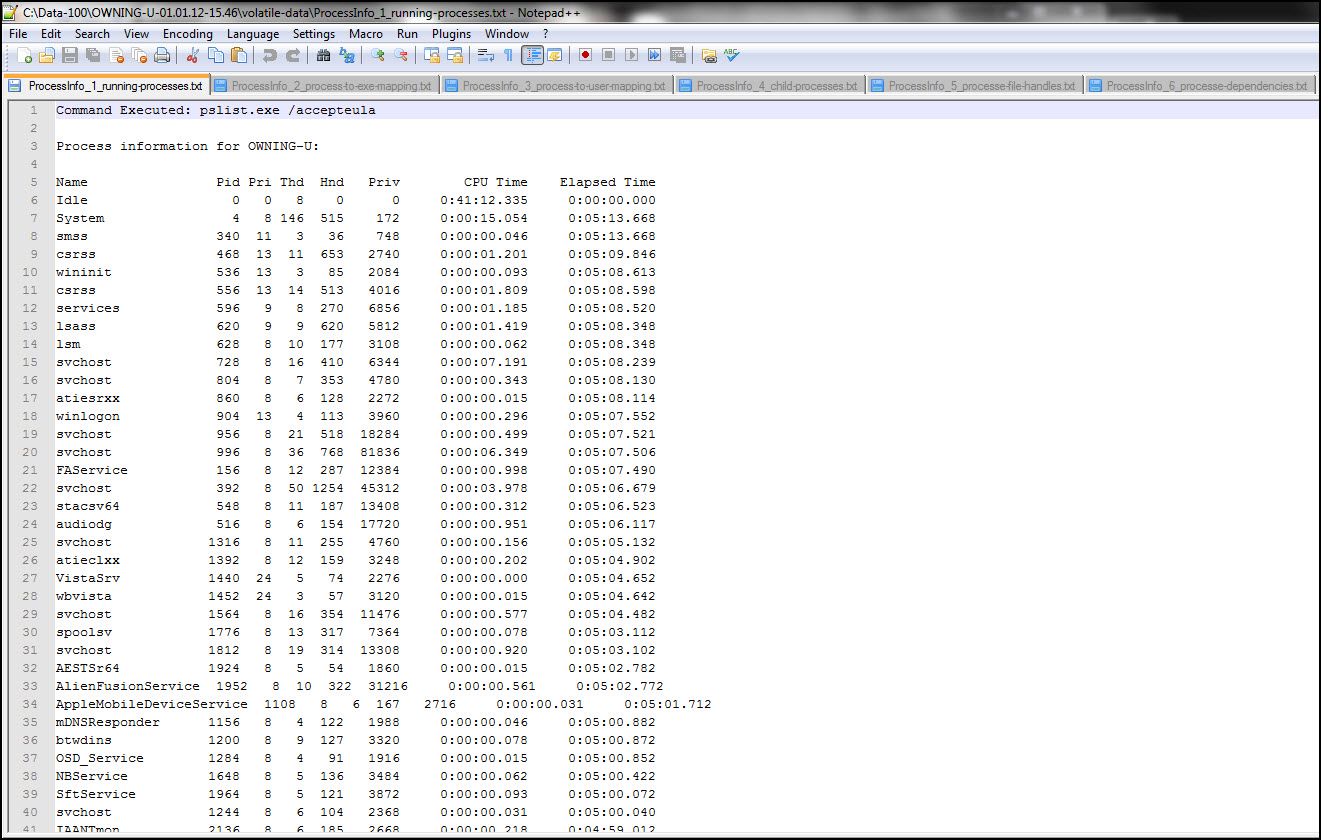
Journey Into Incident Response: Dual Purpose Volatile Data Collection Script
Recomendado para você
-
Get Spider Solitaire Collection Free - Microsoft Store28 março 2025
-
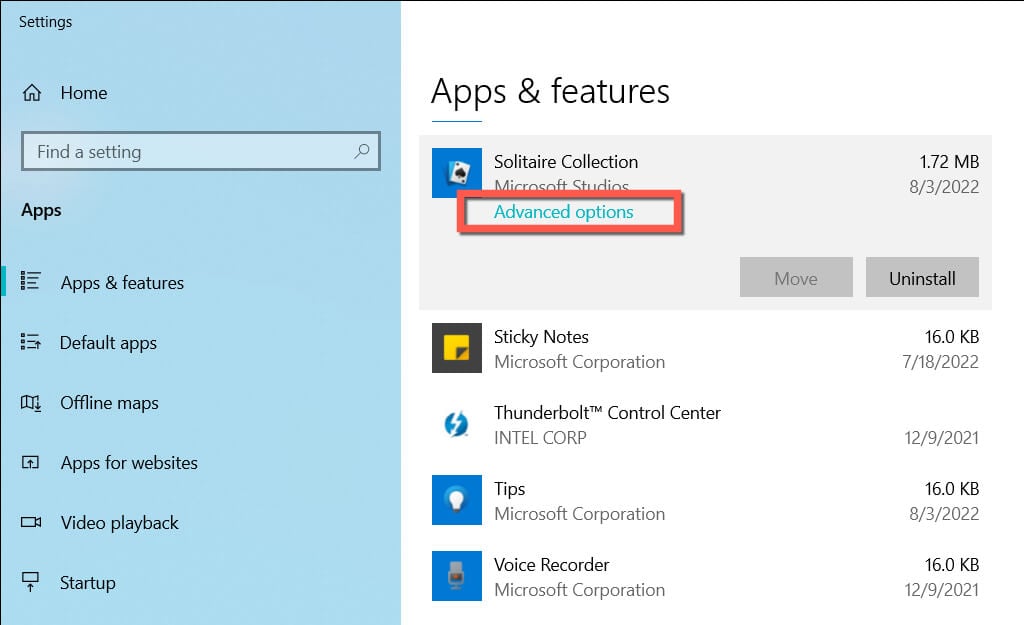 Microsoft Solitaire Collection Not Working in Windows? 10 Fixes to Try28 março 2025
Microsoft Solitaire Collection Not Working in Windows? 10 Fixes to Try28 março 2025 -
Fairway Solitaire - Card Game - Apps on Google Play28 março 2025
-
/pic1280420.jpg) Solitaire for Two, Board Game28 março 2025
Solitaire for Two, Board Game28 março 2025 -
 Fix: Google Docs Unable To Load File - MiniTool28 março 2025
Fix: Google Docs Unable To Load File - MiniTool28 março 2025 -
 The Solitaire Mystery28 março 2025
The Solitaire Mystery28 março 2025 -
 Palm Point and Palm Isles in Palm City28 março 2025
Palm Point and Palm Isles in Palm City28 março 2025 -
Solitaire NGO28 março 2025
-
 How to Uninstall Packages on Ubuntu {via Terminal or GUI}28 março 2025
How to Uninstall Packages on Ubuntu {via Terminal or GUI}28 março 2025 -
Bored? Close your eyes and tap anywhere on the perimeter of the28 março 2025
você pode gostar
-
 シャドウバースF 11月25日(土)放送分 #71 好きって気持ちは、最強だ!|アニメ/ヒーロー|見逃し無料配信はTVer!人気の動画見放題28 março 2025
シャドウバースF 11月25日(土)放送分 #71 好きって気持ちは、最強だ!|アニメ/ヒーロー|見逃し無料配信はTVer!人気の動画見放題28 março 2025 -
