Blog - Page 2 of 4 - Infosec
Por um escritor misterioso
Last updated 17 março 2025
No blog da Infosec Security você encontra matérias relacionadas a vulnerabilidades em redes, aplicações Web, aplicativos mobile, ransomware, dentre outros.

Enrich RBAC and ABAC with ProBAC, #infosec #security #BPM - BPI - The destination for everything process related

Submission Guidelines — InfoSec Writeups, by Sai Krishna Kothapalli

Chief Information Security Officer CISO Resume Examples 2023
Blog - Page 2 of 4 - Infosec
Beacon Completes More Projects

Protecting business interests with policies for it asset management it-toolkits

10 Information Security Policies Organizations Should Implement
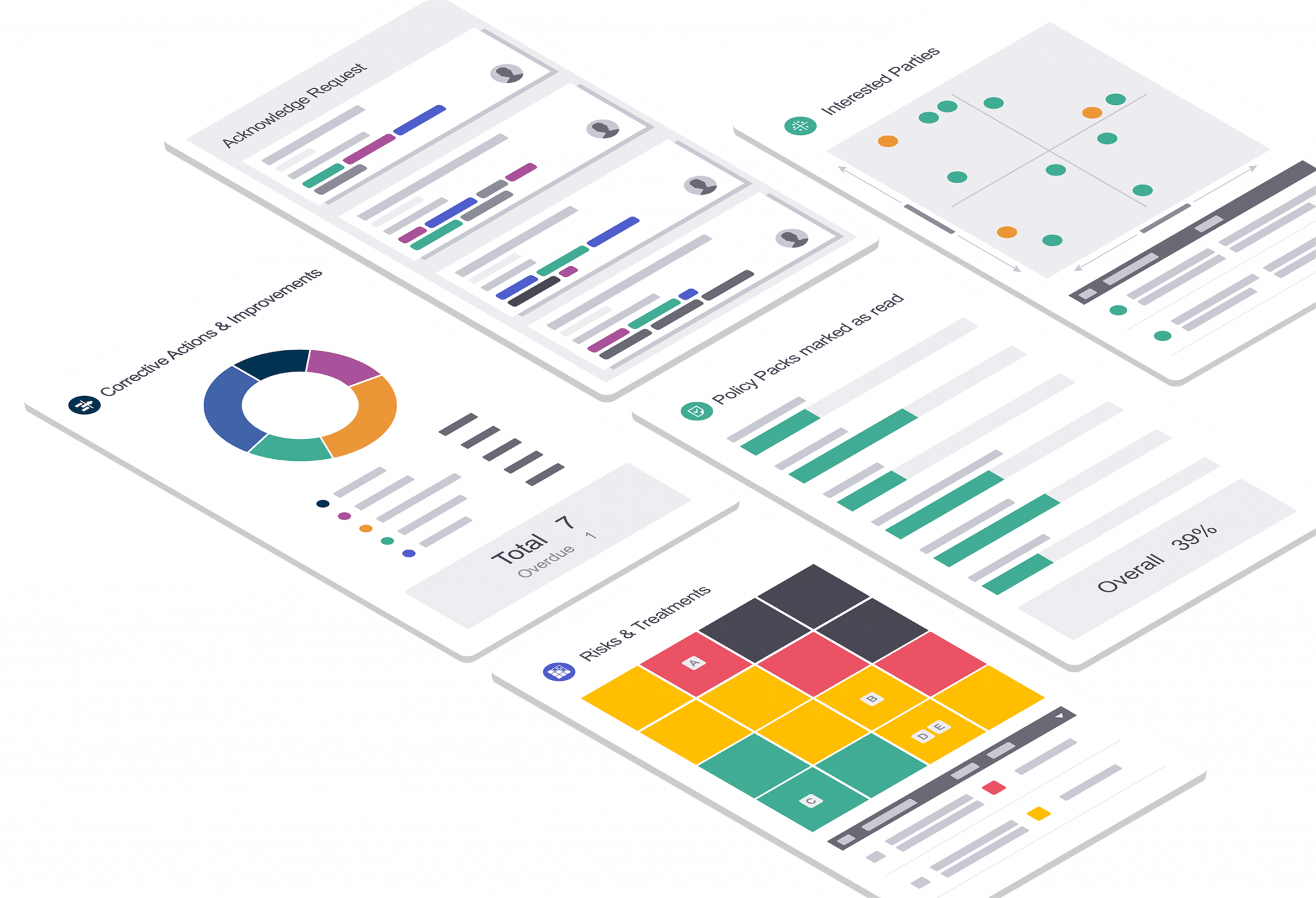
Information Security Management System (Pre-configured ISMS) Solution
The Significance of Key Risk Indicators in Organisations - ISC2 Blog

