Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 21 março 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

The UTI Emergency Kit

Microsoft Defender Attack Surface Reduction recommendations

Loophole Abuse - TV Tropes

A contractile injection system is required for developmentally regulated cell death in Streptomyces coelicolor

exception processing message 0xc0000005 - unexpected parameters - Microsoft Community
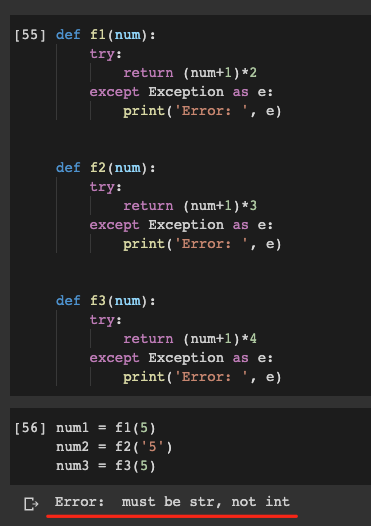
Do Not Abuse Try Except In Python, by Christopher Tao
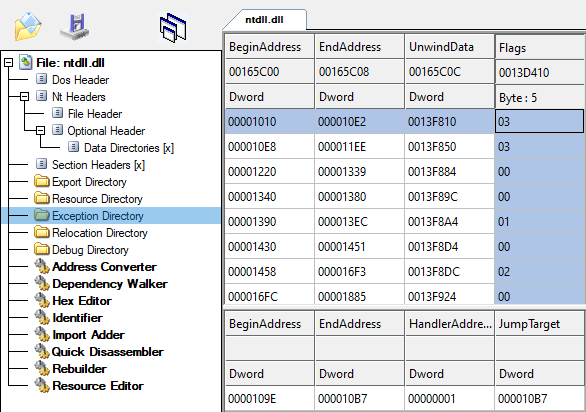
Abusing Exceptions for Code Execution, Part 1

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic
Blindside: A New Technique for EDR Evasion with Hardware Breakpoints - Cymulate

Code of Ethics for Government Services Poster
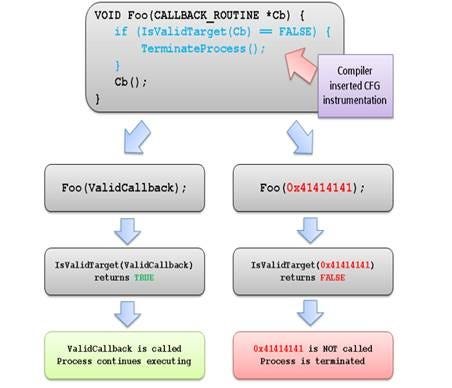
Exploitation Protections From Old To Bleeding Edge pt 1, by Edward Amaral Toledano, stolabs

mTLS: When certificate authentication is done wrong - The GitHub Blog

Hackers Exploit Windows Policy Loophole to Forge Kernel-Mode Driver Signatures
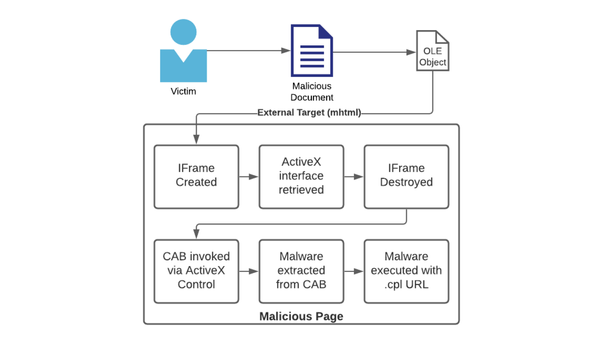
Abusing Exceptions for Code Execution, Part 1

