Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Last updated 28 março 2025

Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..

How OpenBullet is used to attack websites, and how to block it.
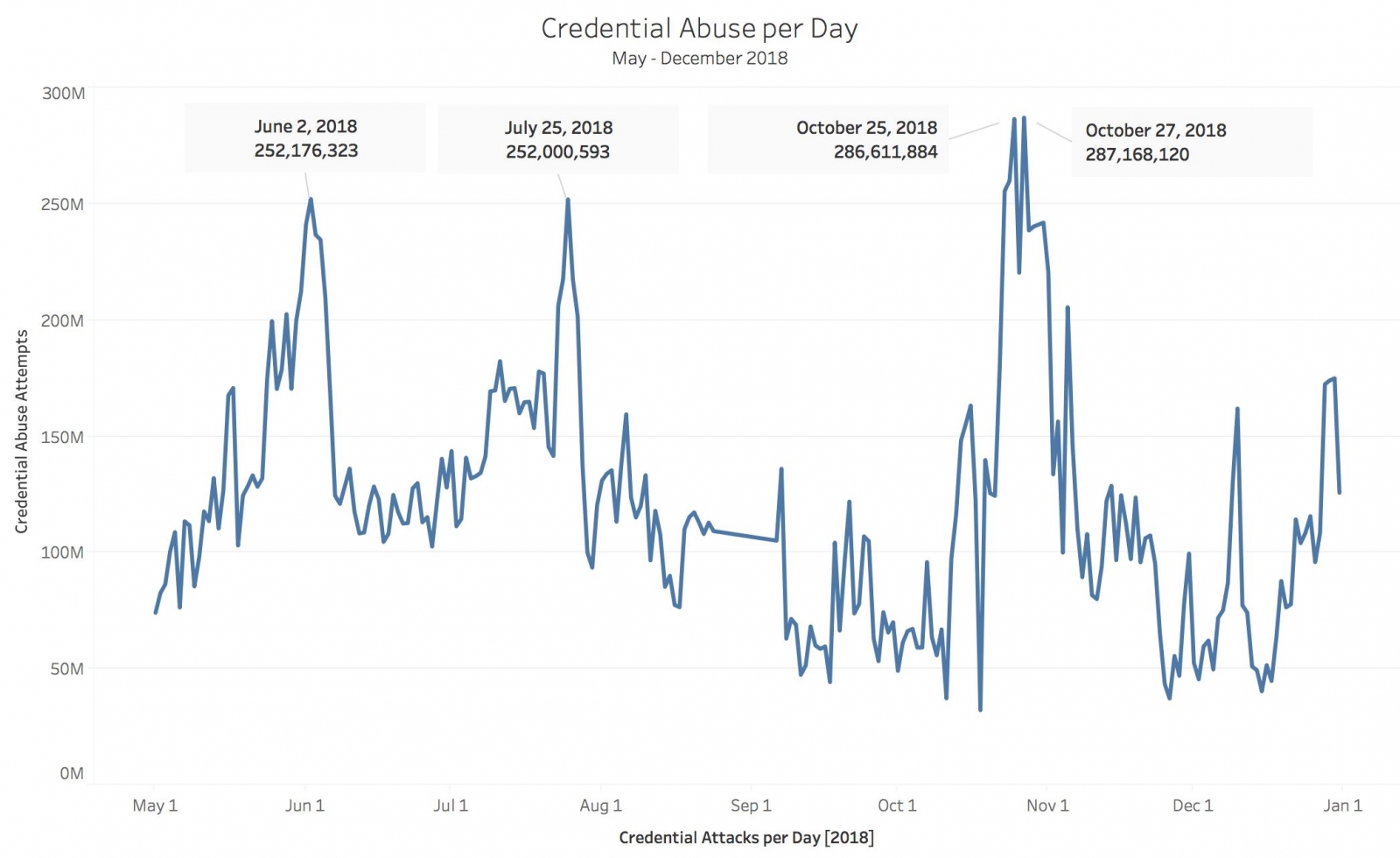
The Anatomy of Highly Profitable Credential Stuffing Attacks
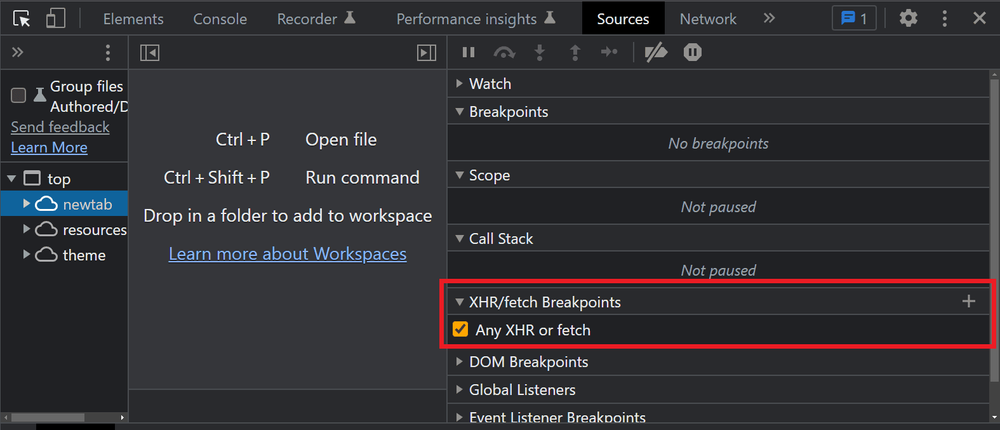
How to Bypass Cloudflare in 2023: The 8 Best Methods - ZenRows
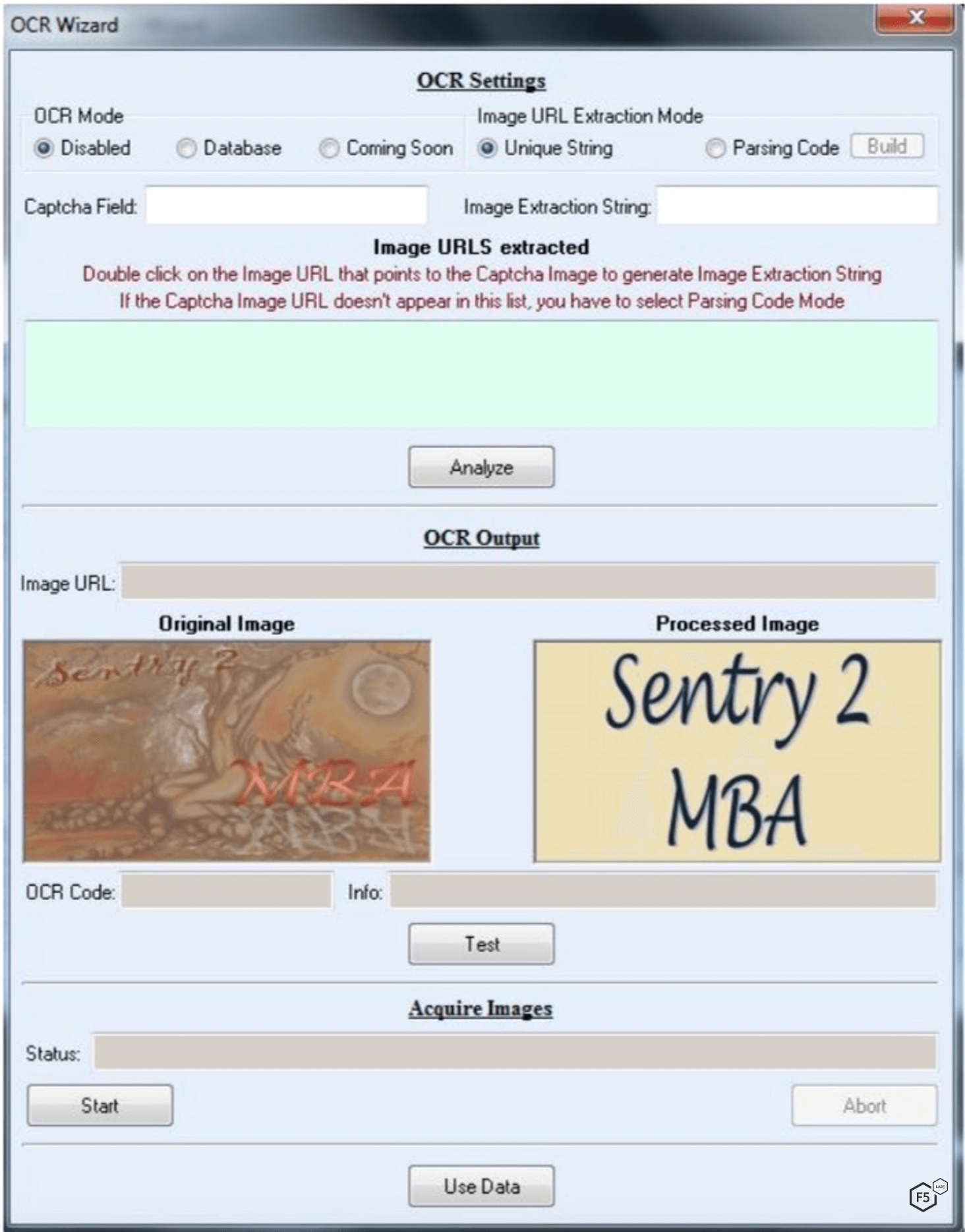
How Credential Stuffing Bots Bypass Defenses
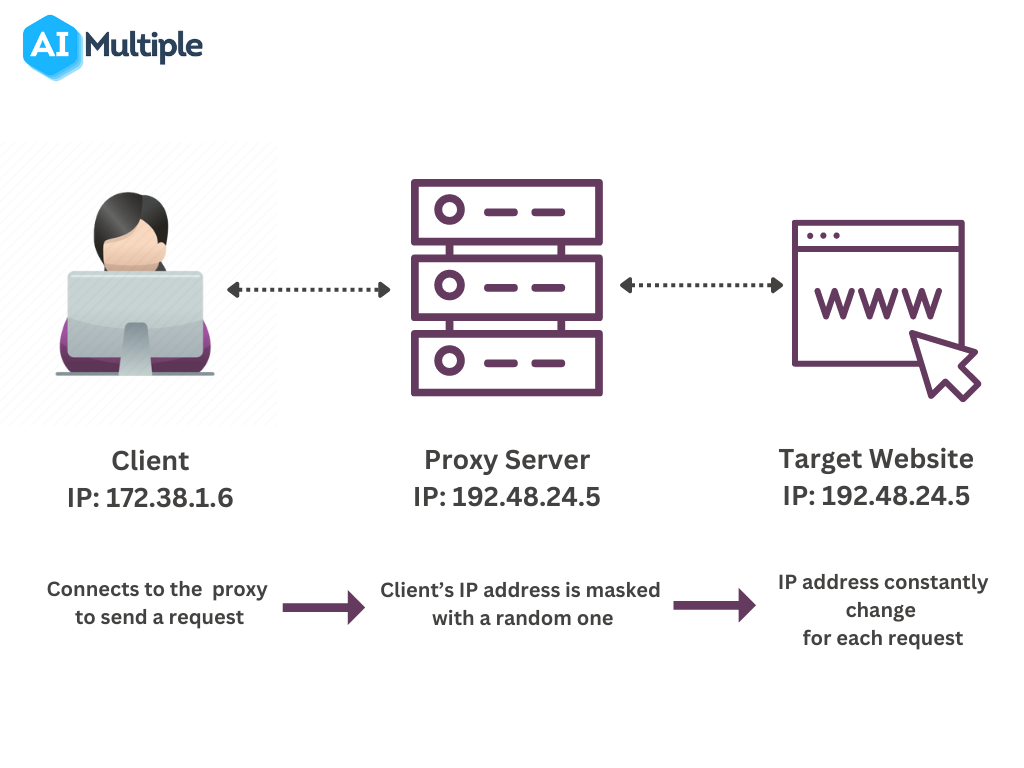
The Ultimate Guide to Avoiding CAPTCHAs in Web Scraping
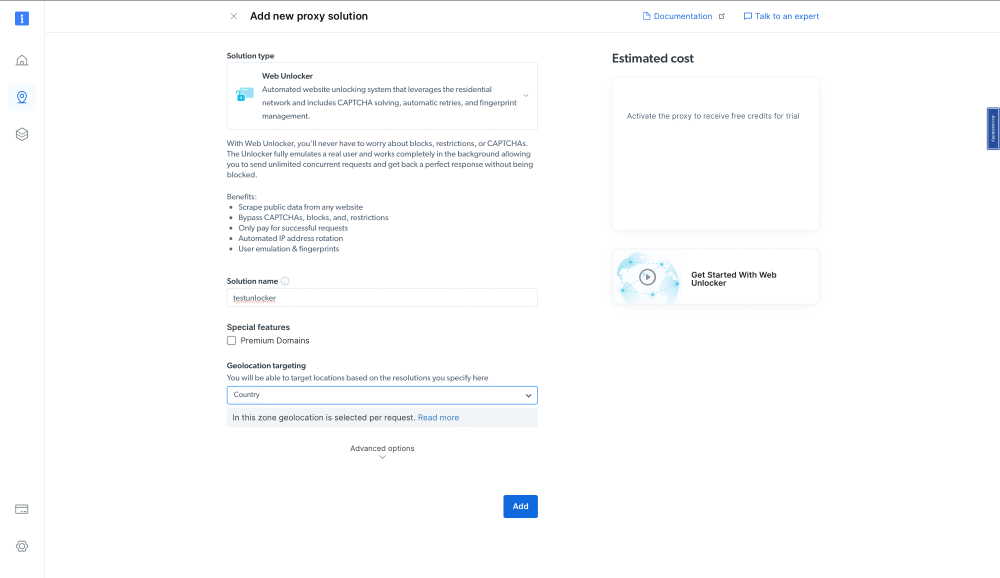
How to Bypass CAPTCHA Using Web Unlocker