Professor Kevin Curran – Page 14 – Cybersecurity Communicator, Researcher & Professor at Ulster University
Ptrace Security GmbH on X: Virtualization Internals Part 1: Part 2: Part 3: Part 4: #Pentesting #CyberSecurity #Virtualization #Infosec

Approaches to Information Security Implementation

Blog Series: “Information Security, Compliance and Governance in the Cloud Era - Oversimplified” - Part #2

Guide on creating enterprise security policy – Tresorit

Use Gartner Cybersecurity Research & Insights to Develop Your Ideal Security Strategy
Recomendado para você
-
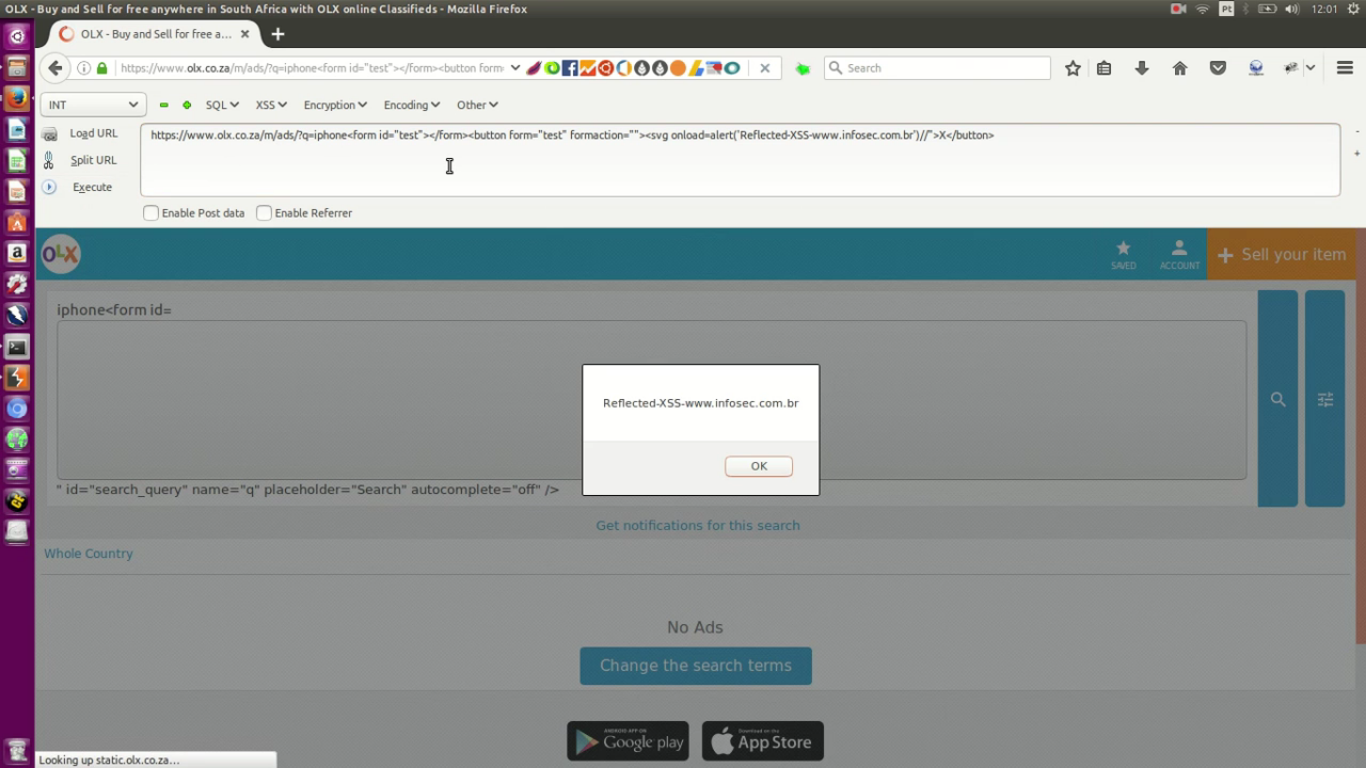
 OLX Developer Portal - Getting access to API17 março 2025
OLX Developer Portal - Getting access to API17 março 2025 -
 How to create OLX account without phone number - SMS-Man Blog17 março 2025
How to create OLX account without phone number - SMS-Man Blog17 março 2025 -
 Create Classified Website By OLX Like WordPress Theme17 março 2025
Create Classified Website By OLX Like WordPress Theme17 março 2025 -
 OLX Autos (Dealers Only) on the App Store17 março 2025
OLX Autos (Dealers Only) on the App Store17 março 2025 -
 How to delete my OLX account? - AccountDeleters17 março 2025
How to delete my OLX account? - AccountDeleters17 março 2025 -
 olxgroup.okta-emea.com - Olxgroup Okta Emea17 março 2025
olxgroup.okta-emea.com - Olxgroup Okta Emea17 março 2025 -
 OLX Egypt offers its Users Tips to Buy and Sell Safely On its Platform17 março 2025
OLX Egypt offers its Users Tips to Buy and Sell Safely On its Platform17 março 2025 -
Musa Tyagi - Dip Associate - Randstad17 março 2025