Abusing Exceptions for Code Execution, Part 1
Recomendado para você
-
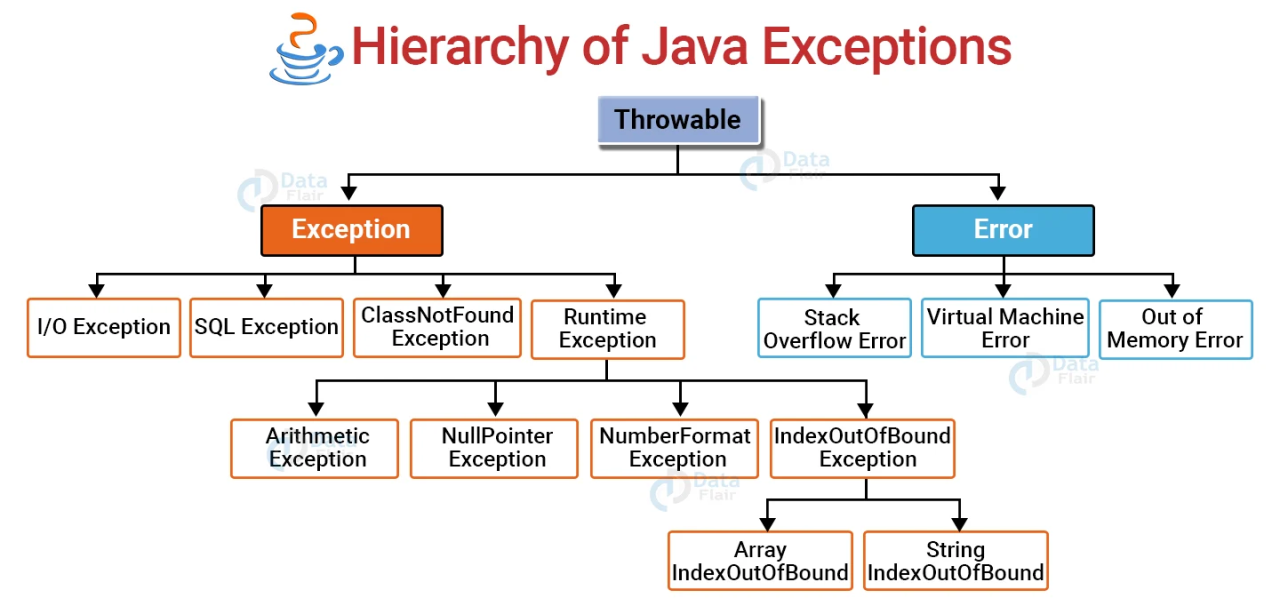
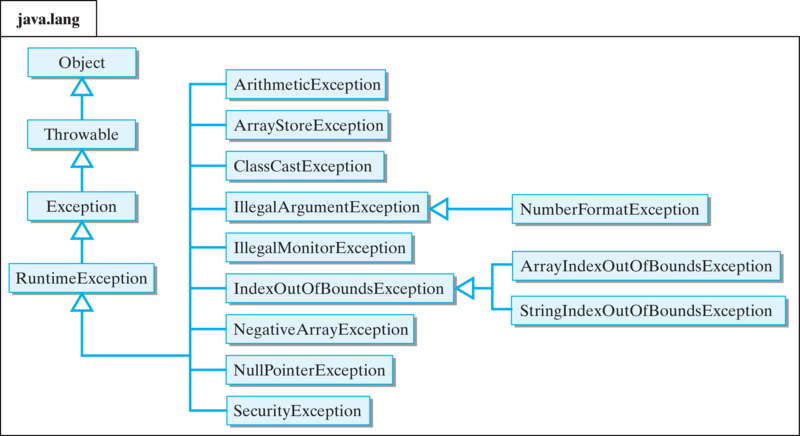 Java's Exception Hierarchy21 março 2025
Java's Exception Hierarchy21 março 2025 -
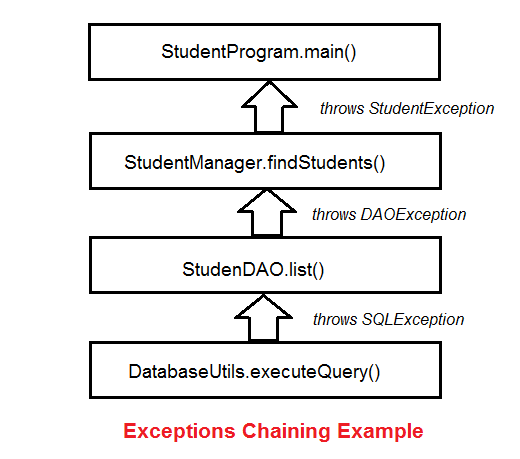 Understanding Java Exception Chaining with Code Examples21 março 2025
Understanding Java Exception Chaining with Code Examples21 março 2025 -
 Handling Exceptions in Java21 março 2025
Handling Exceptions in Java21 março 2025 -
Python Exceptions21 março 2025
-
🚀Mastering Error and Exception Handling: A Deep Dive into Reliable Code Execution 💻✨21 março 2025
-
 Exception Handling Process and Internal Audit – Risk and Control: Ideas for a better tomorrow21 março 2025
Exception Handling Process and Internal Audit – Risk and Control: Ideas for a better tomorrow21 março 2025 -
 Auditing Exceptions and How They Might Impact Your SOC Reports21 março 2025
Auditing Exceptions and How They Might Impact Your SOC Reports21 março 2025 -
 Java Exception Rule Book – Nico de Wet scalable and robust distributed systems21 março 2025
Java Exception Rule Book – Nico de Wet scalable and robust distributed systems21 março 2025 -
 No Exceptions Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime21 março 2025
No Exceptions Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime21 março 2025 -
 CIS 35A: Introduction to Java Programming21 março 2025
CIS 35A: Introduction to Java Programming21 março 2025
você pode gostar
-