How Credential Stuffing is Evolving - PasswordsCon 2019

Penetration Testing Attacks — Credential Stuffing, EC Council, by EC-Council Group
The 5 Stages of a Credential Stuffing Attack

Credential Stuffing Tools and Techniques, Part 1
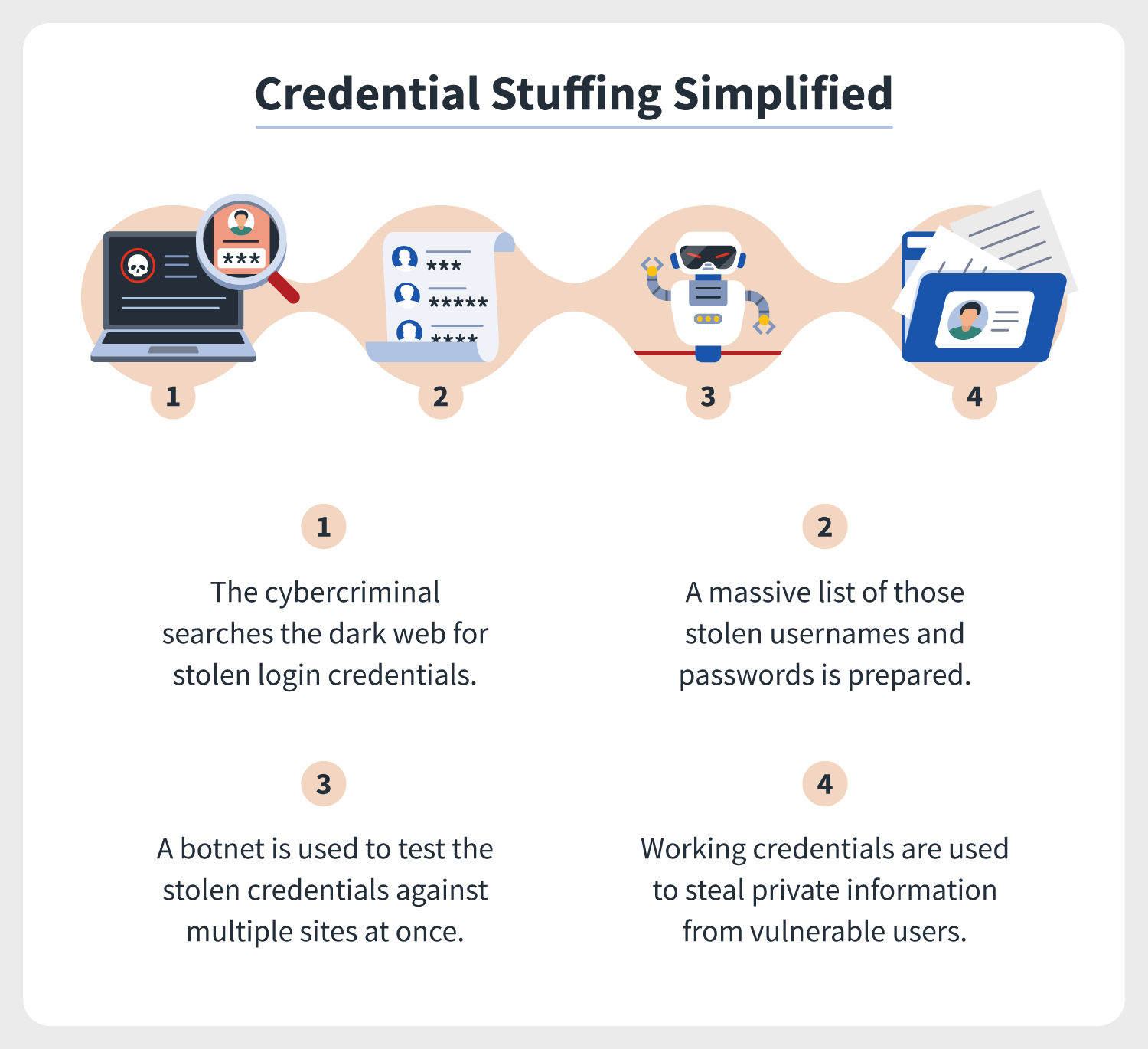
Credential stuffing simplified + attack protection tips
Recomendado para você
-
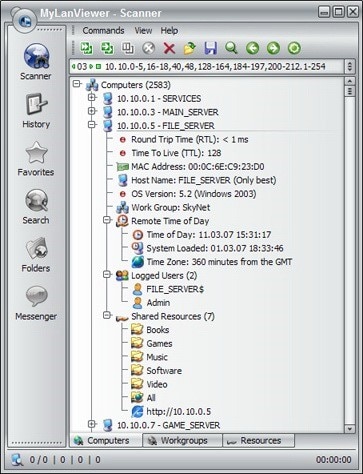 The 7 Best IP Address Trackers - DNSstuff28 março 2025
The 7 Best IP Address Trackers - DNSstuff28 março 2025 -
Is my IP address safe on Discord? - Quora28 março 2025
-
 DW IP Finder28 março 2025
DW IP Finder28 março 2025 -