-
www.tokoaldhieprakerja.com17 março 2025
-
 Determining the Market Price of Old Vehicles Using Python17 março 2025
Determining the Market Price of Old Vehicles Using Python17 março 2025
você pode gostar
-
 Quebra Cabeça 2000 Peças Dinossauros - Bumerang Brinquedos17 março 2025
Quebra Cabeça 2000 Peças Dinossauros - Bumerang Brinquedos17 março 2025 -
 Worlds 2021 Tudo sobre o Mundial de League of Legends - Canaltech17 março 2025
Worlds 2021 Tudo sobre o Mundial de League of Legends - Canaltech17 março 2025 -
 DreamWorks All-Star Kart Racing, jogo de corrida com Shrek é anunciado17 março 2025
DreamWorks All-Star Kart Racing, jogo de corrida com Shrek é anunciado17 março 2025 -
 MKWarehouse: Mortal Kombat: Baraka17 março 2025
MKWarehouse: Mortal Kombat: Baraka17 março 2025 -
 Dvd screensaver 1 Project by Diagnostic Explanation17 março 2025
Dvd screensaver 1 Project by Diagnostic Explanation17 março 2025 -
 Oblee Marketplace Kit Digital Dragon Ball Completo17 março 2025
Oblee Marketplace Kit Digital Dragon Ball Completo17 março 2025 -
 Play Nintendo 64 Banjo-Kazooie Fort Fun V4.0 Online in your17 março 2025
Play Nintendo 64 Banjo-Kazooie Fort Fun V4.0 Online in your17 março 2025 -
 LEVANTAMENTO TERRA - O exercício que pega tudo!17 março 2025
LEVANTAMENTO TERRA - O exercício que pega tudo!17 março 2025 -
 ACDC RAG Yami Kawaii Punk Menhera-chan Leg Warmers - Pink – Blippo17 março 2025
ACDC RAG Yami Kawaii Punk Menhera-chan Leg Warmers - Pink – Blippo17 março 2025 -
 minecraft in google slides|TikTok Search17 março 2025
minecraft in google slides|TikTok Search17 março 2025