 Assistir Dungeon ni Deai wo Motomeru no wa Machigatteiru Darou ka III 3° temporada - Episódio 04 Online - Download & Assistir Online! - AnimesTC21 março 2025
Assistir Dungeon ni Deai wo Motomeru no wa Machigatteiru Darou ka III 3° temporada - Episódio 04 Online - Download & Assistir Online! - AnimesTC21 março 2025 -
 Aparelho Equipamento Supino Inclinado 45° 3 Rei do Fitness21 março 2025
Aparelho Equipamento Supino Inclinado 45° 3 Rei do Fitness21 março 2025 -
 Melhor jogo de gato pc maiô crianças21 março 2025
Melhor jogo de gato pc maiô crianças21 março 2025 -
 Xbox Cloud Gaming (xCloud) on iOS review: How well does it stream21 março 2025
Xbox Cloud Gaming (xCloud) on iOS review: How well does it stream21 março 2025 -
 Hunter x Hunter, Vol. 34 by Yoshihiro Togashi, Paperback21 março 2025
Hunter x Hunter, Vol. 34 by Yoshihiro Togashi, Paperback21 março 2025 -
 Escape Games Play Online at Coolmath Games21 março 2025
Escape Games Play Online at Coolmath Games21 março 2025 -
 The Greatest in the World!: Volume 121 março 2025
The Greatest in the World!: Volume 121 março 2025 -
 Roblox Rainbow Friends Jogo Boneca Rainbow Vilão Rainbow Amigos21 março 2025
Roblox Rainbow Friends Jogo Boneca Rainbow Vilão Rainbow Amigos21 março 2025 -
 Gran Turismo 4 PS2 PlayStation 2 Game + Manual PAL21 março 2025
Gran Turismo 4 PS2 PlayStation 2 Game + Manual PAL21 março 2025 -
 Music tracks, songs, playlists tagged alighieri on SoundCloud21 março 2025
Music tracks, songs, playlists tagged alighieri on SoundCloud21 março 2025