 Where to Find The BEST Free Custom Content For The Sims 428 março 2025
Where to Find The BEST Free Custom Content For The Sims 428 março 2025 -
 Hanyo no Yashahime, revelado o visual de Maroha – Tomodachi Nerd's28 março 2025
Hanyo no Yashahime, revelado o visual de Maroha – Tomodachi Nerd's28 março 2025 -
 Sirsen — Horror sans and Paps try out local foods The28 março 2025
Sirsen — Horror sans and Paps try out local foods The28 março 2025 -
 Assistir Initial D Final Stage Online completo28 março 2025
Assistir Initial D Final Stage Online completo28 março 2025 -
 Rurouni Kenshin: Shin Kyoto-Hen28 março 2025
Rurouni Kenshin: Shin Kyoto-Hen28 março 2025 -
Anime All Star - Top 10 Richest Mangaka 2022 10. George28 março 2025
-
 Últimas notas de FIFA 23 reveladas rumo ao lançamento28 março 2025
Últimas notas de FIFA 23 reveladas rumo ao lançamento28 março 2025 -
 Box com 6 Revistas Coquetel - Caça Palavra Fácil - Outros Livros - Magazine Luiza28 março 2025
Box com 6 Revistas Coquetel - Caça Palavra Fácil - Outros Livros - Magazine Luiza28 março 2025 -
 All the Things You Are, Oscar Hammerstein II & Jerome Kern, recorded by Joe Pass, jazz guitar solo, sheet music/songbook, out of print28 março 2025
All the Things You Are, Oscar Hammerstein II & Jerome Kern, recorded by Joe Pass, jazz guitar solo, sheet music/songbook, out of print28 março 2025