 IP Address Tracker - IP Tracker (Free Trial)28 março 2025
IP Address Tracker - IP Tracker (Free Trial)28 março 2025 -
 Excel Add-In28 março 2025
Excel Add-In28 março 2025 -
 Analysing a Widespread Microsoft 365 Credential Harvesting Campaign28 março 2025
Analysing a Widespread Microsoft 365 Credential Harvesting Campaign28 março 2025 -
 Cybersecurity Search Engine28 março 2025
Cybersecurity Search Engine28 março 2025 -
 IP Checker28 março 2025
IP Checker28 março 2025 -
![4 Ways in 2023] How to Find Someone's IP on Instagram?](https://images.imyfone.com/famiguarden/assets/article/monitor/ip-address-lookup.png) 4 Ways in 2023] How to Find Someone's IP on Instagram?28 março 2025
4 Ways in 2023] How to Find Someone's IP on Instagram?28 março 2025 -
 Discord IP Resolver How to Pull IP on Discord? [2023 Update28 março 2025
Discord IP Resolver How to Pull IP on Discord? [2023 Update28 março 2025
você pode gostar
-
Mario Plays Roblox, The SMG4/GLITCH Wiki28 março 2025
-
 Two New Mario Games Are Coming To The Nintendo Switch28 março 2025
Two New Mario Games Are Coming To The Nintendo Switch28 março 2025 -
 OpenDream - initial d anime 1 0 8 0 p28 março 2025
OpenDream - initial d anime 1 0 8 0 p28 março 2025 -
 Trajes Kawaii - Shoptery28 março 2025
Trajes Kawaii - Shoptery28 março 2025 -
 images./img/ss/mods/5f29b7fdc835d.jp28 março 2025
images./img/ss/mods/5f29b7fdc835d.jp28 março 2025 -
 shindou hikaru and fujiwara no sai (hikaru no go) drawn by kyakya28 março 2025
shindou hikaru and fujiwara no sai (hikaru no go) drawn by kyakya28 março 2025 -
 Yakuza Kiwami Bakamitai (Dame Da Ne) -Sorrow- [English & Spanish28 março 2025
Yakuza Kiwami Bakamitai (Dame Da Ne) -Sorrow- [English & Spanish28 março 2025 -
 Harriet, The Maze Runner Wiki28 março 2025
Harriet, The Maze Runner Wiki28 março 2025 -
 Subway Surfers 2022 Year in Review28 março 2025
Subway Surfers 2022 Year in Review28 março 2025 -
Site para saber os jogos em promoção na Steam. #steam #steamgames28 março 2025

