Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Last updated 28 março 2025

In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

Advanced Apple Debugging & Reverse Engineering
Access Our Reverse Engineering
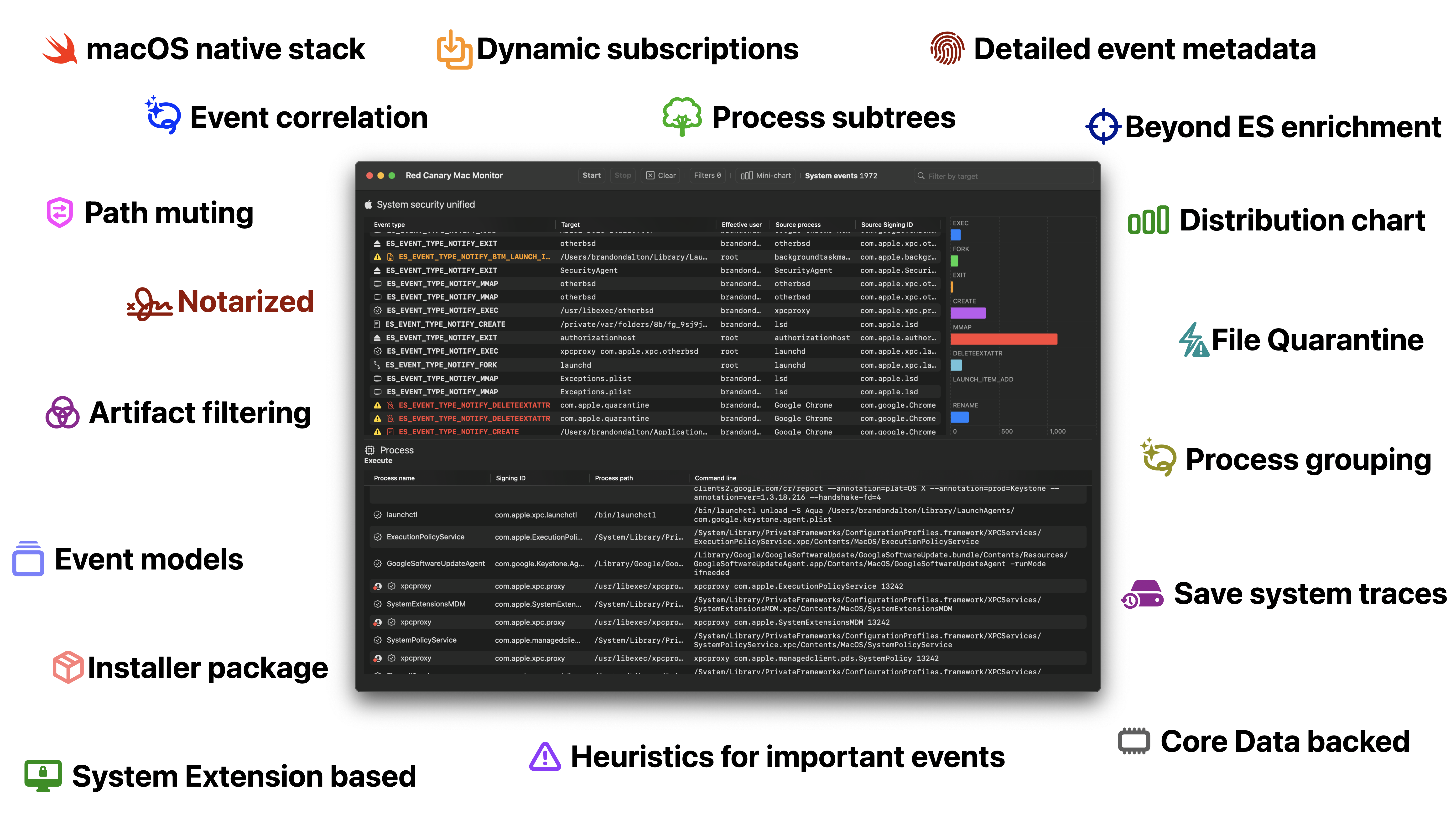
Red Canary Mac Monitor - An Advanced, Stand-Alone System Monitoring Tool Tailor-Made For macOS Security Research

Advanced Apple Debugging & Reverse Engineering, Chapter 1: Getting Started

Kodeco Learn iOS, Android & Flutter

HACKER SUMMER CAMP 2023 GUIDES — Part Nine: DEFCON 31, by DCG 201

The missing guide to debug third party apps on iOS 12+, by Felipe Cavalcanti
Future Internet, Free Full-Text

Mastering Malware Analysis
iOS Reverse Engineering - Debugging and Tracing with LLDB
Recomendado para você
-
rbxgum.com Traffic Analytics, Ranking Stats & Tech Stack28 março 2025
-
 What is the difference between Robux and Tix? - Quora28 março 2025
What is the difference between Robux and Tix? - Quora28 março 2025 -
LilyGia on FreshCut28 março 2025
-
 New rbx.gum Promocode Aug 4,2022 (hurry before expired) #shorts28 março 2025
New rbx.gum Promocode Aug 4,2022 (hurry before expired) #shorts28 março 2025 -
coinEZ/cryptocurrencies.json at main · Purukitto/coinEZ · GitHub28 março 2025
-
Cheeks Joy Blush Face Roblox Item - Rolimon's28 março 2025
-
easy rbx|TikTok Search28 março 2025
-
 Seed Junky Home28 março 2025
Seed Junky Home28 março 2025 -
Blonde Curly Pigtails Roblox Item - Rolimon's28 março 2025
-
Fer99928 março 2025
você pode gostar
-
Will lemmings fall off climate change cliff?28 março 2025
-
Action figure Goku Deus Super Saiyajin Dragon ball estatua28 março 2025
-
 Quem é o pai dos oligarcas que ofereceu emprego a Putin e agora28 março 2025
Quem é o pai dos oligarcas que ofereceu emprego a Putin e agora28 março 2025 -
Y - Alphabet Lore, Special Alphabet Lore Wiki28 março 2025
-
 Server Gta Rp - DFG28 março 2025
Server Gta Rp - DFG28 março 2025 -
Peppa Pig - Dublado - Português - Mistérios [HD] - Vídeo Dailymotion28 março 2025
-
 Spy x Family - Page 3 of 1128 março 2025
Spy x Family - Page 3 of 1128 março 2025 -
 VastLight - النّور الشّاسع on X: The official Sonic.EXE: The28 março 2025
VastLight - النّور الشّاسع on X: The official Sonic.EXE: The28 março 2025 -
 Playing the English by Nikolaos Ntirlis, Opening chess book by28 março 2025
Playing the English by Nikolaos Ntirlis, Opening chess book by28 março 2025 -
Tommy Hilfiger Lahyla Toe-loop Sandals, Created For Macy's Women's Shoes In Yellow28 março 2025




